
Mobile application penetration test is similar to web application pentest but it can sometimes be trick to set an environment to perform this action. In this post I will share all necessary steps required to set an environment for android applications penetration test.
Prerequisites
In order to have a replica of this setup you have to install the followings:
- Linux Machine - For this setup I will use kali Linux but any Operating System can be used.
- adb
- Genymotion or android phone.
- Virtualbox.
- Frida.
- Burpsuite.
Tools Installation.
Am assuming you have Linux distribution of your choice and proceed with installation of other tools.
Adb
This tool can simply be installed by only type the following:
1
└─$ sudo apt install adb
Virtualbox
All required steps to install virutalbox on Kali Linux can be found this link
Genymotion
This will help to provide a virtual phone which will be used during emulation of different android applications. To download it use this link and select your installation file according to your OS but in this post I will use linux_binary.
1
2
3
4
└─$ mv genymotion-3.6.0-linux_x64.bin /opt && cd /opt
└─$ mkdir genymotion && mv genymotion-3.6.0-linux_x64.bin genymotion && cd genymotion
└─$ chmod +x genymotion
└─$ ./genymotion
If it is your first time to use genymotion you will have to register for new free account otherwise you can login.
Frida
To install frida tool is very simple you can use this link or simply you can use this simple command
1
└─$ pip install frida-tools
Sometimes this fails but all you have to do is to use it with privileged user or you can use sudo because it can fail to create path under low privileges.
1
└─$ sudo pip install frida-tools
Up to now I have all required tools to start pentest, burpsuite is pre installed in Kali so no need to reinstall it unless you have a licence and upgrade it to pro version.
Hands on no more stories.
Installation and setup of virtual phone.
To perform this action we need a phone a real one or virtual phone, I will use virtual phone from genymotion through the following steps:
Download latest phone of your choice.
Follow pictures below to install your new android application.
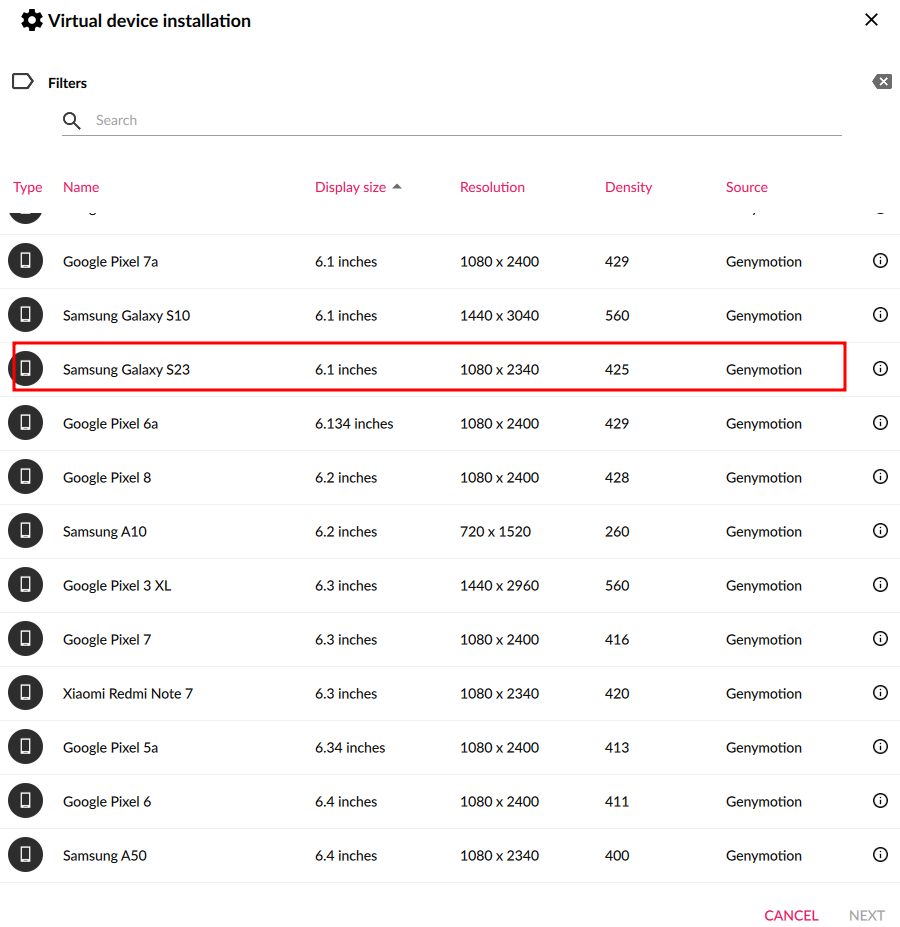
Select phone of your choice on my side I will choose samsung s23 but you can pick any.
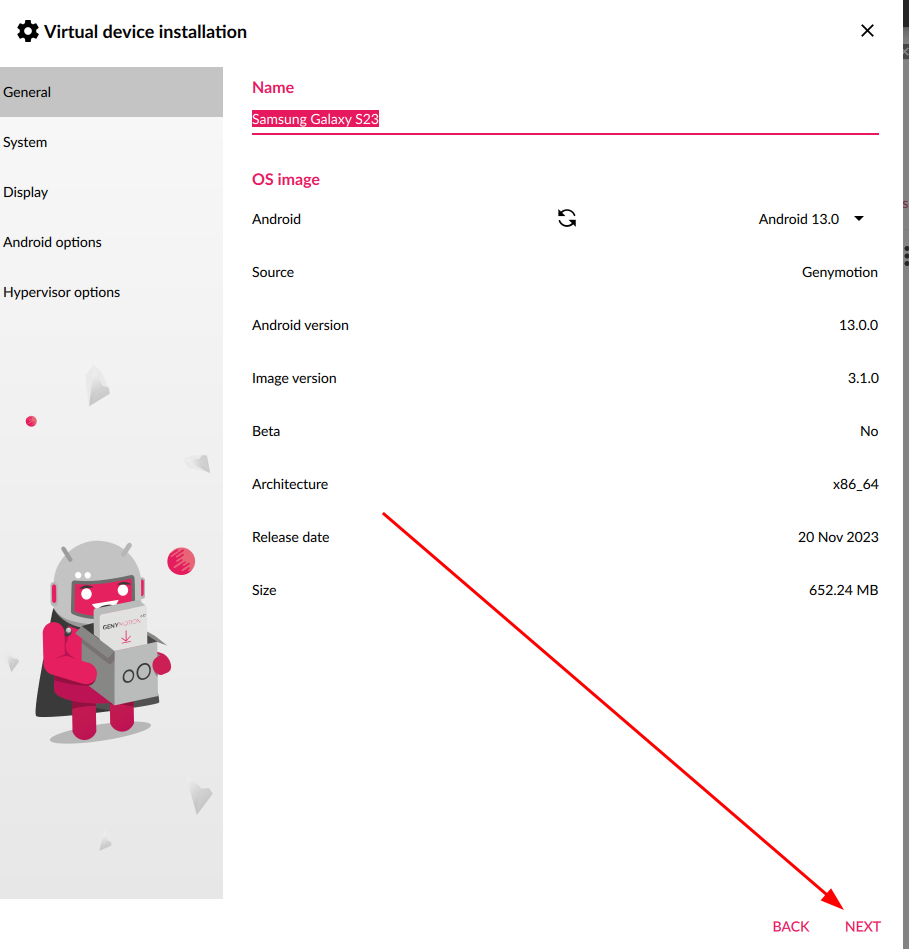
You can modify some few things including mobile name and also specs of mobile phone but some requires a licence but you can leave all the defaults and it will work fine.
Now you will have phone which will open like this.
Install Playstore on virtual phone and sign in with you google account.
Click a button on your virtual phone named Open GApps and click accept to download it.
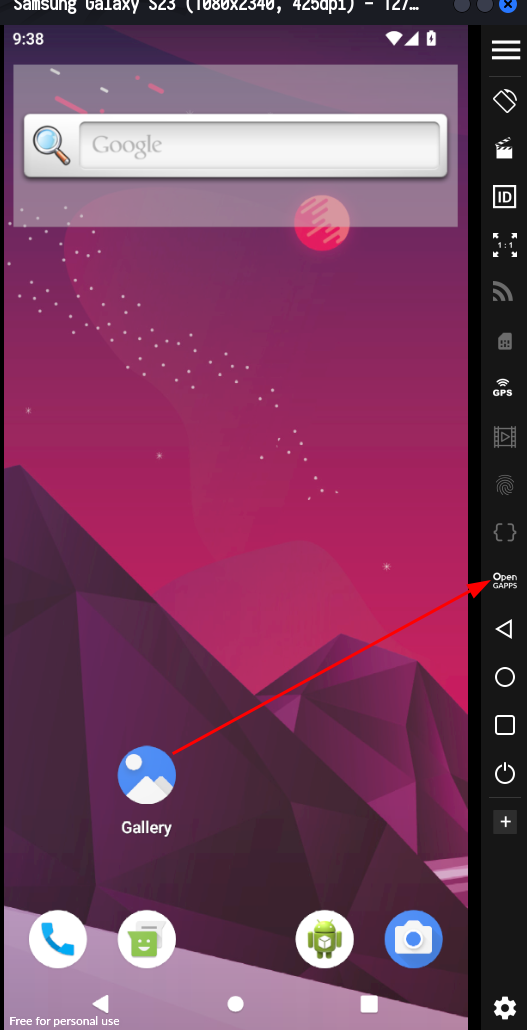
After installation of GApp pop window will appear click restart now to restart your virtual mobile phone.
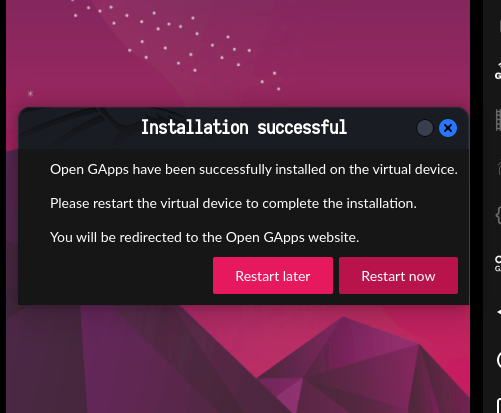
After rebooting mobile phone now playstore will be available and can be accessible.
Now sign in with your google account to have access playstore so that you can download different applications.
Now I have full access and I can download any application of my choice from the store.

Install Burp Certificate and Configure proxy.
There are two methods to install burp certificate. One is simple and clear which involves much user interaction and the second one involves more of commands. I will explain both ways here starting with straight one:
First Method
- Start
Burpsuiteand then run the following commands:1
└─$ curl localhost:8080/cert -o cert.der
The above command will download certificate from
burpsuiteand save it ascert.der. I will download this on my device (Android). The location to install is the same but reaching that path may differ, On this article I am usinggoogle pixel 4aso I will list the path to install.- Go Settings -> Security & Privacy -> More Security Settings -> Encryption & Credentials -> Install a Certificate -> CA Certificate
- Then there will be a warning click
install anyway - The downloaded certificate will be sen here click it and continue with Setting proxy on mobile phone
Second Method
- Start
Burpsuiteand then run the following commands:1
└─$ curl localhost:8080/cert -o cert.der
The above command will download certificate from
burpsuiteand save it ascert.der. - Convert installed file to
permformat and rename it.1 2
└─$ openssl x509 -inform der -in cert.der -out burp.pem └─$ openssl x509 -inform PEM -subject_hash_old -in burp.pem
This will result to the following:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
9a5ba575 -----BEGIN CERTIFICATE----- MIIDqDCCApCgAwIBAgIFANd0C+8wDQYJKoZIhvcNAQELBQAwgYoxFDASBgNVBAYT C1BvcnRTd2lnZ2VyMRQwEgYDVQQIEwtQb3J0U3dpZ2dlcjEUMBIGA1UEBxMLUG9y dFN3aWdnZXIxFDASBgNVBAoTC1BvcnRTd2lnZ2VyMRcwFQYDVQQLEw5Qb3J0U3dp Z2dlciBDQTEXMBUGA1UEAxMOUG9ydFN3aWdnZXIgQ0EwHhcNMTQxMjIwMTAxMzU1 WhcNMzMxMjIwMTAxMzU1WjCBijEUMBIGA1UEBhMLUG9ydFN3aWdnZXIxFDASBgNV BAgTC1BvcnRTd2lnZ2VyMRQwEgYDVQQHEwtQb3J0U3dpZ2dlcjEUMBIGA1UEChML UG9ydFN3aWdnZXIxFzAVBgNVBAsTDlBvcnRTd2lnZ2VyIENBMRcwFQYDVQQDEw5Q b3J0U3dpZ2dlciBDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAJIV cR2mQGz/IrlgvqTskT1z2d8+CJ2zKVwH0cZ+qYpMLe89yEa9kltDtDjYsTs4DXUE qYpyXqEhjdgf7Ti4/WH8Z4TG9ci2cB53pueWIjz+eWozC7QTIRPORqBIAEqEYAlY vdf4DgewbLxaqUUh+mqkaAGmsAJ+OrDIlBZmJEra5Y7oXFUYaeGVzmRp5LywD0vj FurEUVS4HJQ+7cXAdYisqnAF9FReQ6VkccpesdHtWwCjZdWzrhadvqpkwl2rEMO2 ZaR7Xj+NJfcpxW5N7qxKAsLFarRjFE5zRAPNq+Fr3NKBzFPUbVuxXXiwCNItpShw uNN8sLXEyJ66HMKjBz8CAwEAAaMTMBEwDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG 9w0BAQsFAAOCAQEAFcjfdaolla2fCCSHpRBKWG/d5hPUbAYOxpCEh1Ud/uZJvIZB mYTgl4iA2bOHzh9PF/2xMyR/AoXQMbBhljL0ES0+4KI8i8+Fb0X5XEfhOwei7C/R nnuYKm3uGQ+KWti/NVPZn4ty5CHX9J6d1dxlb4keBGLmfycOOWMY1mVAKpsJQ1xR Ualu7kGgI6nOb06813vjIPRlr/dpZpk938mMgKx0xxkLYs+mOAErmNFP6D3cEK45 U5f1yl5EZVzQtAdhnAJhk2QQQO6rxXr2mBASLSC3JUJFhCicIAA+VTnzmHt0ThUG lJ7kWVhQMAbGvckgk2NMiu4AMo90oqwOLd1vGw== -----END CERTIFICATE-----
But name of certificate should be md5sum of subject which can be seen as the fist line with these characters 9a5ba575. Now to rename certificate use the following command
1
└─$ mv burp.pem 9a5ba575.0
- Install Certificate in mobile device.
To install burpsuite certificate follow this trail Go to Settings -> Security -> More security settings -> Encryption & credentials -> Trusted credentials. After all these look for Portswigger you wont see it because it is not there and has not uploaded yet. To upload it use the following command:
1
2
3
└─$ adb push 9a5ba575.0 /system/etc/security/cacerts/
9a5ba575.0: 1 file pushed, 0 skipped. 3.0 MB/s (1330 bytes in 0.000s)
adb: error: failed to copy '9a5ba575.0' to '/system/etc/security/cacerts/9a5ba575.0': remote couldn't create file: Read-only file system
This will result to error because the file system is read only but since this emulated device is rooted then it can be modified and mounted through the following commands:
1
2
3
└─$ adb shell
vbox86p:/ # mount -o remount,rw /
vbox86p:/ # exit
Now upload again it will work.
1
2
└─$ adb push 9a5ba575.0 /system/etc/security/cacerts/
9a5ba575.0: 1 file pushed, 0 skipped. 11.7 MB/s (1330 bytes in 0.000s)
No more error. Now check again if certificate has been uploaded to your virtual mobile phone.
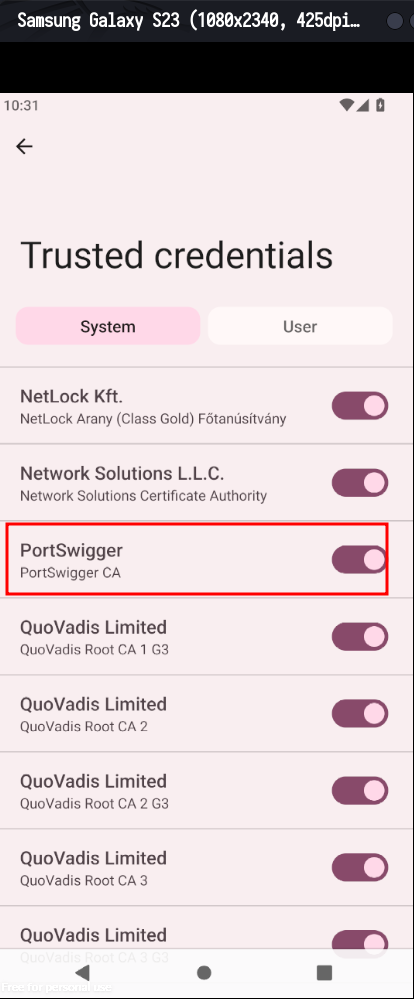
Setting proxy on mobile phone
Since am using wifi network then I will configure my wifi IP as proxy.
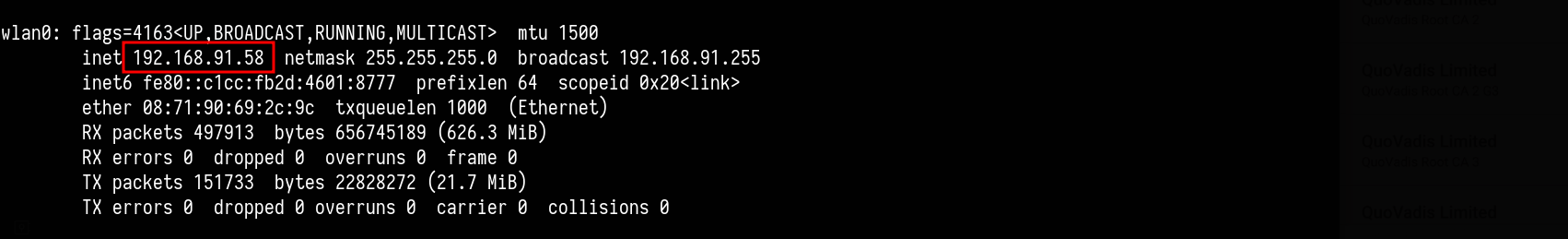
To add this on mobile phone I will use the following command:
1
└─$ adb shell settings put global http_proxy $(ifconfig | grep wlan0 -A 5 | head -n 2| tail -n 1| awk '{print $2 }')
This command will take only the IP address from wifi interface and configure it as proxy in mobile phone. To unset this proxy setting you can use the following command:
1
└─$ adb shell settings put global http_proxy :0
One more thing is to configure burpsuite to allow requests from all interface rather than only loopback to this you can go to burpsuite and do the followings:
Go to Proxy Settings -> And follow below pictures
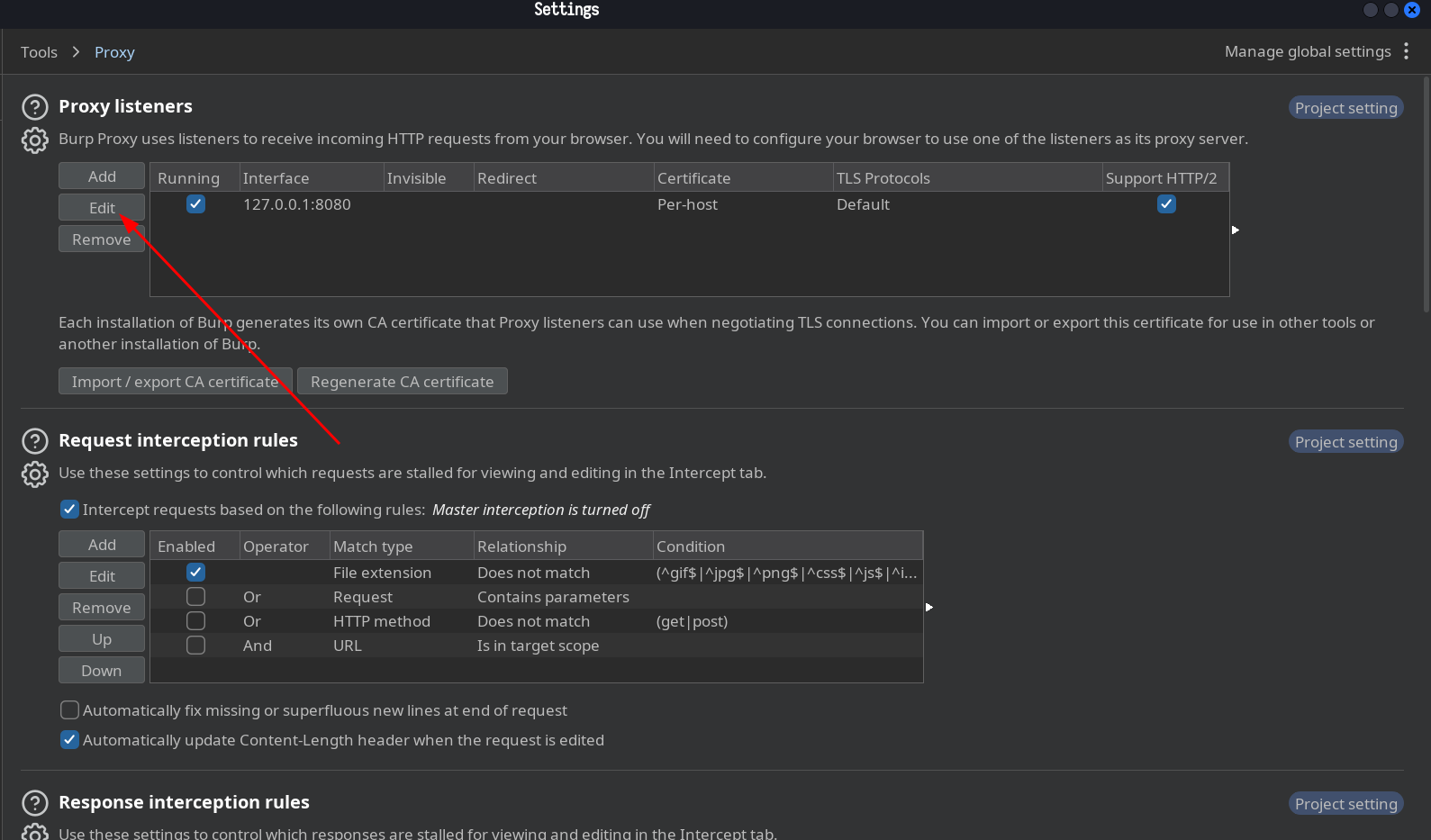
Select all interfaces and click ok button if pop window appear then click yes to accept changes.
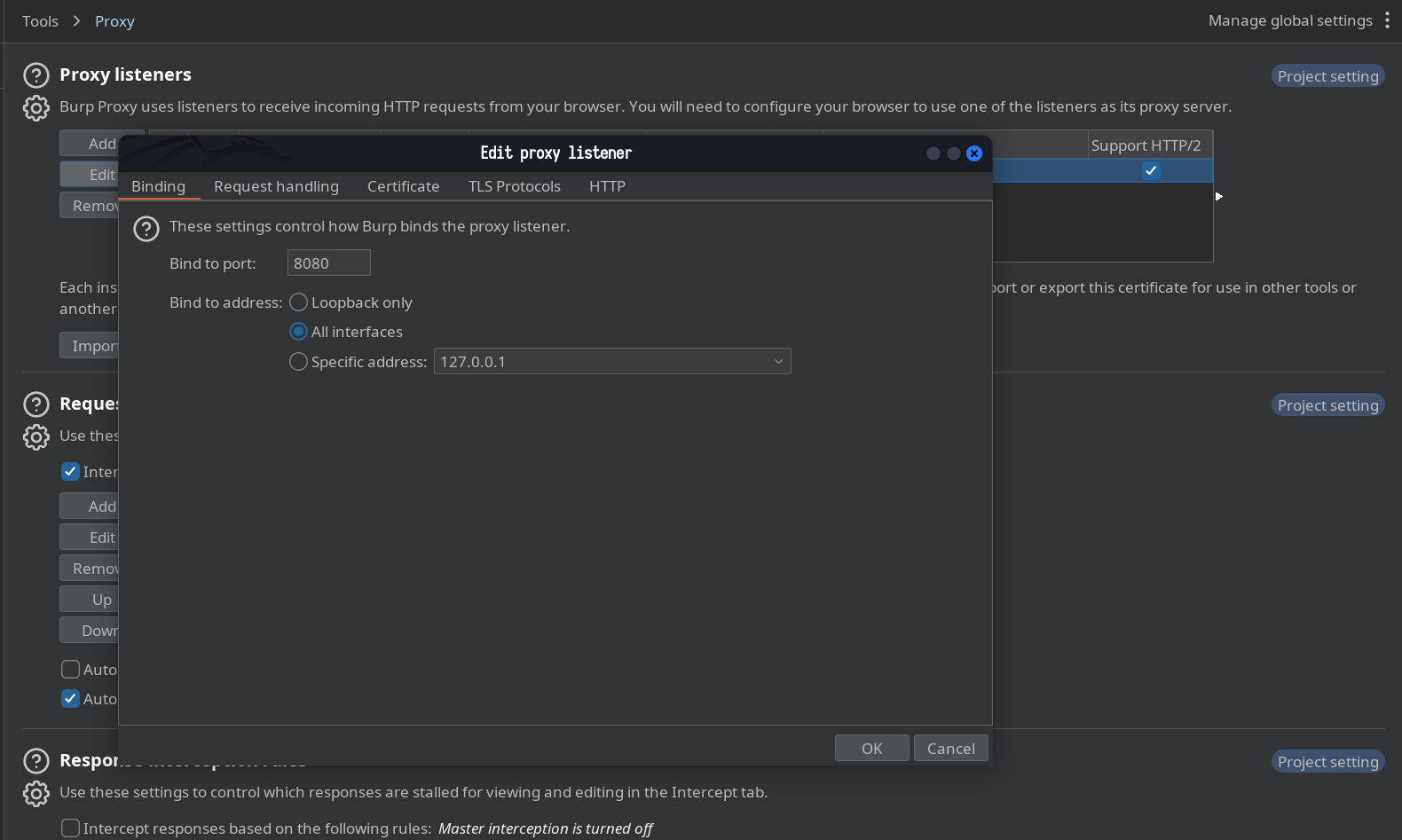
After finish setting then it will now appears as follows:
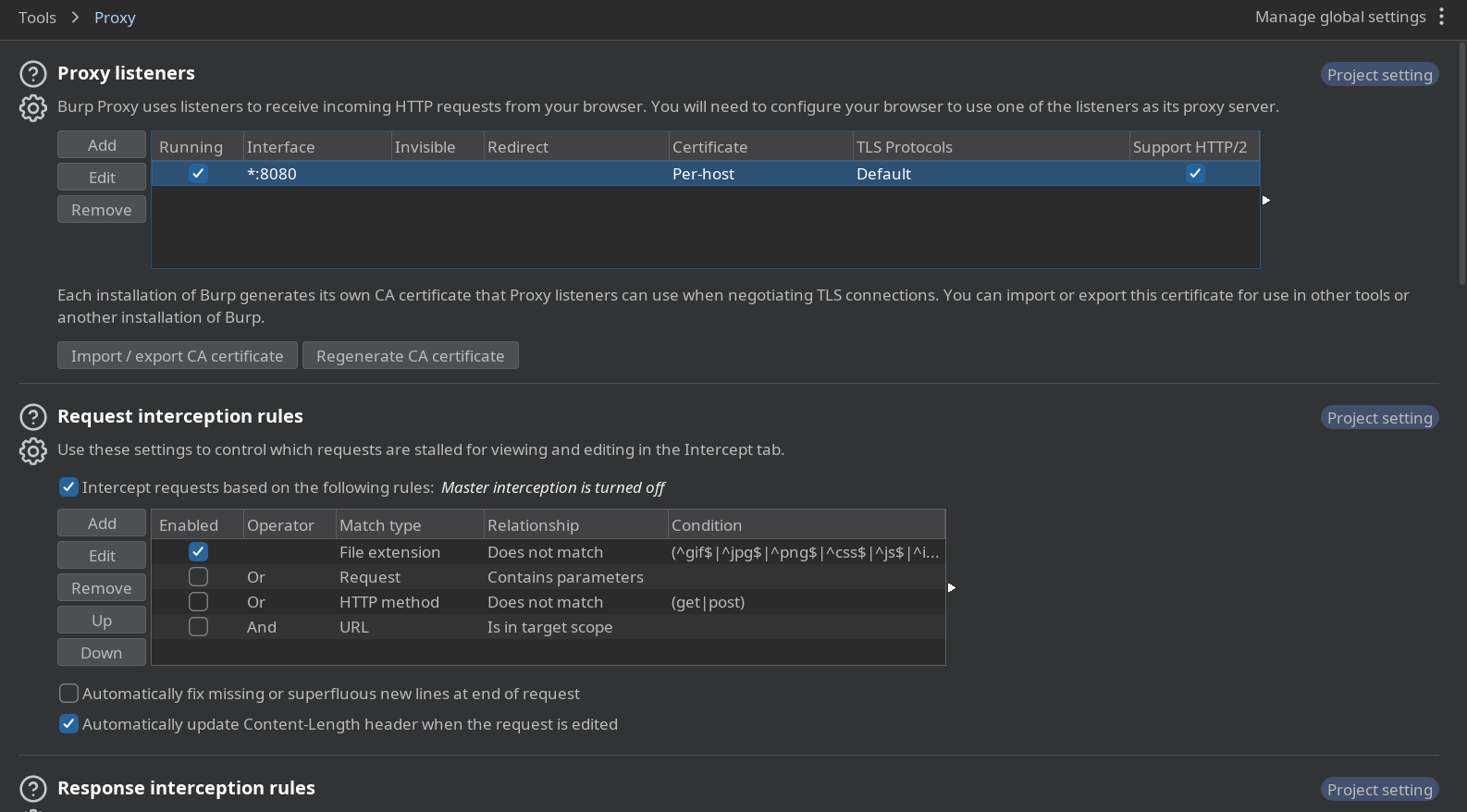
Test if proxy is configured well
I will use udom university as an example. Below image will show before sending request to web application by using mobile phone.
Now I will show after sending request to google servers about The University of Dodoma.
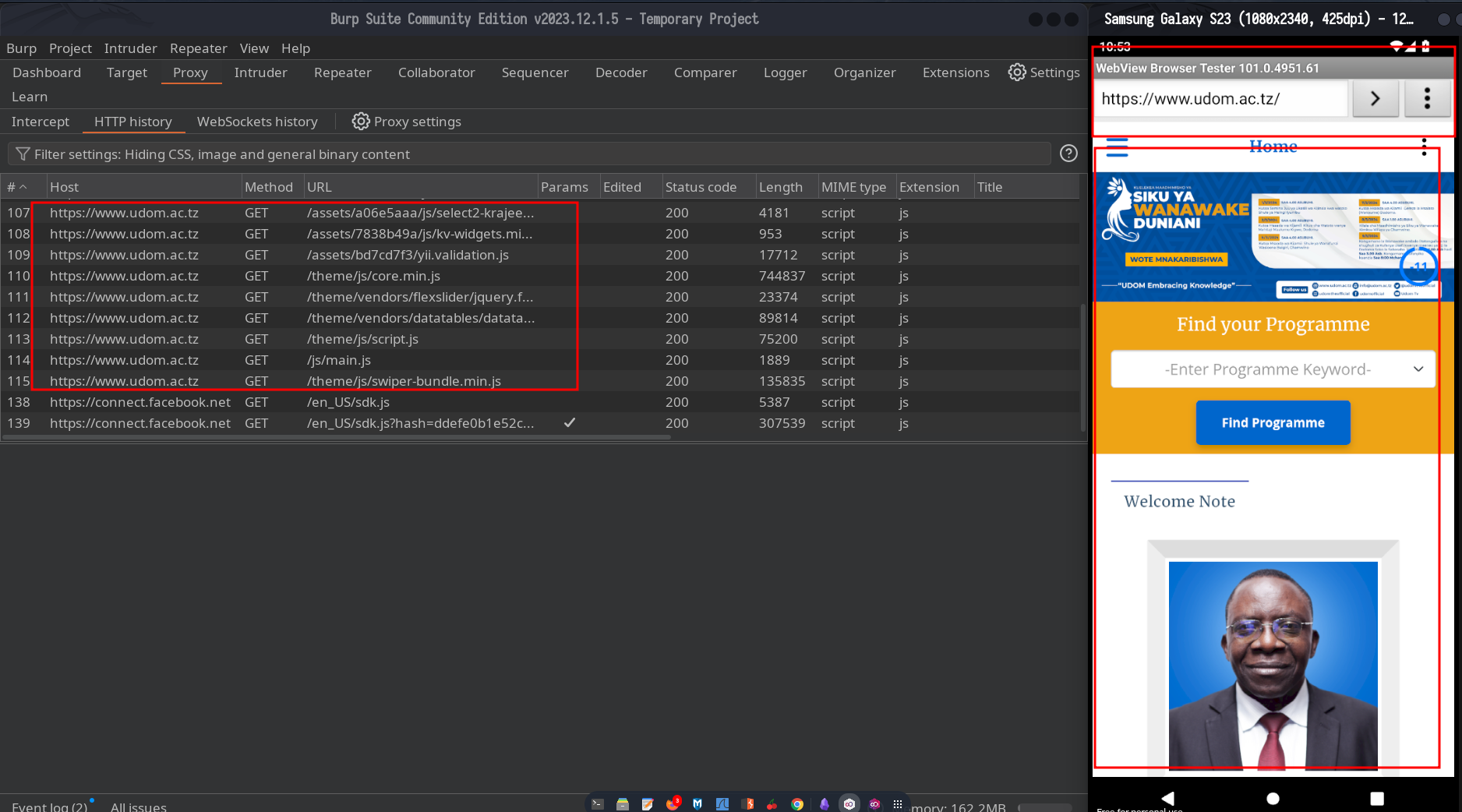
Now I can see all traffics on burpsuite and intercept them for more researches.
This document has been long enough and I have decided to prepare another one as part two which will cover bypass ssl pinning and capture traffics from specific android application. The part two can be found here
1
Mungu Nisaidie