As I was learning Cyber Threat Intelligence I chose Open CTI as demo tool while taking this path, and these were my installation steps which I followed while configuring it. In this document I will show steps used to install it by using docker image and manage them using docker swarm and portainer. I installed the Open CTI in two ubuntu machines where by one was used as manager and the second one as worker.
This document shows all necessary steps used to install it by using docker image and mange them by using docker swarm and portainer .
All steps will be shown in ubuntu machines where by one has been used as manager and the second one as worker.
This setup has been implemented in vmware machine, so the first prerequisites should be installed in both manager and worker
Below are the steps used to perform the task:
Install a single ubuntu machine in vmware followed by all the shared requirements as follows:-
Update repository
1
gemstone@hashghost:~$ sudo apt-get update -y
Install Certificate preparation for docker
1
2
3
4
5
6
gemstone@hashghost:~$ sudo apt-get install -y \
apt-transport-https \
ca-certificates \
curl \
gnupg-agent \
software-properties-common
Adding docker GPG key
1
gemstone@hashghost:~$ curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
Check the fingerprint of the key
1
gemstone@hashghost:~$ sudo apt-key fingerprint 0EBFCD88
Adding docker repository in ubuntu machine
1
2
3
4
gemstone@hashghost:~$ sudo add-apt-repository \
"deb [arch=amd64] https://download.docker.com/linux/ubuntu \
$(lsb_release -cs) \
stable"
Update repositories
1
gemstone@hashghost:~$ sudo apt-get update -y
Install docker and docker composer
1
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-compose
Verify if docker has been successfully installed
1
gemstone@hashghost:~$ sudo docker version
Modify machine user and add the user to docker group
1
gemstone@hashghost:~$ sudo usermod -aG docker $USER
Shutting down the machine.
1
gemstone@hashghost:~$ shutdown now
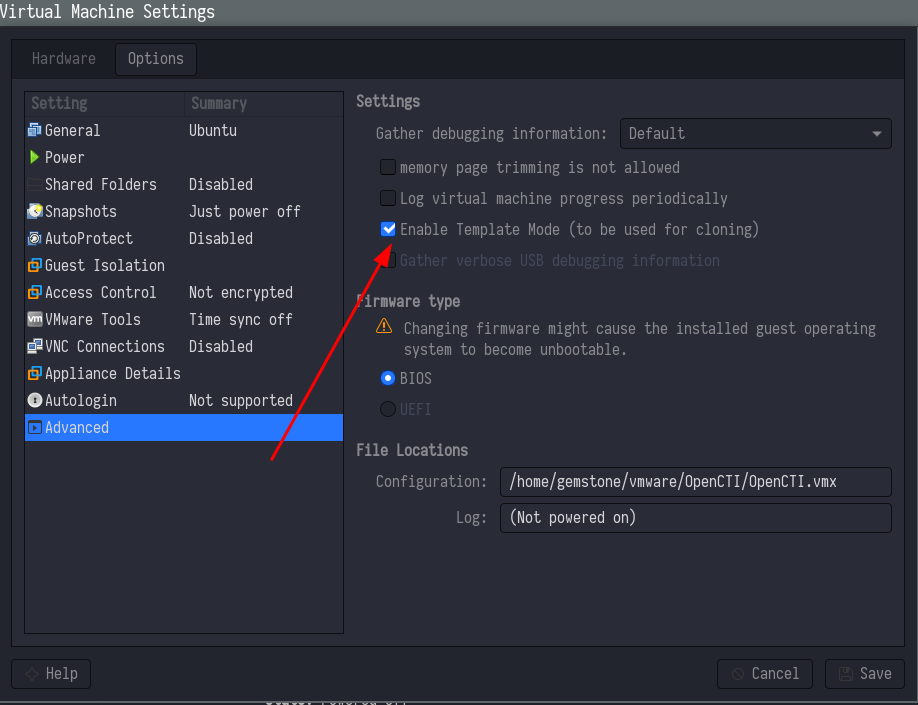
In this documentation OpenCTI is installed in virtual machine then all prerequisites needed for both manager and worker were already installed, then create a template to allow cloning of machines from ubuntu machine. Cloning will help to merge as many as possible machines with pre installed prerequisites.
This process is shown as follows:-
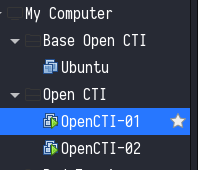
After enabled template mode clone two machines from ubuntu and the first machine name it as OpenCTI-01 which will be used as manager and the second one name it as OpenCTI-02 which will be used as worker machine, all these information can be seen here below:-
Master
Starting with master machine, Start docker swarm and advertise the ip address of master user.
1
gemstone@opencti-01:~$ docker swarm init --advertise-addr 172.16.34.131
After the above command output will be the command to join the swarm with token and port number.
Worker
This command is the output from master machine which allows worker’s machine to join the swarm for management.
1
gemstone@opencti-02:~$ docker swarm join --token SWMTKN-1-1k179pcofdol52ia0yby85x5sm07wp93ioz95vp4j156uuv9i8-dfynlzfru7v3mlo6q7pavdvf6 172.16.34.131:2377
Install Portainer
Portainer is used to manage docker image by providing graphical interface which fetch log data from machines with portainer.
1
2
mkdir -p /opt/portainer && cd /opt/portainer
curl -L https://downloads.portainer.io/portainer-agent-stack.yml -o portainer-agent-stack.yml
The above commands will create new directory /opt/portainer navigate to it and then downloading portainer-agent-stack.yml and save it with the same name. This file will have the following outputs:- Command
1
gemstone@opencti-01:/opt/portainer$ cat portainer-agent-stack.yml
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
version: '3.2'
services:
agent:
image: portainer/agent:2.11.1
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- /var/lib/docker/volumes:/var/lib/docker/volumes
networks:
- agent_network
deploy:
mode: global
placement:
constraints: [node.platform.os == linux]
portainer:
image: portainer/portainer-ce:2.11.1
command: -H tcp://tasks.agent:9001 --tlsskipverify
ports:
- "9443:9443"
- "19000:9000"
- "18000:8000"
volumes:
- portainer_data:/data
networks:
- agent_network
deploy:
mode: replicated
replicas: 1
placement:
constraints: [node.role == manager]
networks:
agent_network:
driver: overlay
attachable: true
volumes:
portainer_data:
There is port numbers which portainer will use them during access, these ports are common and should changed to avoid any collision.
1
2
- "9000:9000"
- "8000:8000"
Add this one as shown below:-
1
2
- "19000:9000"
- "18000:8000"
After all the installation you be able to access portainer in web browser by using manager ip which is http://172.16.34.131 with port number 19000 . At a time I document this I was already created an account so it claimed for password because I am known user to it.
Portainer will start to count all the images which are up and up to this stage its about 5 containers but there is no opencti Then add new stack and named it as opencti .
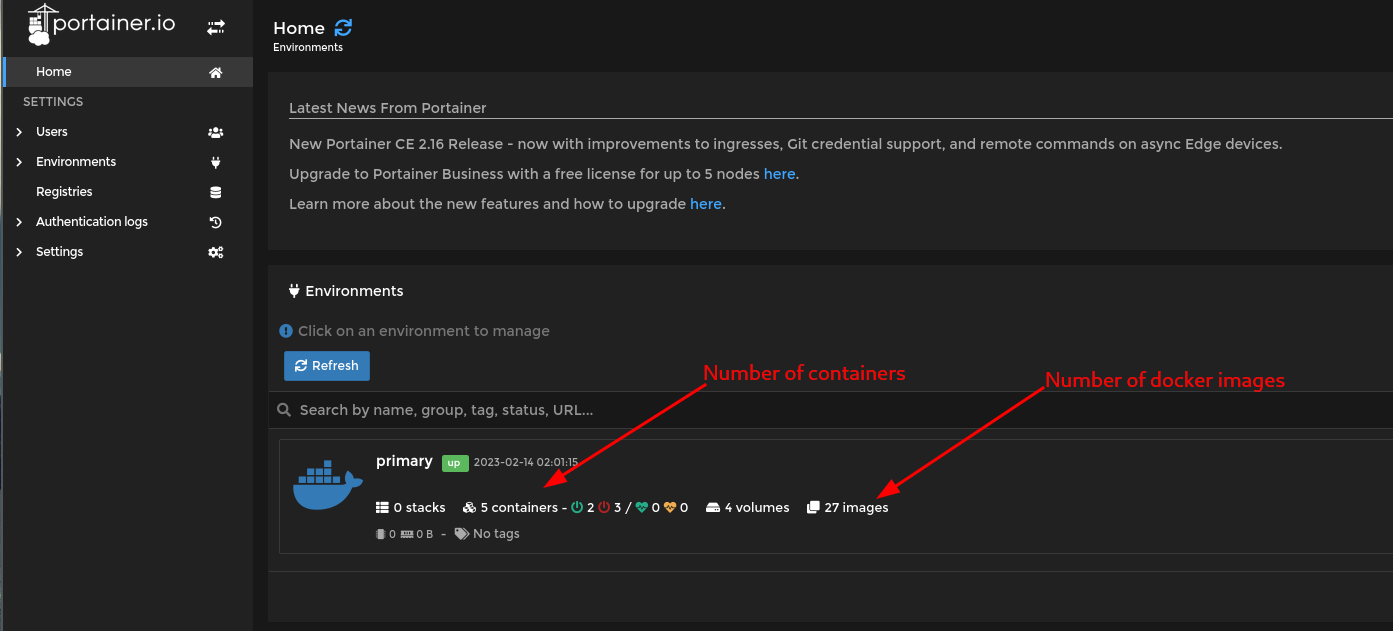
Since we were using portainer then it is clearly that we have to install the docker version of opencti. Visited official github page of opencti and grab the .yml file and add it to the portainer also and add some connectors which opencti will use to collect data from as shown below:
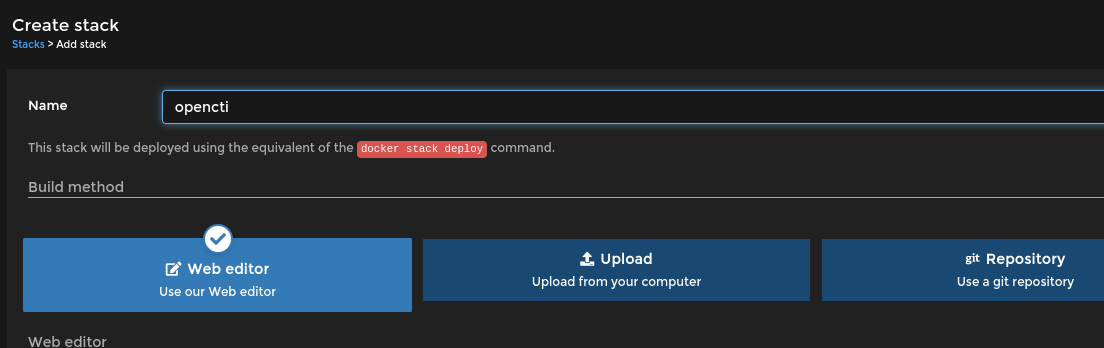
Adding configuration file with connectors API keys.
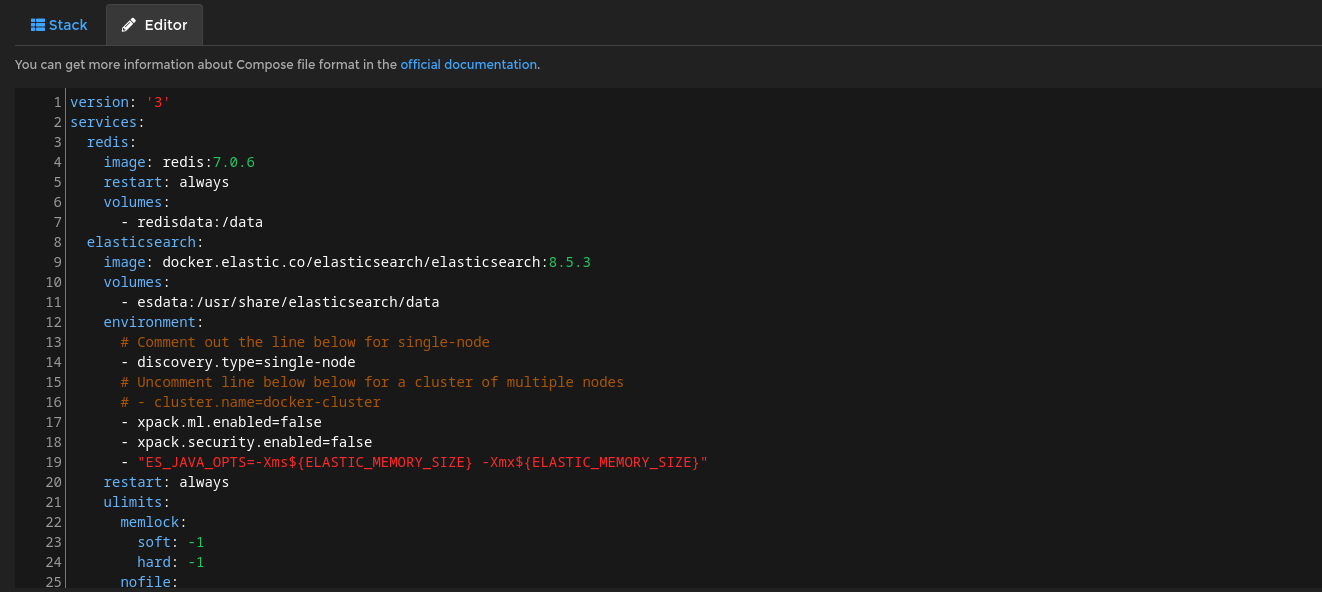
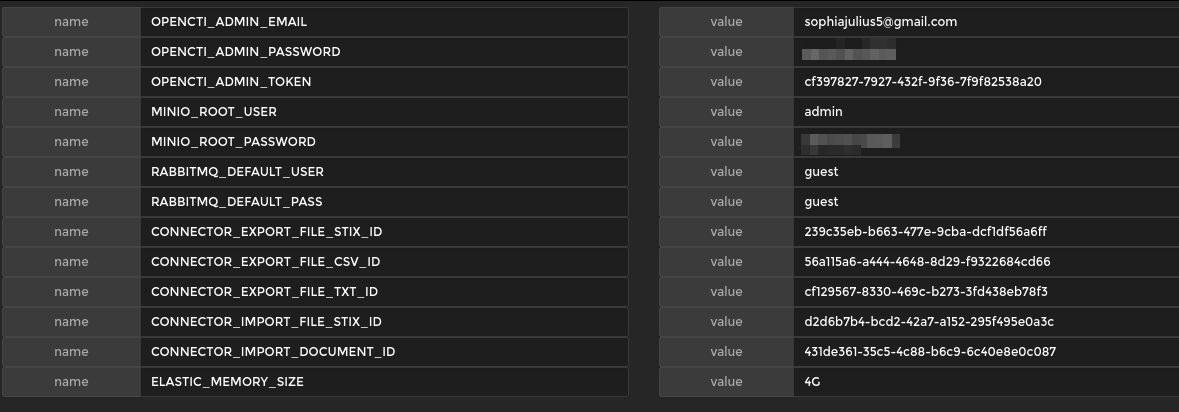
Also add the environment variables which contains some credentials for the opencti login also the sample of these variables from opencti GitHub page as shown below:-
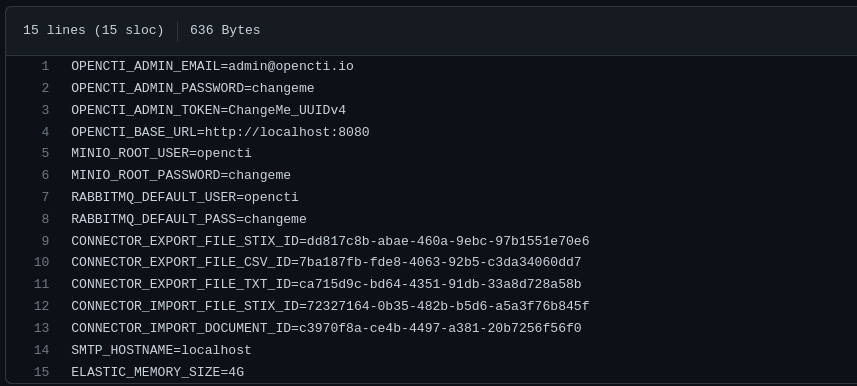
After adding the environment it will be seen as follows:-
After adding the configuration file and environment variables then deploy machine and stack number was improved to two which are opencti stack and portainer, also number of containers increased.
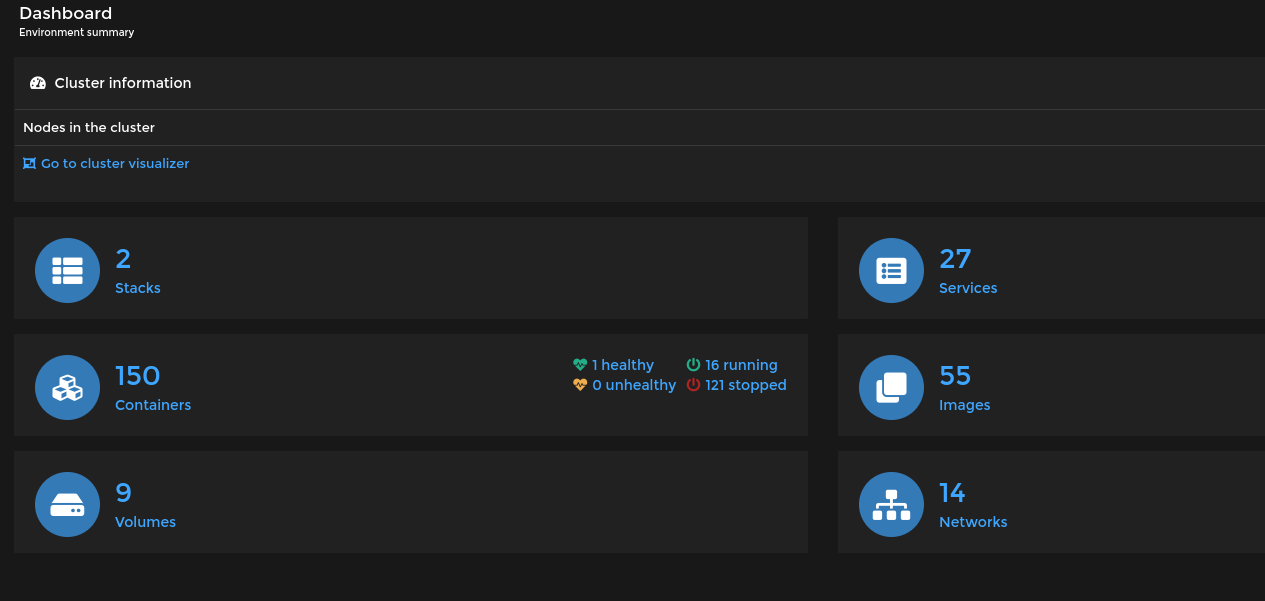
Stack names after adding portainer
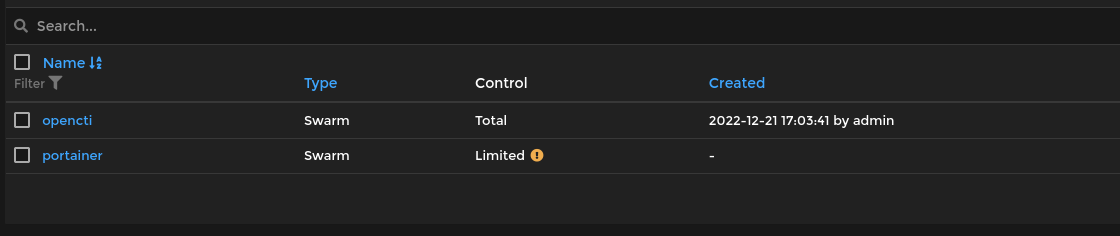
Deploying OpenCTI
After adding the stack and some connectors in portainer then click deploy stack and wait for some times then access opencti with manager ip again but this time with another port number which is 8080
Dashboard
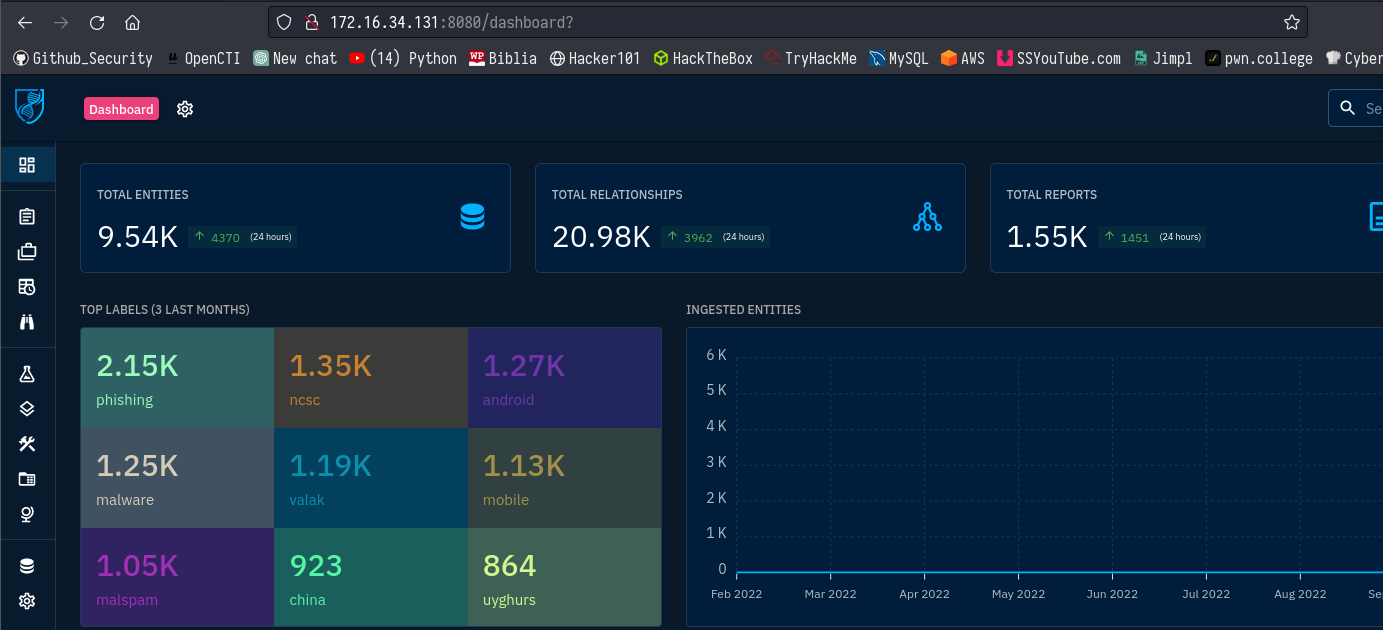
Analyze
In this part different reports are displayed from the connectors we added before. Example of report is the Raspberry Robin’s botnet second life.
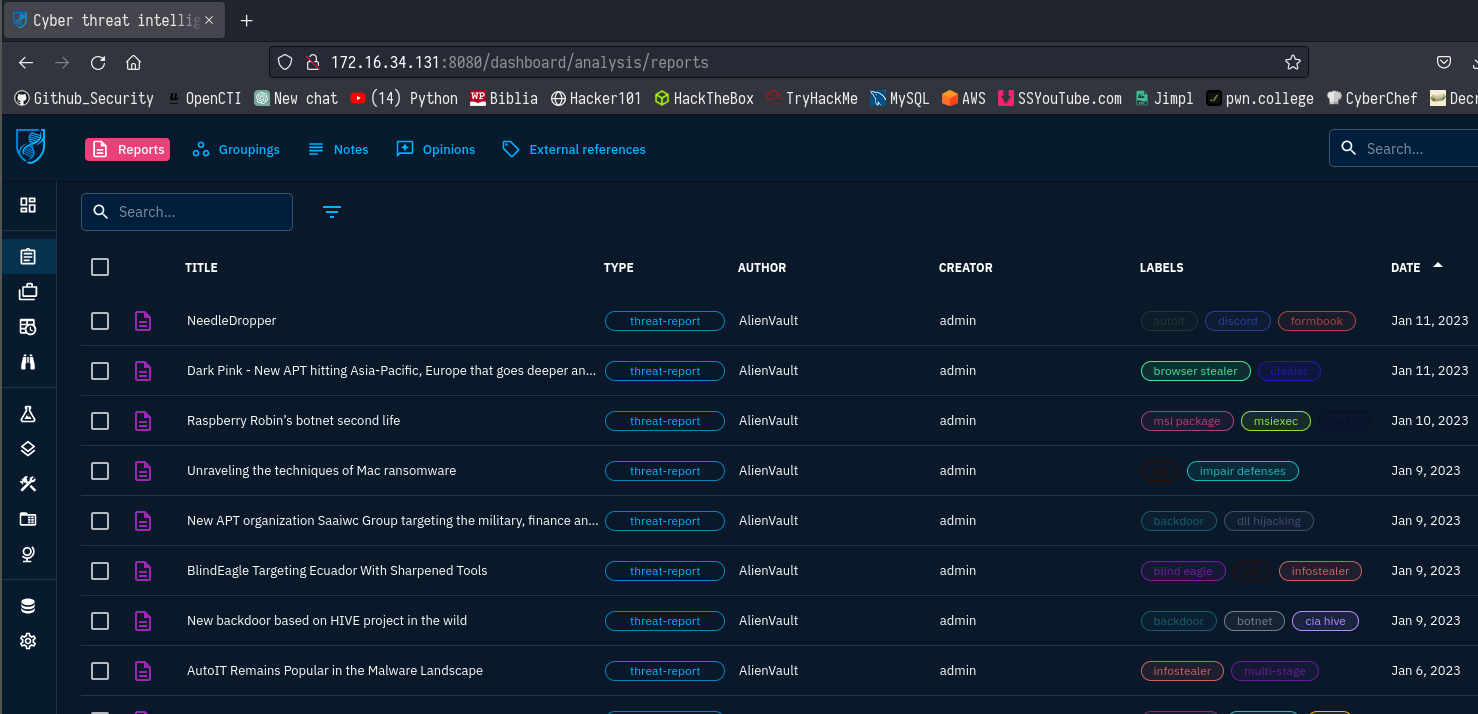
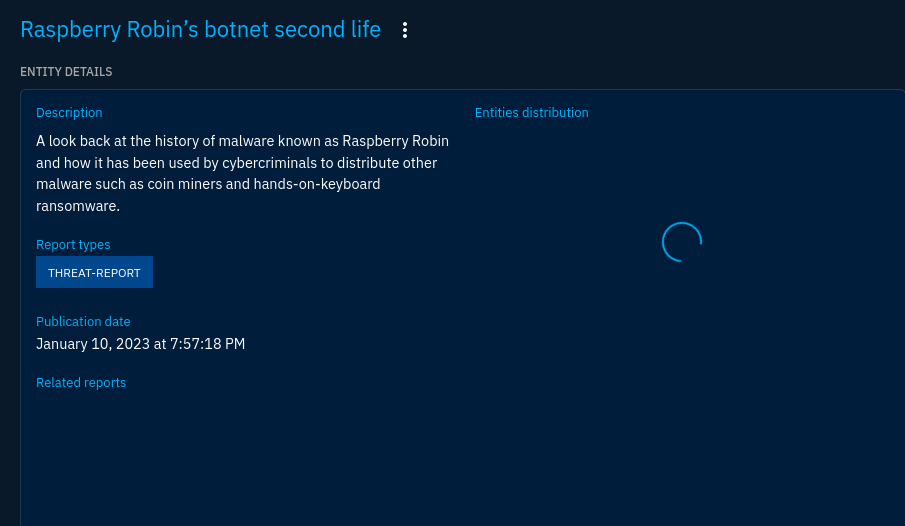
Reading the report
You can click this report to see its description and date it was published.
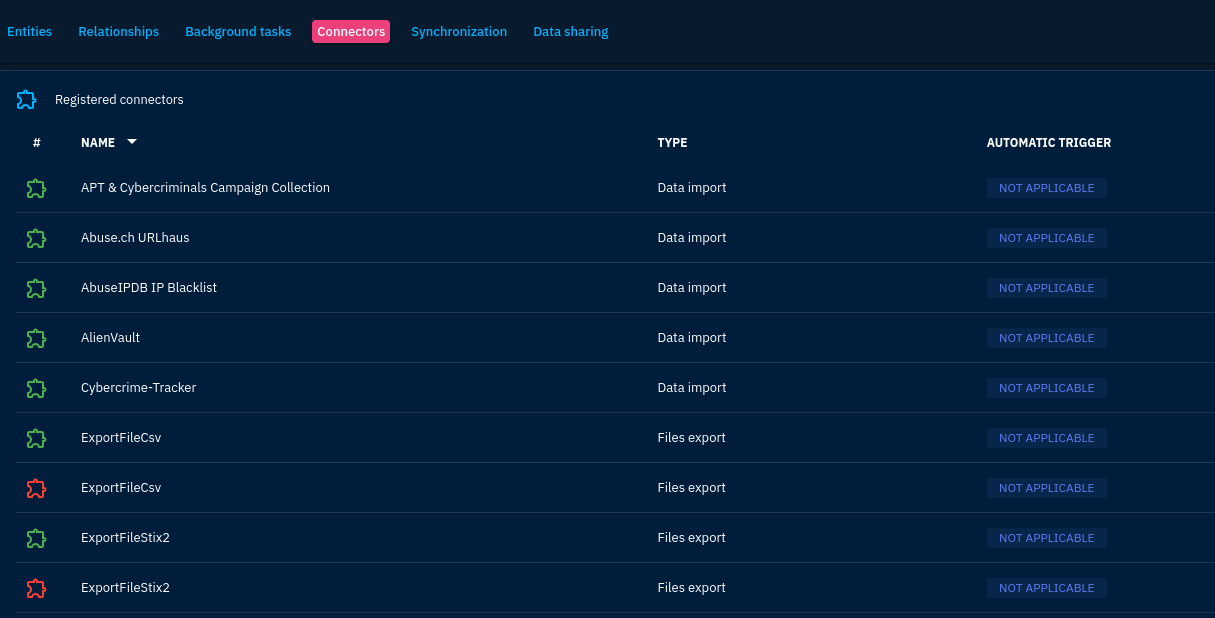
Connectors
You can clicked on database at bottom left of side bar and then connector. One of the connector added is AlienVault and it is shown below.
Thanks for reading.
The End.