
This is the part two of android pentest, part one documentation is found here.
In this document I will show how to intercept android application traffics using burpsuite. In previous post I showed how to capture traffics from web browser but using same methodology on intercepting android apk wont work.
To achieve some modifications must be done and to do this there are steps to followed as explained below:-
Phase 01 - Install Android Application.
I will continue where I ended on the first post and all steps on it will be applied here. To achieve this I will use instagram for android as case study. I will download and install from google-playstore.
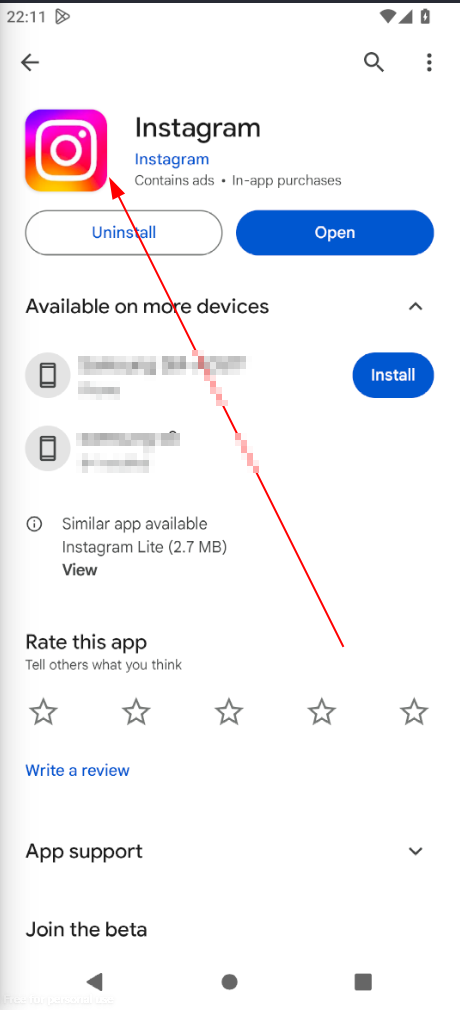
After installing I will try to open and check if requests are forwarded to burpsuite
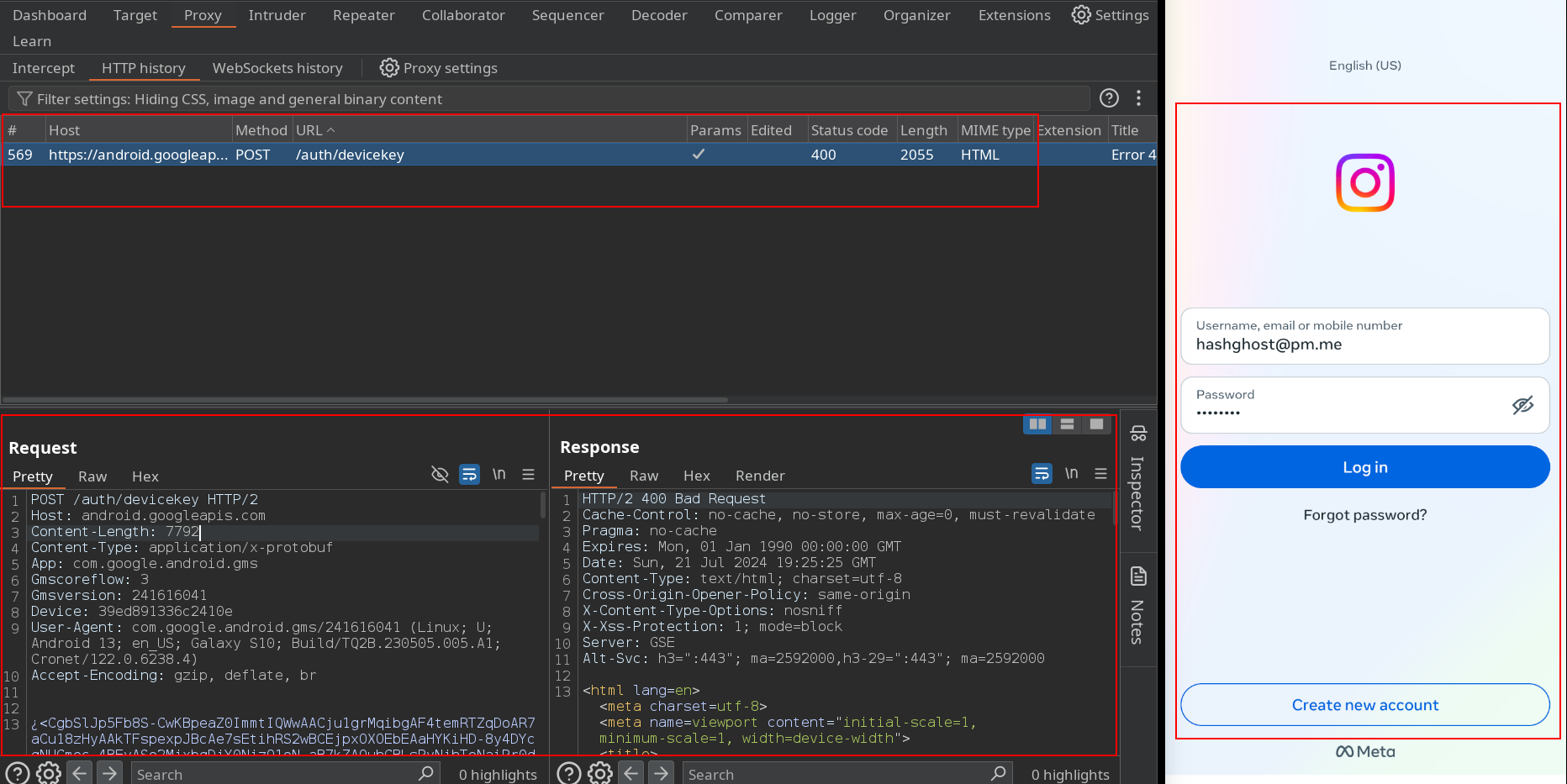
No request has been captured with burpsuite, this is because of SSL Pinning. Instagram and many other applications use SSL Pinning to prevent interception of their HTTPS traffics. This means that even if someone intercept the traffic with Burp Suite, won’t be able to read them because the app is expecting a specific SSL Certificate. For more reference about it you can check indusface or here.
Phase 02 - SSL Bypass.
To bypass SSL Pinning and intercept HTTPS traffic as plain on burpsuite can involve some techniques such as patching the app, using Frida, or applying a tool like SSLUnpinning. But in this post I will use frida.
Install Frida Tools.
To install frida this simple command can be used. This will be used on Linux machine and I run as client.
1
pip3 install frida-tools
Sometimes pip3 fails because it can not create path but to avoid this I can set path manually or use sudo although it is not recommended.
After that step frida will be available on machine.
Download Frida Server from github.
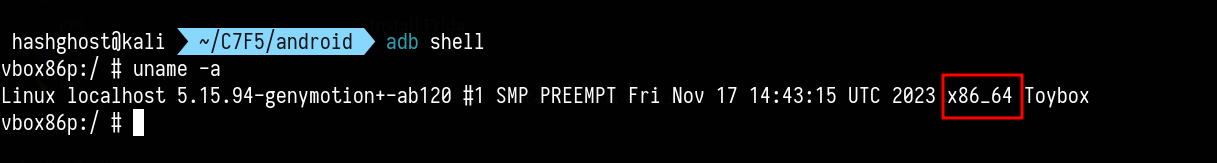
For this part to be successful I need to know my android architecture and since am using genymotion this will be quite simple with uname command.
1
2
3
└─$ adb shell
vbox86p:/ # uname -a
Linux localhost 5.15.94-genymotion+-ab120 #1 SMP PREEMPT Fri Nov 17 14:43:15 UTC 2023 x86_64 Toybox
All I need here is this value x86_64 android architecture as shown on screenshot below:
 After having this then I will visit frida on github and download it.
After having this then I will visit frida on github and download it.
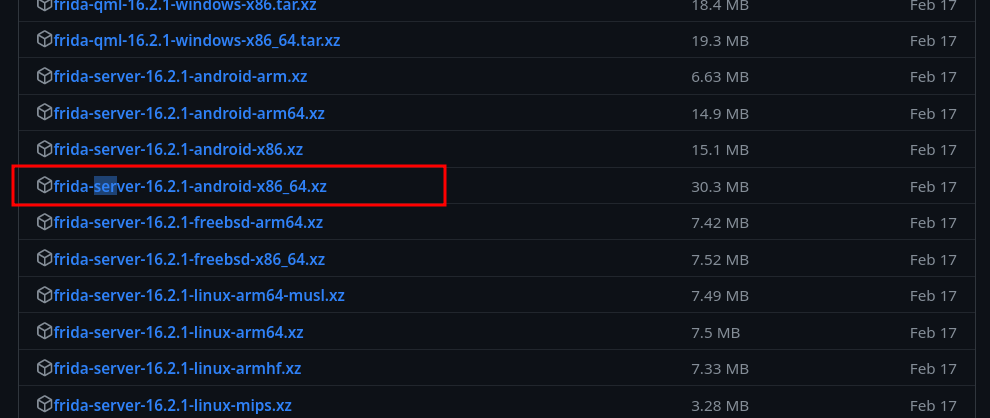
will extract zipped file and upload it to android device.
1
└─$ 7z x frida-server-16.2.1-android-x86_64.xz
Since this name is very long then I will rename it to frida-server
1
└─$ mv frida-server-16.2.1-android-x86_64 frida-server
Upload Frida-Server on android device.
The next step is to have frida-server on mobile device and to do this this simple command is used.
1
2
└─$ adb push frida-server /data/local/tmp/
frida-server: 1 file pushed, 0 skipped. 181.7 MB/s (108616536 bytes in 0.570s)
Now this should execute on the device then I will give it execution permission.
1
└─$ adb shell "chmod 755 /data/local/tmp/frida-server"
SSL unpinning
Before this step I need to know the name of the binary and this can be done through playstore on google.
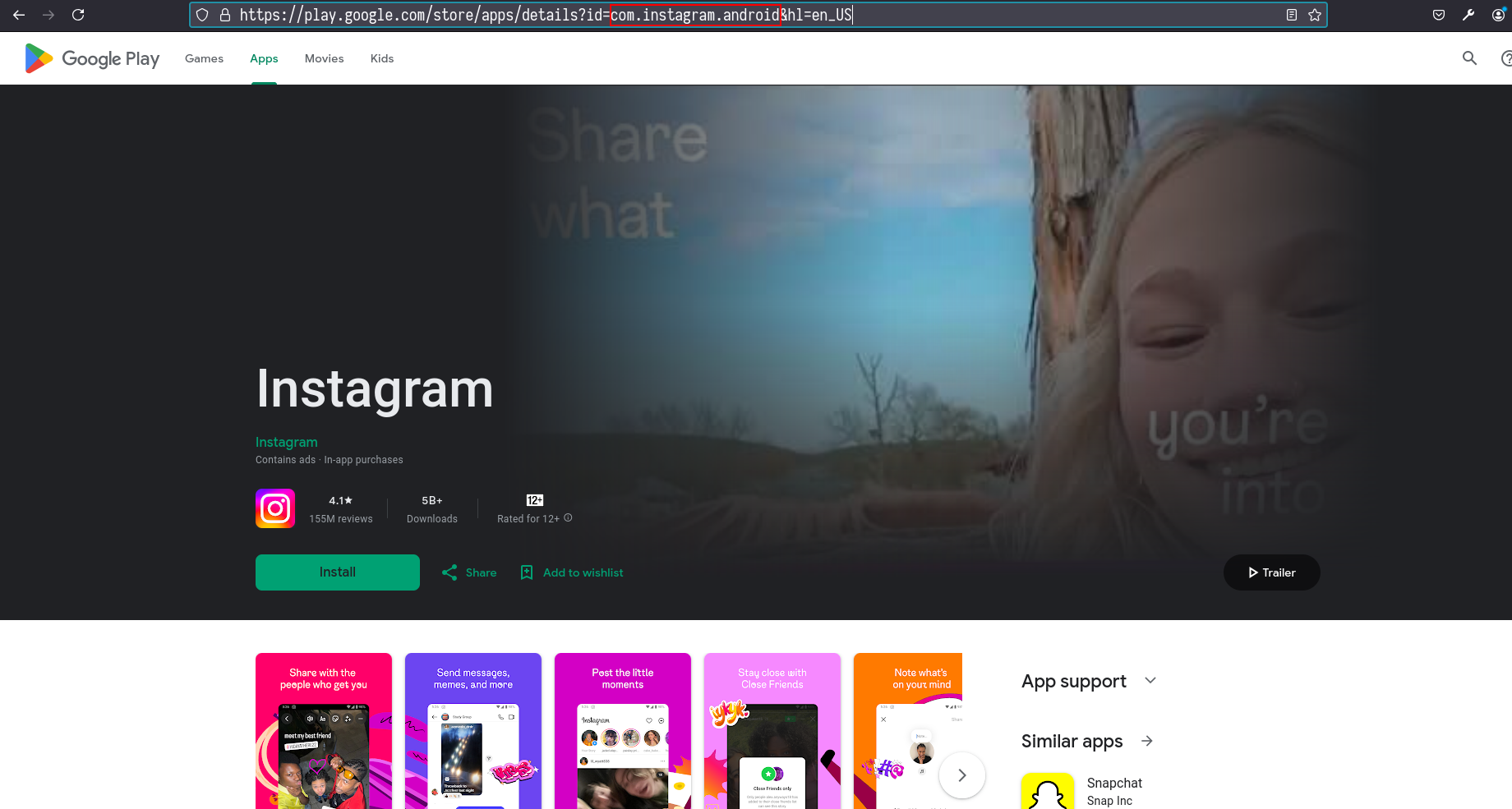
Then Instagram binary will have a name of com.instagram.android. Now I need a javascipt file for multiple unpinning this file is found on this link but for this lab I will be using this.
All together.
Download script from Eltion.
1
└─$ wget https://raw.githubusercontent.com/Eltion/Instagram-SSL-Pinning-Bypass/main/instagram-ssl-pinning-bypass.js
Run server on android phone emulator
1
└─$ adb shell "/data/local/tmp/frida-server &"
Shift frida to capture usb/ mobile phone
1
└─$ frida-ps -U
Run frida with javacript unpinning file if you have saved it manually or you can as the posts explains.
1
└─$ frida -U -l ./instagram-ssl-pinning-bypass.js -f com.instagram.android
Result
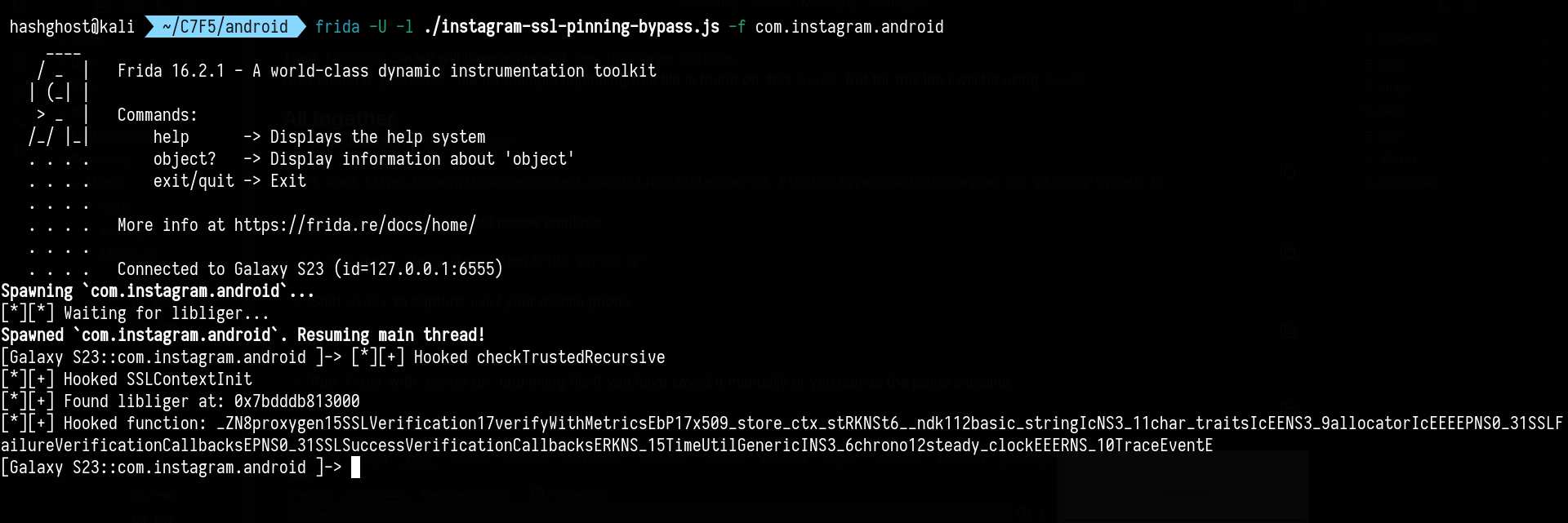
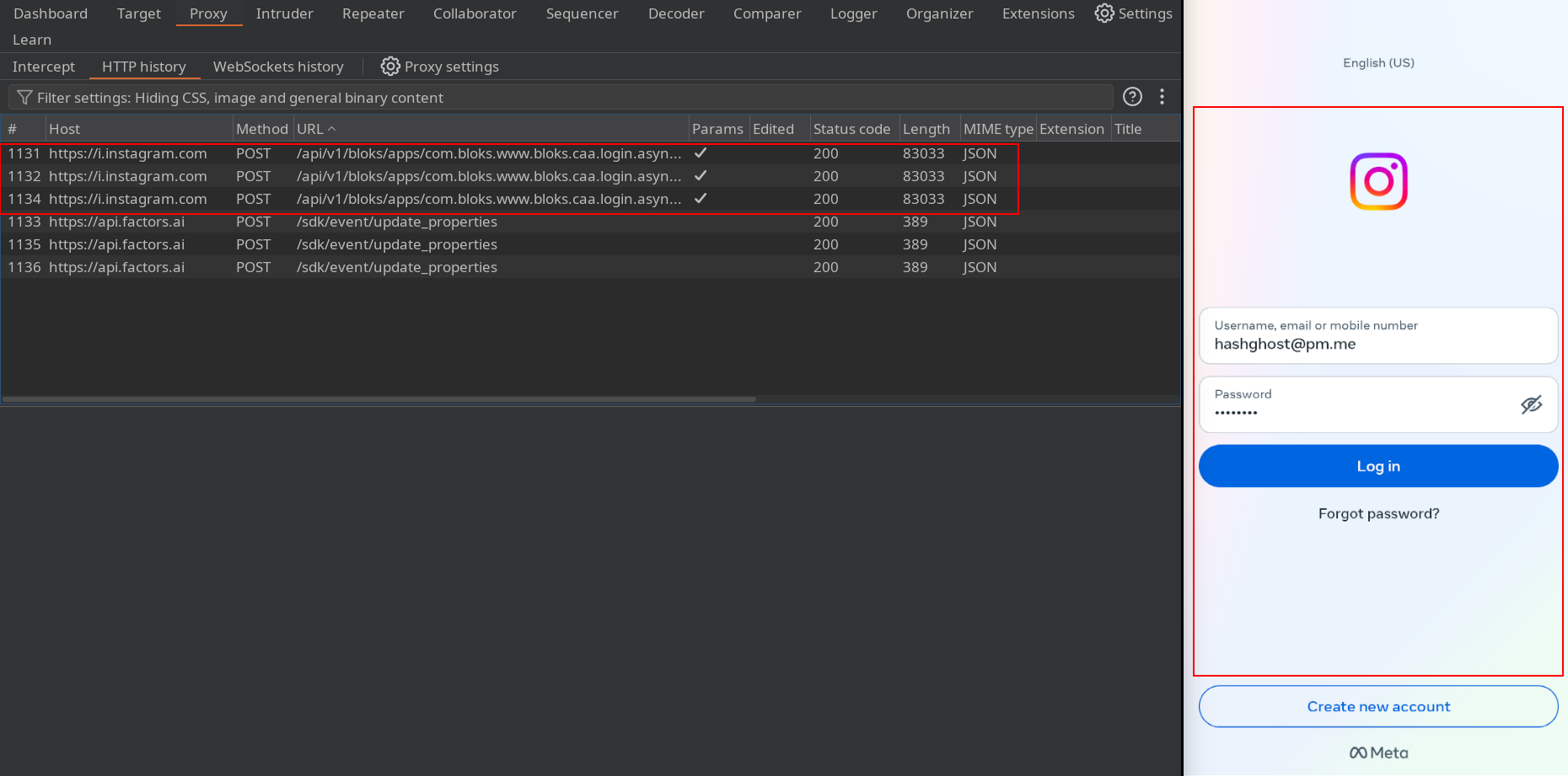
Now Instagram traffics will be captured with burpsuit
The End.
1
Mungu Nisaidie